
Reconnaissance
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=Escape
| Not valid before: 2025-06-01T14:31:21
|_Not valid after: 2025-12-01T14:31:21
|_ssl-date: 2025-06-02T16:24:40+00:00; -2s from scanner time.
| rdp-ntlm-info:
| Target_Name: ESCAPE
| NetBIOS_Domain_Name: ESCAPE
| NetBIOS_Computer_Name: ESCAPE
| DNS_Domain_Name: Escape
| DNS_Computer_Name: Escape
| Product_Version: 10.0.19041
|_ System_Time: 2025-06-02T16:24:35+00:00
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Initial Access
Connecting to RDP via xfreerdp3 /v:<IP> /sec:'nla:off' shows a message concerning the usage of user KioskUser0 without a password. Notably the confirm button is in Korean.
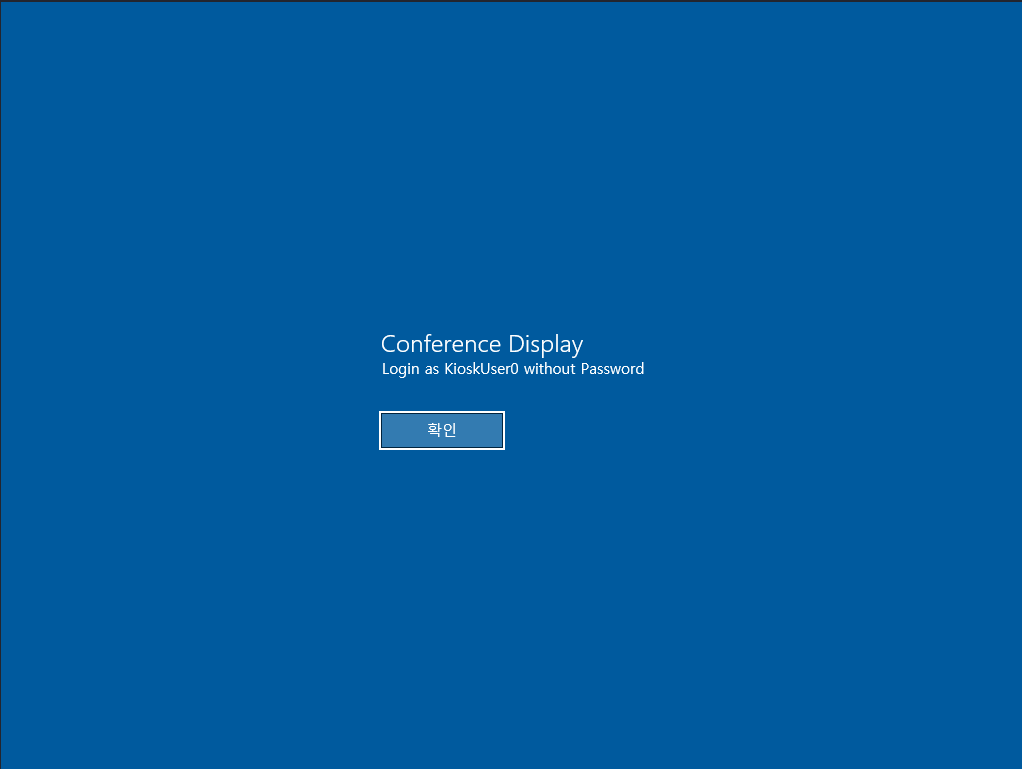
Clicking on the button directs me to the actual login prompt where I sign in with KioskUser0. Using ALT+TAB I can see that the application is running msedge.exe and killing the process results in another start of the same view.

Privilege Escalation
Using the windows key opens the start menu and I can search for msedge to start another browser. This time the interface is present and shows the on-boarding view in Korean that I click through.
By navigating to file:///C:\ I can start browsing the file system and collect the first flag on the Desktop.
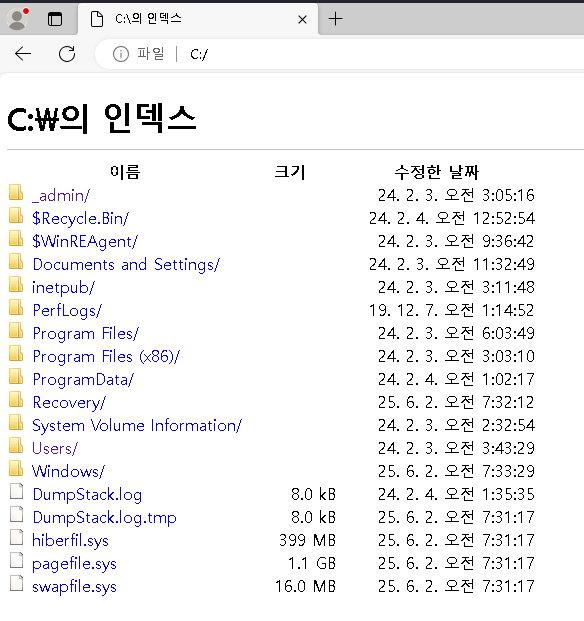
In order to gain a shell, I browse to C:/Windows/System32 and download cmd.exe. That drops the binary into the Downloads folder but executing it results in an error message. Since a lot of the programs seem to be restricted I decide to rename the binary to msedge.exe and this let’s me run it1.

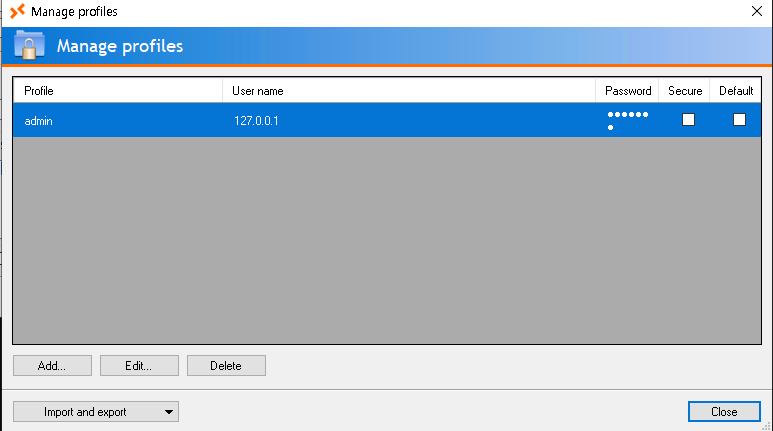
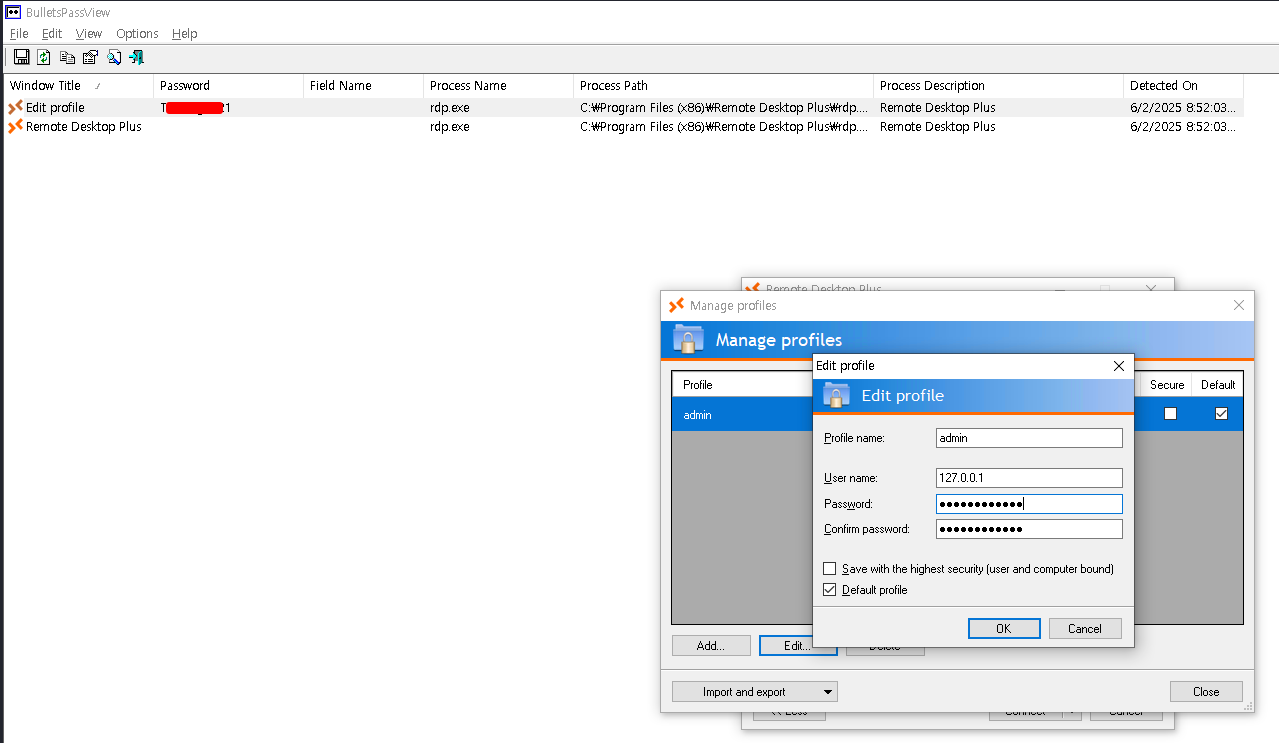
On the root of the file system there’s an interesting folder called _admin that contains credentials for Remote Desktop Plus, but the password for admin is encrypted.
<?xml version="1.0" encoding="utf-16"?>
<!-- Remote Desktop Plus -->
<Data>
<Profile>
<ProfileName>admin</ProfileName>
<UserName>127.0.0.1</UserName>
<Password>JW<REDACTED>Wc=</Password>
<Secure>False</Secure>
</Profile>
</Data>I can start the application in C:\Program Files (x86)\Remote Desktop Plus\rdp.exe and import the profiles.xml after copying it to the users Downloads directory.
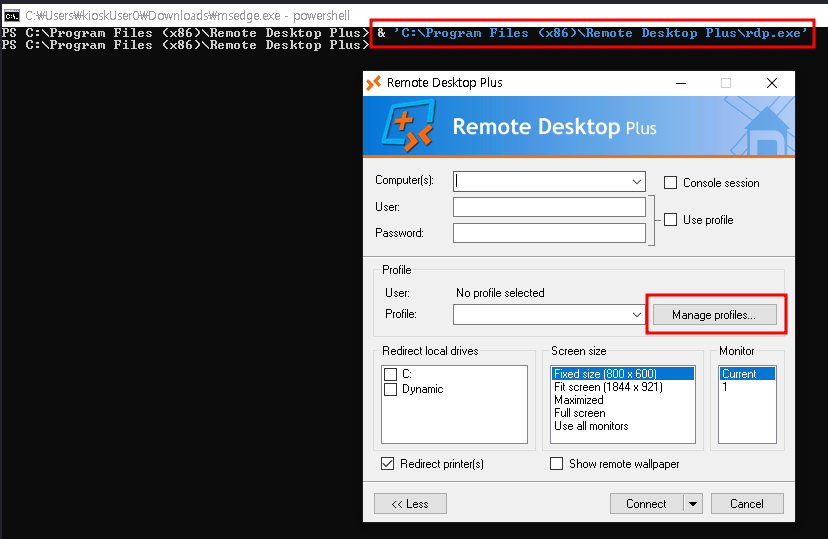
Unfortunately the application only displays dots instead of the password and there’s no option to deobfuscate it.
Searching for options to read that password finds BulletsPassView that claims to retrieve passwords from standard text-boxes. I download the binary and the accompanying chm file and transfer it over to the target through SMB. Running it displays the password T<REDACTED>1 for the admin user.
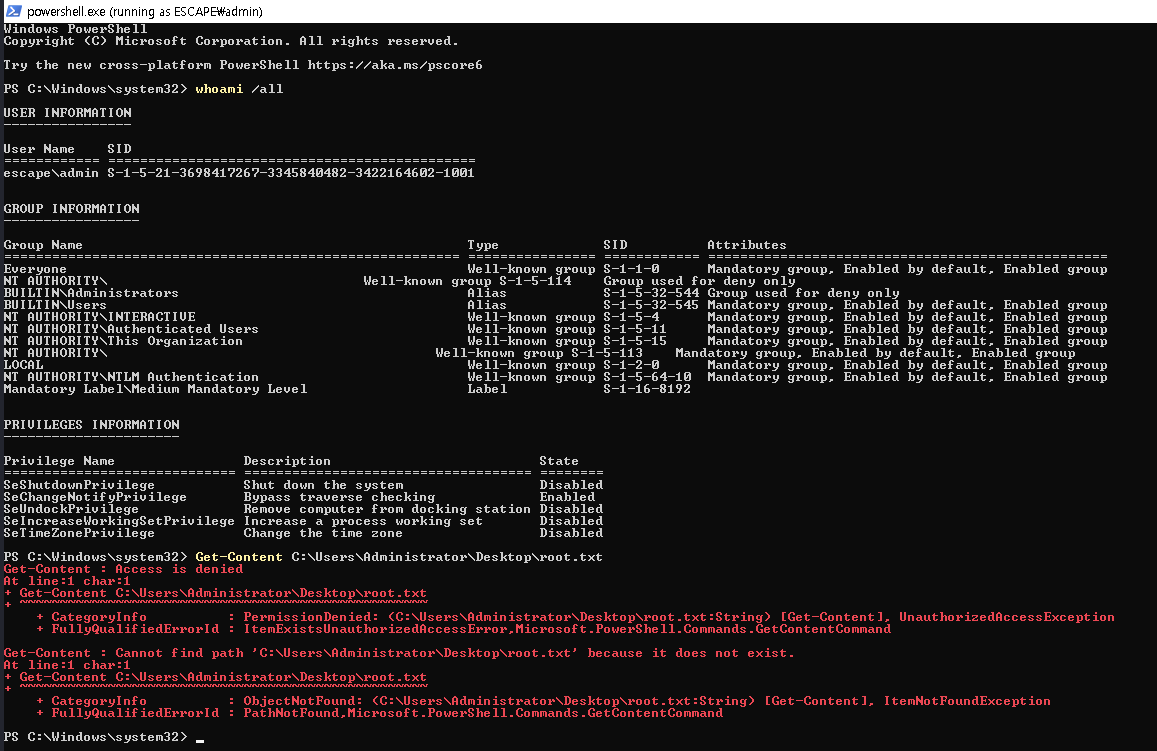
By using runas I spawn a new PowerShell window as admin user and checking the privileges with whoami /all shows that this account is part of the Administrators group.
PS > runas /user:admin powershell.exe
Enter the password for admin:
Attempting to start powershell.exe as user "ESCAPE\admin" ...But that does not allow me to read the flag in C:\Users\Administrator\Desktop\root.txt since I’m still running in medium integrity and I’m therefore lacking real administrative privileges.
In order to elevate into a high integrity context, I’ll spawn a new powershell with the Run as Administrator option2. This shows the UAC prompt that I accept and spawns a new console window with full administrative privileges.
PS > Start-Process -FilePath "powershell" -Verb RunAsAttack Path
flowchart TD subgraph "Initial Access" A(RDP) -->|Hint on Login| B(Access as KioskUser0) B -->|Escape Kiosk mode by renaming cmd| C(Shell) end subgraph "Privilege Escalation" C -->|Deobfuscate Password in Remote Desktop Plus| D(Credentials for admin) D -->|Runas| E(Shell as admin) E -->|Run As Administrator| F(Administrative Shell) end
